New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
add dumpntlm.py to examples #1523
Conversation
|
Might be worth renaming it to something like |
Agreed |
|
We agree that for this example to be merged, it needs a different name such as the proposed DumpNTLMInfo.py or omitting the word dump all together. |
|
@ShutdownRepo Thanks for your attention to my contribution. Could explain more please? |
|
@Sanmopre DumpNTLMInfo.py shows all the flags as they are, for security options and don't parse them as True/Flase (like crackmapexec). This means |
|
@NtAlexio2 Thanks for the quick response, could you add the option that you mentioned to check if SMBv1 is enabled or not? |
|
Hi! the concern here is more about how information is presented to the operator. For somebody who's coming from cme, it is actually a bit of confusing to see SIGNING_ENABLED when it is possible to establish a non signed connection. I know this is part of the protocol specification, but I think it could more than useful if we can somehow clarify when signing it's mandatory or not. |
|
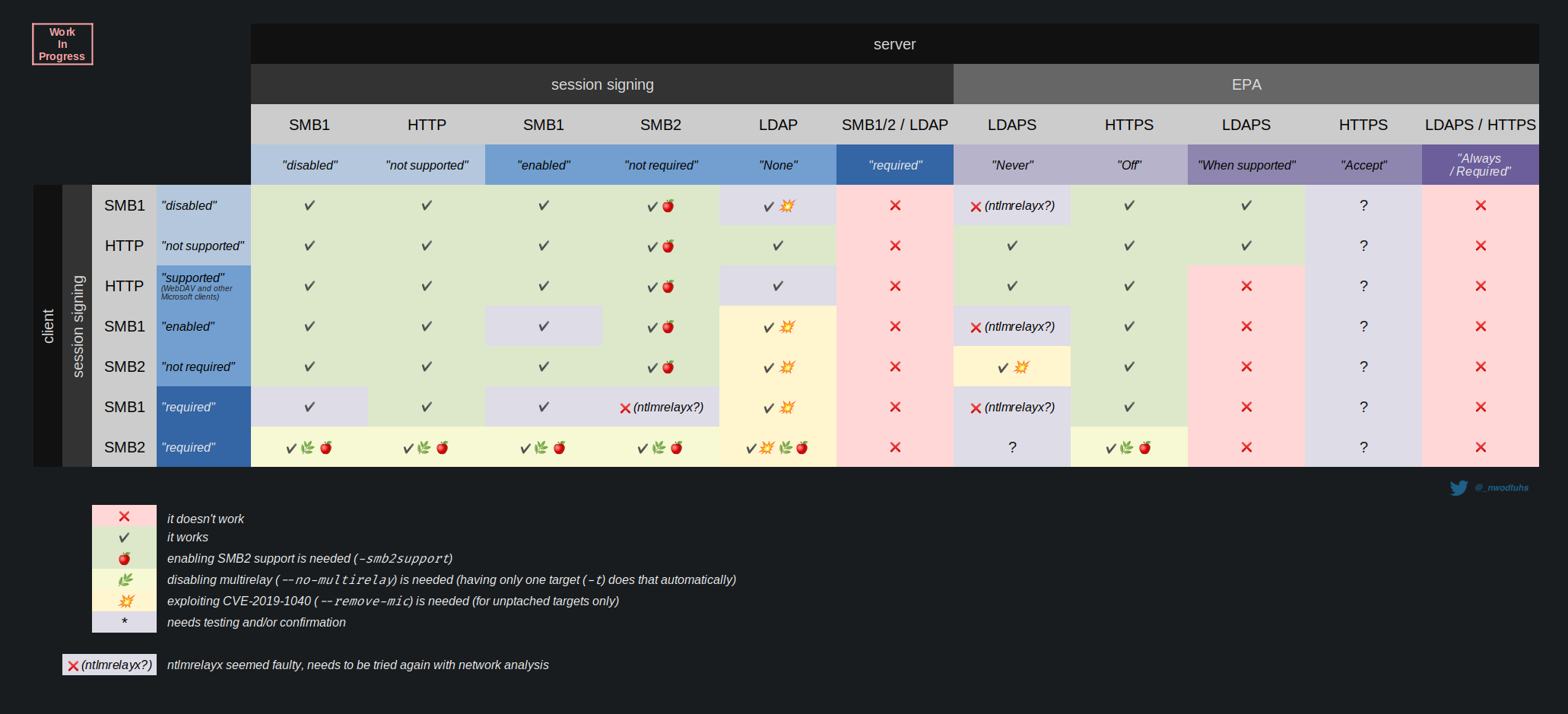
Not sure we need to base Impacket on CME. And returning the "raw" values is mandatory imo. The fact CME returns "true" is not enough as SMB signing has different settings whether it's client/server side or SMBv1/v2 (see The Hacker Recipe's NTLM relay chart below) We need a tool that show all this remotely. |
|
@Sanmopre Sure! ^^ |
This PR adds new file to
examples/folder nameddumpntlm.pywhich dumps NTLM information of remote computer using specific protocol. Features:Test output for domain-joined Windows 11 Build 22000 box: