New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
SslStream: Don't include "NT AUTHORITY" in Distinguished Names list of CertificateRequest. #60949
Comments
|
Tagging subscribers to this area: @dotnet/ncl, @vcsjones Issue DetailsDuring client certificate authentication, it is necessary to configure a certificate trust list in certain scenarios. This certificate trust list is configured in the Distinguished Names of the Certificate Request message of the TLS handshake. In NET 6.0, the ability to configure Distinguished Names list was added to SslStream via #45456. The trust list is set using any machine store on the server as shown here. However, for servers using SslStream, in addition to the trust list from the configured store, there is an additional "NT AUTHORITY" string in the Distinguished Names during the TLS handshake. This is unexpected and breaks clients, especially in scenarios where the intention is to send an empty Distinguished Names list in the TLS handshake. Below trace shows the expected behavior when the intention is to send a empty list in the DistinguishedNames. (This trace was collected on http.sys (not SslStream) The below snippet shows frame 55 from the attached wireshark capture. There are zero entries in the Distinguished Names because the trust list was configured with an empty store. Below snippet shows the EmptyCTL store on the server that was used to configure the trust list. Below trace shows the unexpected behavior when the Distinguished Names is configured with an empty list on SslStream. As you can see, the Distinguished Names list is not empty, it contains the string "NT AUTHORITY" This breaks the scenario and client does not send any certificate in the Certificate message of the TLS handshake as shown below. The expectation is to be able to configure the trust lists from the contents of the stores only and not have any additional strings (such as "NT AUTHORITY") in the DistinguishedNames during TLS handshake. Wireshark logs: serverhello.zip
|

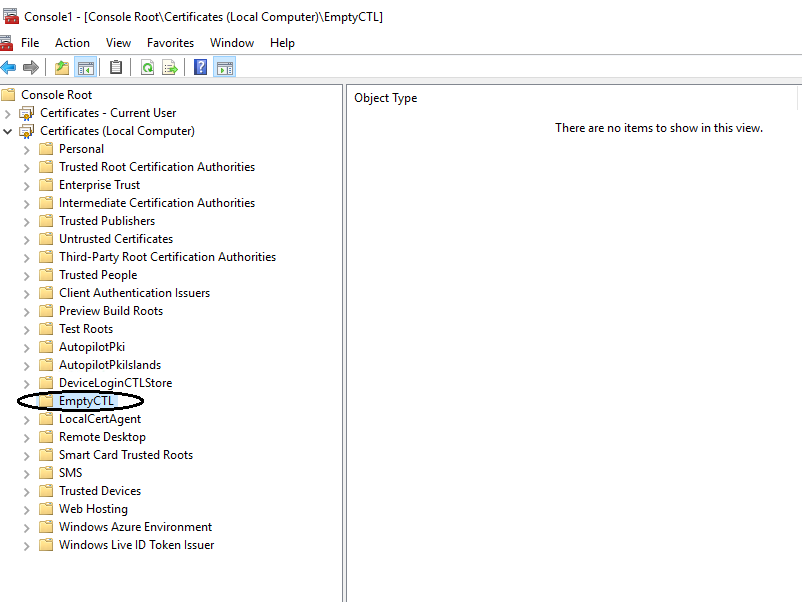


During client certificate authentication, it is necessary to configure trusted certificate authorities (CA) list in certain scenarios. This trusted CA list is configured in the Distinguished Names of the Certificate Request message of the TLS handshake.
In NET 6.0, the ability to configure Distinguished Names list was added to SslStream via #45456. The trusted CA list is set using any machine store on the server as shown here.
However, for servers using SslStream, in addition to the CA list from the configured store, there is an additional "NT AUTHORITY" string in the Distinguished Names during the TLS handshake. This is unexpected and breaks clients, especially in scenarios where the intention is to send an empty Distinguished Names list in the TLS handshake.
Below trace shows the expected behavior when the intention is to send an empty CA list in the Distinguished Names. (This trace was collected on http.sys (not SslStream)
The below snippet shows frame 55 from the attached wireshark capture. There are zero entries in the Distinguished Names because the CA list was configured with an empty store.
Below snippet shows the EmptyCTL store on the server that was used to configure the CA list.
On SslStream, below trace shows the unexpected behavior when the Distinguished Names is configured with an empty list. As shown below, the Distinguished Names list is not empty, it contains the string "NT AUTHORITY"
This breaks the scenario and client does not send any certificate in the Certificate message of the TLS handshake as shown below.
The expectation is to be able to configure the CA lists from the contents of the stores only and not have any additional strings (such as "NT AUTHORITY") in the Distinguished Names during TLS handshake.
Wireshark logs: serverhello.zip
The text was updated successfully, but these errors were encountered: