Job that checks files for virus or frauds
Follow the next steps in order to run this project on your local environment.
Install Java JDK 11+.The JDK (Java Development Kit) is a development environment for building applications, applets, and components using the Java programming language.
The database used is Mongo DB 5+. There is a docker compose file to start a mongo db container. To start run the following command in the root folder:
docker-compose up -d
It will start a mongo db instance in port 27017. THe default username and password is root.
To build the project and install the dependencies you will need Maven 3.6+.
After installing the prerequisites, run the installation of the dependencies of the project. In the main folder of the project, run the following command
mvn clean install
Edit the file application.properties with the correct database configuration, case necessary
spring.data.mongodb.uri=mongodb://root:root@localhost/checks
spring.data.mongodb.database=checks
To execute the tests run
mvn clean test
To get coverage information run the following command. This will generate a html report in target/site folder with all the test coverage information.
mvn clean verify
To generate a build run the following command
mvn clean package
This will generate a target folder with a jar named malware-scanner-[version].jar. For example: malware-scanner-1.0.0.jar;
To start the server run the following command
java -jar malware-scanner-[version].jar
The development server will start in the port 8080
You can use the jar generated in the previous step to deploy in your application server
The blacklisted iban codes are set in a environment variable 'business.iban-blacklist'. It was done this way just to simplify the logic of the challenge. In a real world application it would be necessary to know how many iban codes would be in this blacklist and the frequency it would change. With that information we could choose to save this information in a cache (like Redis), or in the database, or even consume this information from another service. After the file is sent to analysis a cron job will read the files according to a configurable chunk and carry out the checks. After that the results will be available in the GET endpoint. This was done to allow asynchronous processing, because I could not use a Kafka or other queue related solution. To add another check you just need to create a class that implements the 'com.sdase.malware.scanner.checker.Checker' interface. The CheckerService will detect this new class and add in the list of checkers.
| Name | Default Value | Type | Required | Description |
|---|---|---|---|---|
| spring.data.mongodb.uri | mongodb://root:root@localhost/checks | string | true | The database connection uri |
| spring.data.mongodb.database | checks | string | true | The default database |
| management.endpoint.health.show-details | always | string | false | Flag to show healthcheck endpoint |
| business.iban-blacklist | DE89 3704 0044 0532 0130 00,AT61 1904 3002 3457 3201,FR1420041010050500013,DE15 3006 0601 0505 7807 80 | [string] | false | The blacklisted iban codes |
| business.cron.expression | 0/30 * * * * * | cron expression | true | The cron expression to the scheduled task |
| business.cron.chunk | 10 | number | true | The number of files to be processed each time |
There is a swagger endpoint where you can call the endpoints and see the responses in your web browser. It is available on:
/swagger-ui/
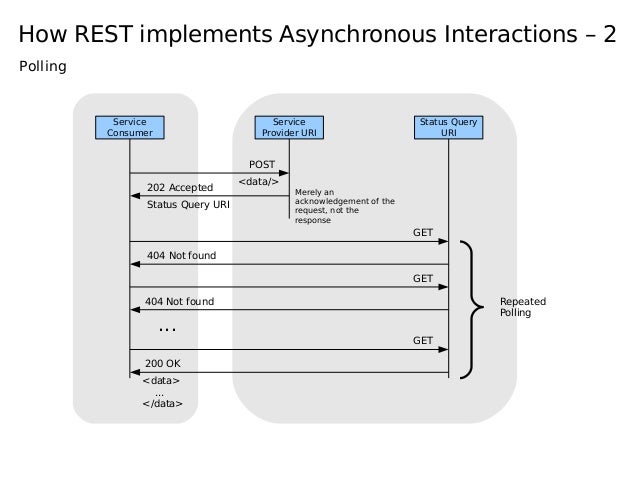
There are 2 API endpoints. The POST route will pre validate the file, save the content to the database and return a status 202 (Accepted) and a header 'Location' with the resource URL. While the file is not processed, the GET endpoint will return 404 (Not Found). A cron job will check for the files not yet processed and execute the verifications. After the verification the results will be available in the resource url returned in the first step. This processes is described in the following image:
POST /check/
| Attribute | Type | Required | Description |
|---|---|---|---|
| url | string | true | The URL of the file |
| fileType | string | true | The type of the file |
curl -X POST \
http://localhost:8080/check \
-H 'Content-Type: application/json' \
-d '{
"url": "/path-to-file/file.pdf",
"fileType": "pdf"
}'Responses
HTTP/1.1 202 Accepted
Location: /check/1
----------------------------------------------------
HTTP/1.1 422 Unprocessable Entity
{
"state": "IGNORED",
"name": "pre-validation",
"details": "An error ocurred while opening file"
}
GET /check/id
| Attribute | Type | Required | Description |
|---|---|---|---|
| id | string | true | The id of the file |
Responses
HTTP/1.1 404 Not Found
----------------------------------------------------
HTTP/1.1 200 OK
[{
"state": "OK",
"name": "iban-checker",
"details": "This file has a valid IBAN code"
}]
----------------------------------------------------
HTTP/1.1 200 OK
[{
"state": "IGNORED",
"name": "iban-checker",
"details": "This file does not have an IBAN number"
}]
----------------------------------------------------
HTTP/1.1 200 OK
[{
"state": "SUSPICIOUS",
"name": "iban-checker",
"details": "This IBAN code is on blacklist"
}]
GET /actuator/health
Responses
HTTP/1.1 200 OK
{
"status": "UP",
"components": {
"diskSpace": {
"status": "UP",
"details": {
"total": 250966470656,
"free": 149904588800,
"threshold": 10485760,
"exists": true
}
},
"mongo": {
"status": "UP",
"details": {
"version": "5.0.3"
}
},
"ping": {
"status": "UP"
}
}
}
- Elbio Caetano - Initial work - Elbio Caetano
This project is licensed under the Mozilla Public License 2.0 - see the LICENSE file for details