Authorization and Authentication with IdentityServer
IdentityServer is an open-source software framework that allows developers to add authentication and authorization
functionality to their applications. It is built on top of the open standards OAuth 2.0 and OpenID Connect,
which provide a secure and standard way to manage user authentication and authorization.
A central authentication and authorization server that can be used to authenticate users across numerous apps or services can be made by developers using IdentityServer. Users may log in once and access different resources without having to re-enter their credentials, resulting in a safer and more seamless user experience.
Because IdentityServer is so flexible and versatile, developers may combine it with other identity management systems or
add their own authentication and permission logic. As well as working with tokens, claims, and
other security-related features, it offers a comprehensive collection of tools and libraries.
IdentityServer can be installed using the following Docker files. More information about the installation is here: Getting Started

https://github.com/ebubekirdinc/SuuCat/blob/master/docker-compose.yml
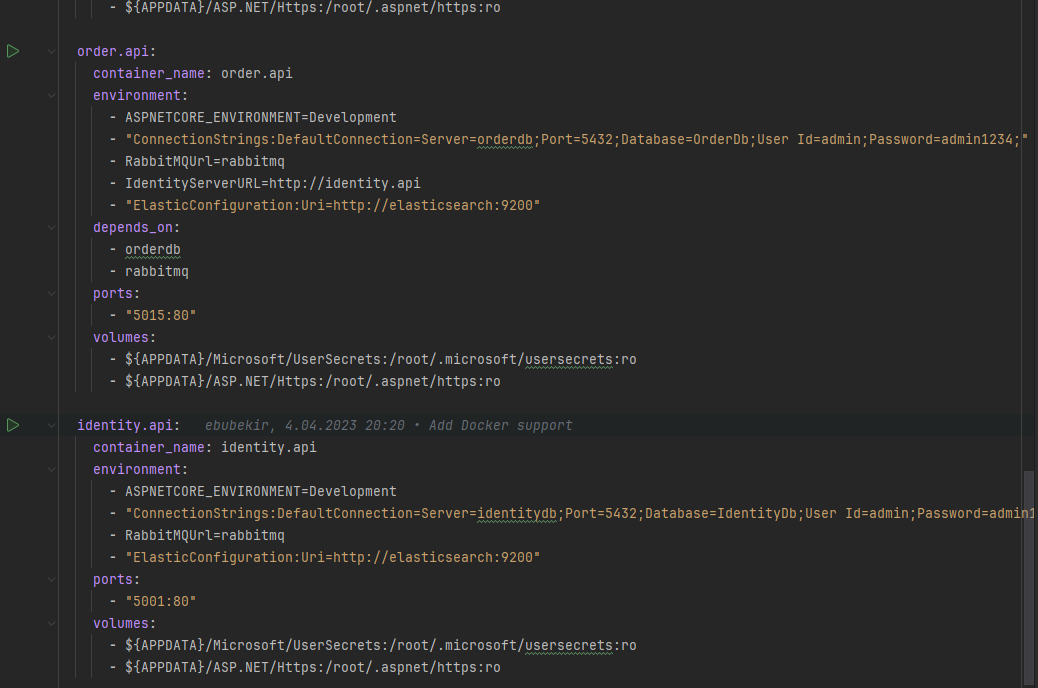 https://github.com/ebubekirdinc/SuuCat/blob/master/docker-compose.override.yml
https://github.com/ebubekirdinc/SuuCat/blob/master/docker-compose.override.yml
.
-IdentityServerURL=http://identity.api
This line should be added to every microservice in order to communicate with IdentityServer.
OAuth 2.0's Client Credentials grant type enables clients to request an access token from the authorization server
without involving users in order to access protected resources. With the help of its own credentials,
often a client ID and a client secret, the client authenticates itself to the authorization server in this flow and
receives an access token which can be used to access protected resources.
The client application sends a token request to the authorization server with its own client ID and secret as
authentication credentials in order to use the Client Credentials grant type. Following the client credentials being
verified, the authorization server generates an access token that the client application can use to gain access
to restricted resources.
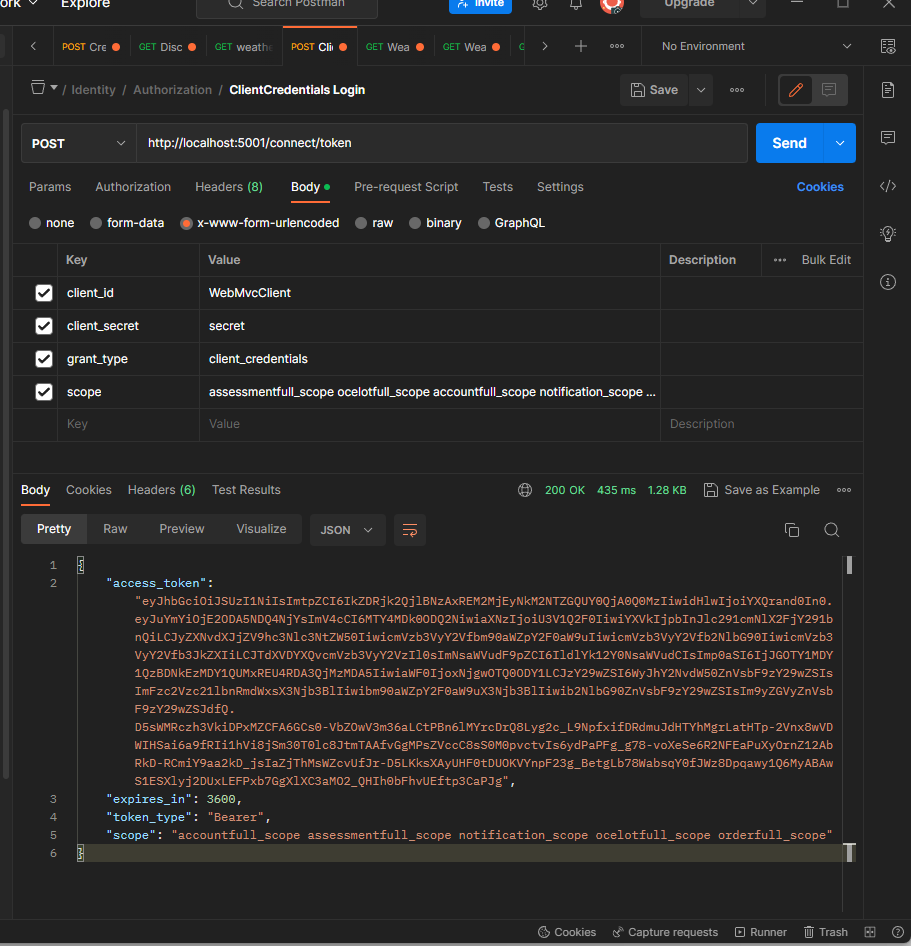
Client Credentials grant type request in Postman

Client Credentials token in jwt.io
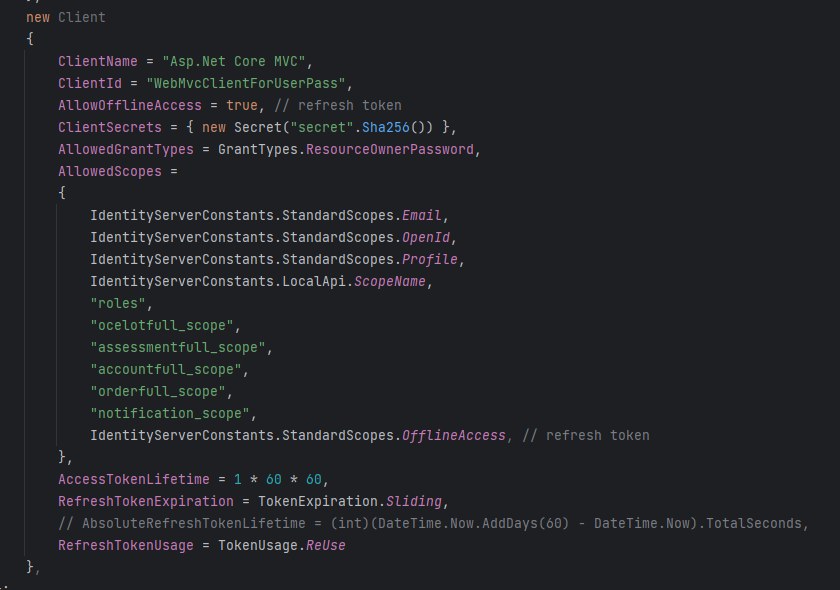
In the following code, the ClientCredentials grant type is configured in the Identity project.

https://github.com/ebubekirdinc/SuuCat/blob/master/src/Services/Identity/Config.cs
The AllowedScopes property specifies the scopes that the client is allowed to request. If the requested scope is not
present in this list, the request will be rejected with a 403 Forbidden.
One of the grant types in OAuth 2.0 and OpenID Connect, ResourceOwnerPassword, enables an application to
directly exchange the user's credentials (username and password) for an access token, enabling user authentication.
Under this grant type, the user must directly provide their credentials to the client application, which is
trusted to manage them safely.
By making a POST request to IdentityServer's token endpoint together with the user's username and password,
a client using ROPC can obtain an access token.

Resource Owner grant type request in Postman
Here is the info of the token from jwt.io

Resource Owner token in jwt.io
The following code snippet shows a configuration for a client that uses the Resource Owner Password Credentials
grant type in IdentityServer.