This commandline utility is intended to binary patch protected system files, such as drivers or DLLs, that reside in a Windows system directory.
This is primarily meant to be used to apply necessary fixes to the drivers of a newly created system, such as a Windows To Go drive or a directory where a Windows 10 image has been applied.
Windows 7 or later.
Use Visual Studio 2019 and invoke the .sln to compile.
Let's say you want to run Windows 10 ARM64 on a system where xHCI registers must be accessed through two
32-bit accesses (such as the VL805 controller of the Raspberry Pi 4), but the Windows USBXHCI.SYS driver
is enforcing 64-bit accesses, which results in a BSOD when trying to boot from an USB 3.0 drive.
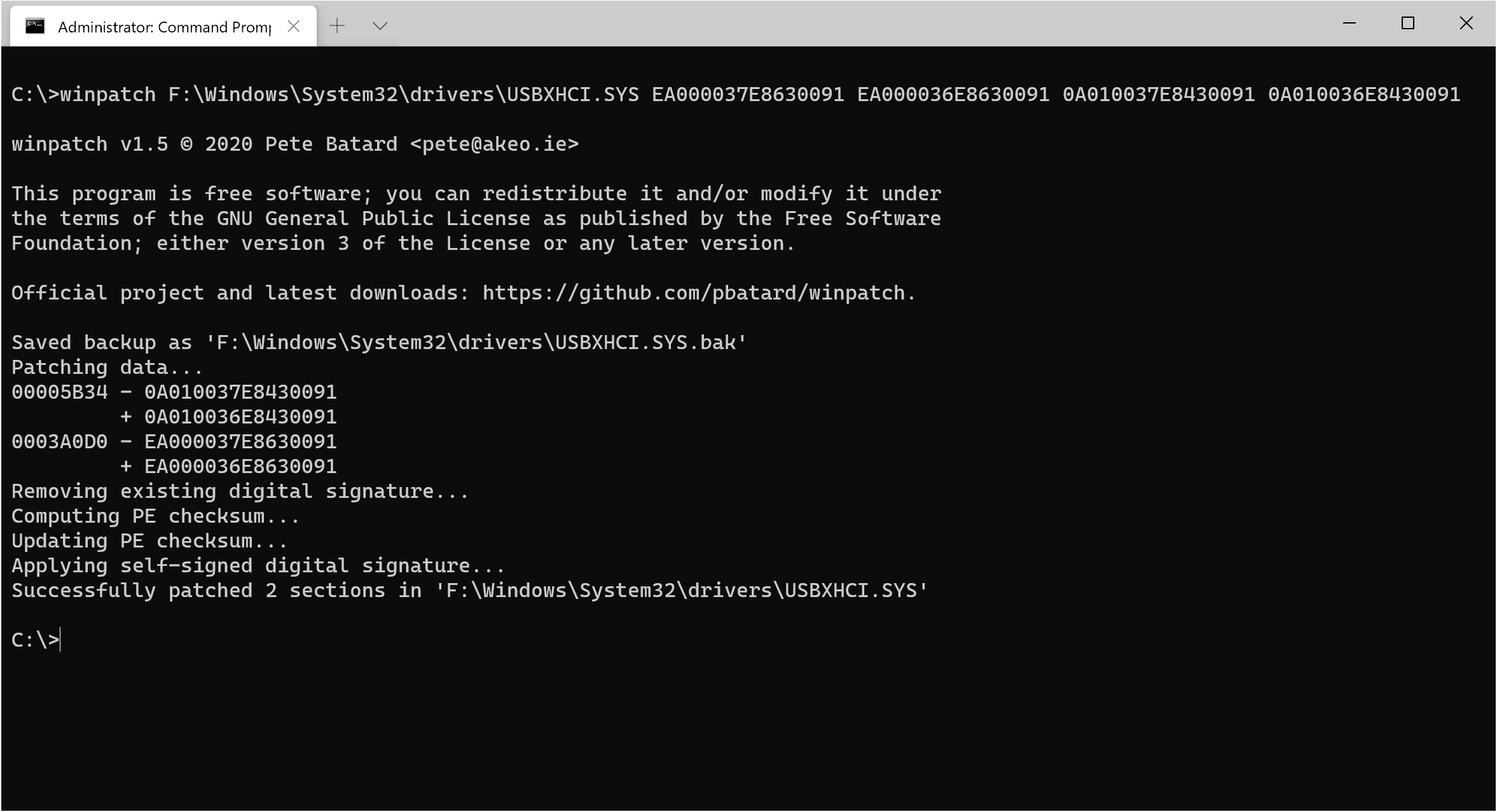
Provided that the driver for the system you want to patch resides in F:\Windows\System32\drivers\, then,
from an elevated command prompt, you can use winpatch as follows:
winpatch F:\Windows\System32\drivers\USBXHCI.SYS 910063E8370000EA 910063E8360000EA 3700010AD5033F9F 3600010AD5033F9F
Obviously, since you have patched a system file, you also have to disable signature enforcement with
something like (assuming the BCD for that drive resides on an ESP mounted as S:):
bcdedit /store S:\EFI\Microsoft\Boot\BCD /set {default} testsigning on
bcdedit /store S:\EFI\Microsoft\Boot\BCD /set {default} nointegritychecks on
Besides the patching (which currently must be aligned to 64-bit, i.e. winpatch does match with QWORDs that start at a 32-bit offset in the file), winpatch performs the following:
- Take ownership of the system file if needed.
- Delete the existing digital signature, if any.
- Update the PE32 or PE64 checksum after patching.
- Apply a new self-signed digital signature.
Each of these steps is required, because:
- System files are protected by Windows and you cannot alter them without taking ownership.
- If the file was patched, then the existing digital signature has become invalid.
- If you don't update the PE checksum, Windows produces BSODs during boot with error
0xc0000221(STATUS_IMAGE_CHECKSUM_MISMATCH) for the modified driver or DLL. - Even with
testsigningandnointegritychecksactive, if a modified system file is not digitally signed, Windows boots straight into recovery mode, with error code0xc000000ffromwinload.exe.