Commit
This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
[8.6] [Security Solution][Bug] Add privilege check in open timeline (#…
…147964) (#148587) # Backport This will backport the following commits from `main` to `8.6`: - [[Security Solution][Bug] Add privilege check in open timeline (#147964)](#147964) <!--- Backport version: 8.9.4 --> ### Questions ? Please refer to the [Backport tool documentation](https://github.com/sqren/backport) <!--BACKPORT [{"author":{"name":"christineweng","email":"18648970+christineweng@users.noreply.github.com"},"sourceCommit":{"committedDate":"2023-01-03T19:21:48Z","message":"[Security Solution][Bug] Add privilege check in open timeline (#147964)\n\n## Summary\r\n\r\nThis PR contains fixe for\r\nhttps://github.com//issues/147544. On Timelines page, a\r\nKibana read-only user was able to see and click on options to create and\r\nduplicate timelines. This PR fixes this bug by checking user privilege\r\n(have crud access) before showing timeline actions.\r\n\r\n## After: \r\nUser with read only access to kibana security solutions can: \r\n1) select timelines\r\n2) export timelines\r\n3) export timelines in bulk\r\n\r\nUser with crud access to kibana security solutions can: \r\n1) select timelines\r\n2) have the options to modify timelines as before\r\n3) bulk actions include delete timelines and export timelines\r\n4) see and click on 'import', ' Create new timeline', 'Create new\r\ntimeline template' buttons\r\n\r\n### User with read access but not crud access\r\n- Have access to export ('Export selected'), cannot see 'Create new\r\ntimeline' buttons\r\n\r\n\r\n\r\n- 'Export selected' in bulk actions\r\n\r\n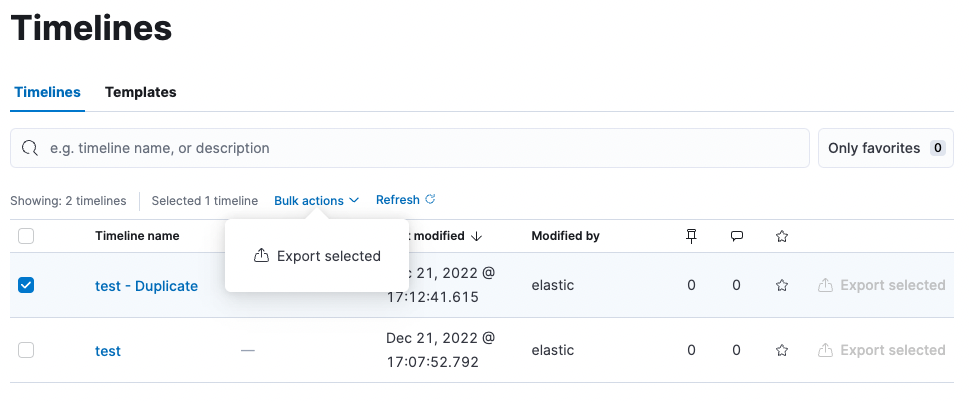\r\n\r\n\r\n\r\n\r\n### User with full access\r\n\r\n\r\n\r\n- 'Export selected' and 'Delete selected' available in bulk actions\r\ndropdown\r\n\r\n\r\n\r\n### Checklist\r\n\r\n- [x] [Unit or functional\r\ntests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)\r\nwere updated or added to match the most common scenarios\r\n\r\nCo-authored-by: Kibana Machine <42973632+kibanamachine@users.noreply.github.com>","sha":"3abf705b10926d3c6221504dd5575b97d15c9a31","branchLabelMapping":{"^v8.7.0$":"main","^v(\\d+).(\\d+).\\d+$":"$1.$2"}},"sourcePullRequest":{"labels":["release_note:skip","backport missing","Team:Threat Hunting","Team: SecuritySolution","Feature:Timeline","Team:Threat Hunting:Investigations","v8.6.0","v8.7.0"],"number":147964,"url":"#147964 Solution][Bug] Add privilege check in open timeline (#147964)\n\n## Summary\r\n\r\nThis PR contains fixe for\r\nhttps://github.com//issues/147544. On Timelines page, a\r\nKibana read-only user was able to see and click on options to create and\r\nduplicate timelines. This PR fixes this bug by checking user privilege\r\n(have crud access) before showing timeline actions.\r\n\r\n## After: \r\nUser with read only access to kibana security solutions can: \r\n1) select timelines\r\n2) export timelines\r\n3) export timelines in bulk\r\n\r\nUser with crud access to kibana security solutions can: \r\n1) select timelines\r\n2) have the options to modify timelines as before\r\n3) bulk actions include delete timelines and export timelines\r\n4) see and click on 'import', ' Create new timeline', 'Create new\r\ntimeline template' buttons\r\n\r\n### User with read access but not crud access\r\n- Have access to export ('Export selected'), cannot see 'Create new\r\ntimeline' buttons\r\n\r\n\r\n\r\n- 'Export selected' in bulk actions\r\n\r\n\r\n\r\n\r\n\r\n\r\n### User with full access\r\n\r\n\r\n\r\n- 'Export selected' and 'Delete selected' available in bulk actions\r\ndropdown\r\n\r\n\r\n\r\n### Checklist\r\n\r\n- [x] [Unit or functional\r\ntests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)\r\nwere updated or added to match the most common scenarios\r\n\r\nCo-authored-by: Kibana Machine <42973632+kibanamachine@users.noreply.github.com>","sha":"3abf705b10926d3c6221504dd5575b97d15c9a31"}},"sourceBranch":"main","suggestedTargetBranches":["8.6"],"targetPullRequestStates":[{"branch":"8.6","label":"v8.6.0","labelRegex":"^v(\\d+).(\\d+).\\d+$","isSourceBranch":false,"state":"NOT_CREATED"},{"branch":"main","label":"v8.7.0","labelRegex":"^v8.7.0$","isSourceBranch":true,"state":"MERGED","url":"#147964 Solution][Bug] Add privilege check in open timeline (#147964)\n\n## Summary\r\n\r\nThis PR contains fixe for\r\nhttps://github.com//issues/147544. On Timelines page, a\r\nKibana read-only user was able to see and click on options to create and\r\nduplicate timelines. This PR fixes this bug by checking user privilege\r\n(have crud access) before showing timeline actions.\r\n\r\n## After: \r\nUser with read only access to kibana security solutions can: \r\n1) select timelines\r\n2) export timelines\r\n3) export timelines in bulk\r\n\r\nUser with crud access to kibana security solutions can: \r\n1) select timelines\r\n2) have the options to modify timelines as before\r\n3) bulk actions include delete timelines and export timelines\r\n4) see and click on 'import', ' Create new timeline', 'Create new\r\ntimeline template' buttons\r\n\r\n### User with read access but not crud access\r\n- Have access to export ('Export selected'), cannot see 'Create new\r\ntimeline' buttons\r\n\r\n\r\n\r\n- 'Export selected' in bulk actions\r\n\r\n\r\n\r\n\r\n\r\n\r\n### User with full access\r\n\r\n\r\n\r\n- 'Export selected' and 'Delete selected' available in bulk actions\r\ndropdown\r\n\r\n\r\n\r\n### Checklist\r\n\r\n- [x] [Unit or functional\r\ntests](https://www.elastic.co/guide/en/kibana/master/development-tests.html)\r\nwere updated or added to match the most common scenarios\r\n\r\nCo-authored-by: Kibana Machine <42973632+kibanamachine@users.noreply.github.com>","sha":"3abf705b10926d3c6221504dd5575b97d15c9a31"}}]}] BACKPORT--> Co-authored-by: kibanamachine <42973632+kibanamachine@users.noreply.github.com>
- Loading branch information