-
Notifications
You must be signed in to change notification settings - Fork 4.6k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
HTTPS on macOS does not work running from the default ASP.NET Core Web App (MVC) template #27132
Comments
|
From @mkArtakMSFT on August 10, 2018 16:59 Thanks for contacting us, @sankra. |
|
What was the error in the browser? These errors in the server are expected if the client does not trust the server's certificate and aborts the connection. See https://blogs.msdn.microsoft.com/webdev/2018/02/27/asp-net-core-2-1-https-improvements/ for trust. |
|
From @sankra on August 10, 2018 17:23 Tried running the trust command again, but it said the cert was already trusted: Here are the screenshots of various browsers trying to access the default site: Safari: Chrome: Firefox: |
|
Interesting. I just noticed that last error "Cipher Suite negotiation failure". I found another report of this error at https://developercommunity.visualstudio.com/content/problem/297841/kestrel-failed-to-authenticate-https-connection-on.html @davidsh have you seen this with SslStream on Mac? |
|
This is an issue for me as well. My colleague with virtually identical setup does not have this issue so it seems to be something with my machine's configuration. Any clues on where to look next? The reproduction path is simple: Then debug through visual studio code 1.27.0 and the same error occurs (or dotnet run). I have tried various things to trust my dev certificate but can't figure out the magic key combination. |
|
cc: @wfurt |
|
I just did this @richardpineo and it works for me. I did I think there is possibility that you have some conflicting certificate for |
|
@wfurt Woohoo - that did it, thanks. I had deleted the localhost certificate in the system section, but not in the login. Really appreciate the quick help. |
|
I'm glad it worked @richardpineo. Can you please give it try as well @sankra? |
|
Excellent @wfurt , removing existing cert using Keychain Access and regenerating made the problem disappear. Thanks for your help 👍 |
|
Same problem here. Solved using: |
|
The solution to delete the certificates in the keychain and regenerate them does not work for me. Neither does to use the command line tool to clear the certificates and regenerate them. If I run the default generateed .net core WebAPI project i get the following It loads OK But if I hit the HTTPS endpoint ... |
That is very different error. Can please post packet capture? Wireshark or Did you try to access it wither with Safari or curl? |
|
Hi @wfurt, I am getting the same problem. Heres is the tcpdump |
|
I also tried to curl it |
|
To confirm, I did the following (on a mac - mac mojave) |
It seems like the client even cannot establish TCP. After sending SYN, server immediately resets connection. That generally happens when you try to connect to closed port or if listening application immediately crashes (or throws unhandled exception) It is also interesting that same sequence on IPv6 has different behavior. Can you post the actual pcap file @appsolutegeek ? (-w on tcpdump) Maybe @Tratcher can help with debugging server code. After running '--clean' did you check keychain and verified that there is no 'localhost' certificate? |
|
Issues with the server TLS parameters would trigger that kind of symptom. E.g. it connects, calls AuthenticateAsServerAsync, fails, and aborts the connection. I assume IPv4 is fine if you connect using http instead of https? |
|
Thanks, guys for the help here. Here is the netstat command |
|
The syntax should be As far as the netstat, it looks ok. I was wondering if there would be something lingering on port 5000. |
|
@wfurt sorry, here is the file with the syntax you asked for |
|
ALso confirmed, when i did a clean and checked the keychain - they were 0 localhost i think did the --trust and appeared 2 x localhost in the keychain |
|
Here is small example of the console output If I can provide anything more then please let me know. |
|
with regards to using http vs https. I haven't changed anything. It seems to want to use https. I tried passing in the http but no joy. Do I need to change something ? I came from .net window background, i stopped working with .Net around 3 years ago because of the non multi platform etc - this is my first try with .net core on mac. |
|
I meant does http work if you try that in your curl request? |
|
I did notice it says its listening on port 5000 for http but when i enter that in my browser it redirects me to https 5001 |
|
Open the Keychain app, and remove the localhost (depends on your app) from the system cert location and add id again as a trusted with a command above. |
|
run |
The step where you had to delete the localhost certificate in the system section in Keychain Access and then run dotnet dev-certs https and dotnet dev-certs https --trust solves the issue. |
|
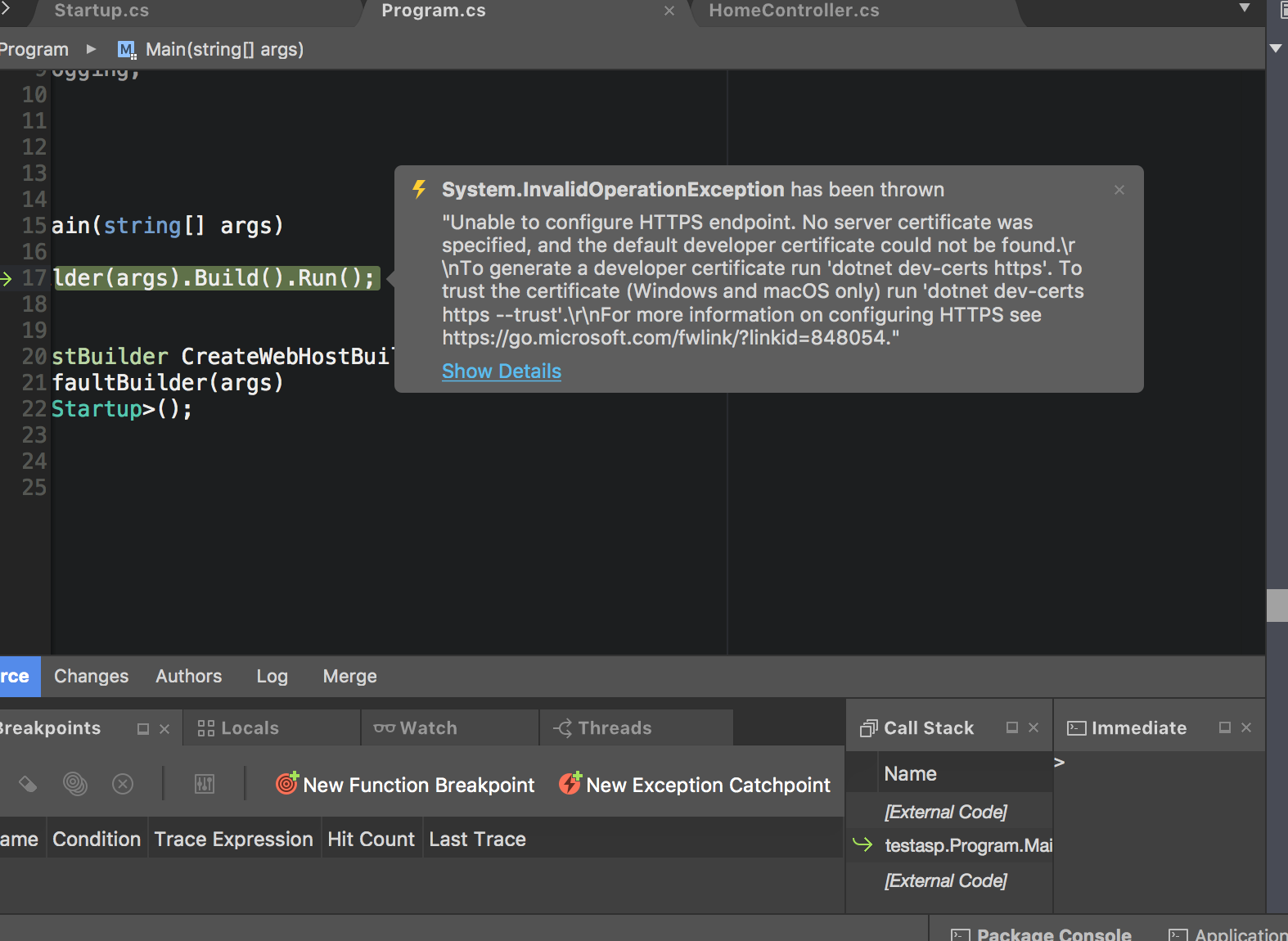
Newbie here:
Anyone know why I might be getting this error? How can I get more info as to why it's not able to save to the "certificate store"? EDIT: 2nd EDIT: |
|
The yellow lines suggest that this will run under sudo to get temporary privilege elevation. You can check if your current account is capable of doing that. |
|
This doesn't work at all over SSH, btw. |
|
|
Just chiming in to say I was having problems establishing a connection to a local SignalR application running on my Mac from a |
|
My web app using VS Code was OK, but all of a sudden I faced the same issue |
|
This seems beyond corefx and certificate manipulation @niranjanbhuta . If you think there is issue with asp.net, open new issue in corresponding repo. |
|
I was having the same issue, and was able to get past it using the following. It seems I had an old certificate from a previous .net core install that was conflicting. Removing and reinstalling a new dev cert did the trick. You may have to |
|
I faced in .NET Core 3.0 the same thing, solved using the same commands stated by @wfurt |
|
For those that are still having issues even after running the dev certs command, I fixed my issue by upgrading my dotnet core 3.0 preview to the release candidate edition and running the command again. |
|
dbug: HttpsConnectionAdapter[1] I have tried the solutions provided above but still i am getting the error. I updated my .net core version to 3.0.100 and used the below commands. still no use. please kindly help me regarding this. dotnet dev-certs https --clean |
|
this almost looks like you mixing http and https @ramakrishna578. I would suggest to do packet capture with Wireshark. |
|
Same issue here, using dotnet Core 3.0.100 on macOS Catalina 10.15. I've tried removing, adding and trusting the dev cert, and also using a trusted self-signed certificate. The outcome is the same - works in debug mode, fails when using Any ideas please? |
|
This could be related to dotnet/aspnetcore#15118 |
|
Thank you for very much your answer @wfurt .
Running codesign on the app (named "Shield"):
I would like to emphasise that when running in debug mode, my self-signed-trusted certificate works perfectly, so I would really like to better understand what is the difference between the run methods. Any help would be greatly appreciated! |
|
@assafsl - Did you ever figure this out? I'm having the same exact issue. VS Code debug mode works. Standalone |
it's same here for me. run from vscode or vs for mac is ok |
This did the trick. I missed the login section and was banging my head until I saw this post! Nice! |
|
What is the solution??
|
|
You should follow up discussion here dotnet/aspnetcore#19590 @roalroga. It is not responsibility of runtime to create or manage application certificates. Also commenting on closed issues is not good practice. |
I just wanted to drop by and say that this worked for me. Thank you! |






From @sankra on August 10, 2018 9:1
Is this a Bug or Feature request?:
Bug, HTTPS should work under development also on macOS.
Steps to reproduce (preferably a link to a GitHub repo with a repro project):
Run the following project on macOS: https://github.com/Sankra/HttpsMacOSFails
Description of the problem:
dotnet runand the debug command in VS for Mac. Requests over HTTPS to https://localhost:5001 fails with the stack trace below.Regular http works.
Version of
Microsoft.AspNetCore.MvcorMicrosoft.AspNetCore.ApporMicrosoft.AspNetCore.All:Microsoft.AspNetCore.App 2.1.1
Stack Trace
Hosting environment: Development
Content root path: /Users/sankra/projects/HttpsMacOSFails/HttpsMacOSFails
Now listening on: https://localhost:5001
Application started. Press Ctrl+C to shut down.
Loaded '/usr/local/share/dotnet/shared/Microsoft.NETCore.App/2.1.1/System.Threading.ThreadPool.dll'. Module was built without symbols.
Loaded '/usr/local/share/dotnet/shared/Microsoft.NETCore.App/2.1.1/System.Net.Security.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
Loaded '/usr/local/share/dotnet/shared/Microsoft.NETCore.App/2.1.1/System.Diagnostics.StackTrace.dll'. Module was built without symbols.
Loaded '/usr/local/share/dotnet/shared/Microsoft.NETCore.App/2.1.1/System.Reflection.Metadata.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
�[40m�[37mdbug�[39m�[22m�[49m: HttpsConnectionAdapter[1]
Failed to authenticate HTTPS connection.
System.IO.IOException: Authentication failed because the remote party has closed the transport stream.
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
HttpsConnectionAdapter:Debug: Failed to authenticate HTTPS connection.
System.IO.IOException: Authentication failed because the remote party has closed the transport stream.
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
�[40m�[37mdbug�[39m�[22m�[49m: HttpsConnectionAdapter[1]
Failed to authenticate HTTPS connection.
System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. ---> Interop+AppleCrypto+SslException: Internal error
--- End of inner exception stack trace ---
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
HttpsConnectionAdapter:Debug: Failed to authenticate HTTPS connection.
System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. ---> Interop+AppleCrypto+SslException: Internal error
--- End of inner exception stack trace ---
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
Loaded '/usr/local/share/dotnet/shared/Microsoft.NETCore.App/2.1.1/Microsoft.Win32.Primitives.dll'. Skipped loading symbols. Module is optimized and the debugger option 'Just My Code' is enabled.
�[40m�[37mdbug�[39m�[22m�[49m: HttpsConnectionAdapter[1]
Failed to authenticate HTTPS connection.
System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. ---> Interop+AppleCrypto+SslException: Internal error
--- End of inner exception stack trace ---
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
HttpsConnectionAdapter:Debug: Failed to authenticate HTTPS connection.
System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. ---> Interop+AppleCrypto+SslException: Internal error
--- End of inner exception stack trace ---
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
�[40m�[37mdbug�[39m�[22m�[49m: HttpsConnectionAdapter[1]
Failed to authenticate HTTPS connection.
System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. ---> Interop+AppleCrypto+SslException: Cipher Suite negotiation failure
--- End of inner exception stack trace ---
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
HttpsConnectionAdapter:Debug: Failed to authenticate HTTPS connection.
System.Security.Authentication.AuthenticationException: Authentication failed, see inner exception. ---> Interop+AppleCrypto+SslException: Cipher Suite negotiation failure
--- End of inner exception stack trace ---
at System.Net.Security.SslState.StartSendAuthResetSignal(ProtocolToken message, AsyncProtocolRequest asyncRequest, ExceptionDispatchInfo exception)
at System.Net.Security.SslState.CheckCompletionBeforeNextReceive(ProtocolToken message, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartSendBlob(Byte[] incoming, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.ProcessReceivedBlob(Byte[] buffer, Int32 count, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.StartReadFrame(Byte[] buffer, Int32 readBytes, AsyncProtocolRequest asyncRequest)
at System.Net.Security.SslState.PartialFrameCallback(AsyncProtocolRequest asyncRequest)
--- End of stack trace from previous location where exception was thrown ---
at System.Net.Security.SslState.ThrowIfExceptional()
at System.Net.Security.SslState.InternalEndProcessAuthentication(LazyAsyncResult lazyResult)
at System.Net.Security.SslState.EndProcessAuthentication(IAsyncResult result)
at System.Net.Security.SslStream.EndAuthenticateAsServer(IAsyncResult asyncResult)
at System.Net.Security.SslStream.<>c.b__51_1(IAsyncResult iar)
at System.Threading.Tasks.TaskFactory
1.FromAsyncCoreLogic(IAsyncResult iar, Func2 endFunction, Action1 endAction, Task1 promise, Boolean requiresSynchronization)--- End of stack trace from previous location where exception was thrown ---
at Microsoft.AspNetCore.Server.Kestrel.Https.Internal.HttpsConnectionAdapter.InnerOnConnectionAsync(ConnectionAdapterContext context)
Copied from original issue: aspnet/Mvc#8251
The text was updated successfully, but these errors were encountered: