v0.7.0
New Features
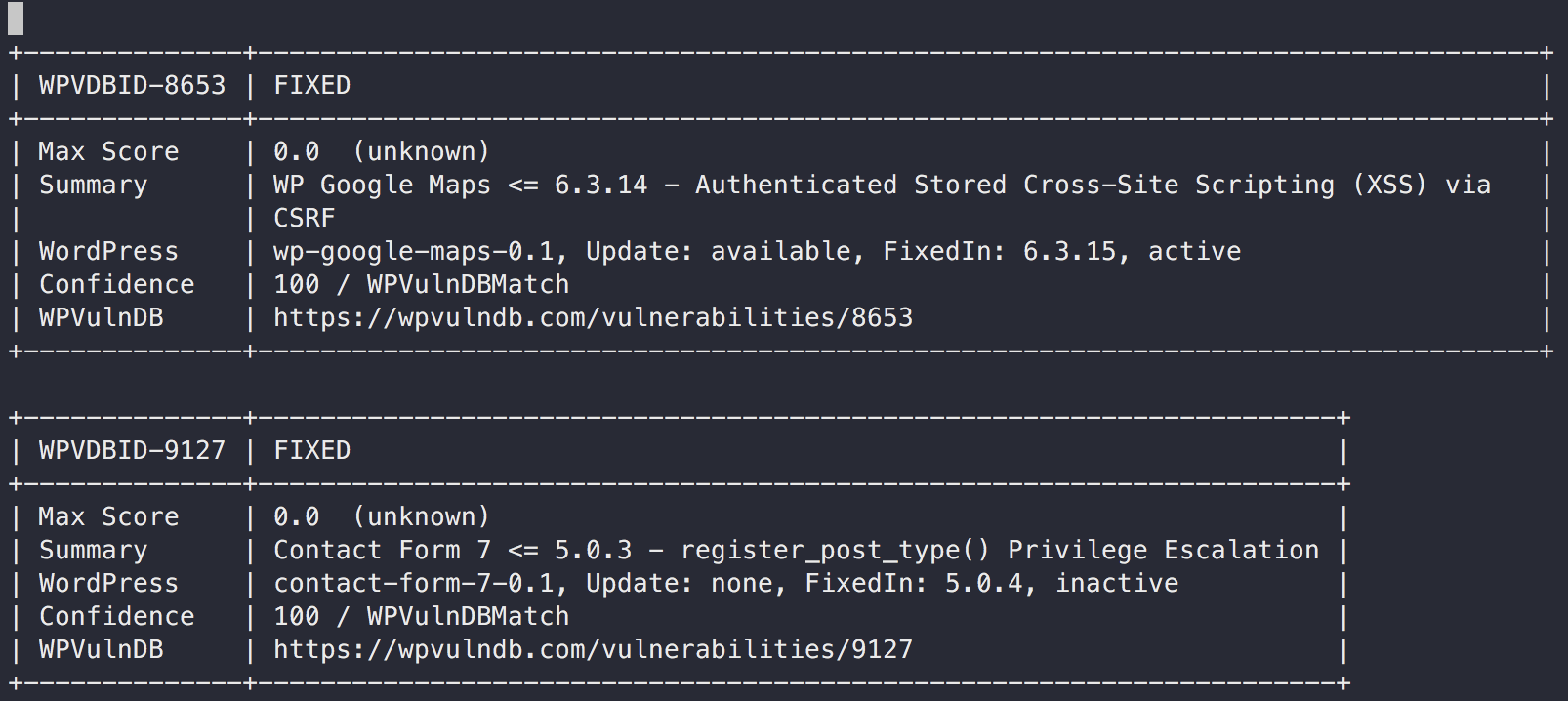
WordPress Vulnerability Scan (core, plugin, theme)
For non-commercial use, you can use this WordPress integration for free.
But for commercial use, You have to send a E-Mail to the WPVulnDB team.
For Details, see the NOTE:
If you are under any doubt if your software is classed as non-commercial and/or would like to inquire about commercial usage of our databases get in touch.
First, you need to register a user and get the API token from your profile page on wpvulndb.com.
And then, check whether the wp command is insatalled on the scan target server.
A sample configuration is below.
- config.toml
[servers.kusanagi]
user = "root"
host = "10.10.10.10"
port = "22"
[servers.kusanagi.wordpress]
cmdPath = "/usr/local/bin/wp"
osUser = "wordpress"
docRoot = "/home/kusanagi/wp/DocumentRoot/"
wpVulnDBToken = "xxxxTokenxxxx"
ignoreInactive = false
- cmdPath: A path of
wp-clion the WordPress server - osUser: A OS user of
wp-clion the WordPress server - docRoot: A path of document root on the WordPress server
- wpVulnDBToken: A token of WPVULNDB API
- ignoreInactive: Ignore plugins or themes which are inactive state
Scan
To scan WordPress, execute as below.
$ vuls scan kusanagi
Vuls collects WordPrss Core version, plugins and themes via wp-cli.
Reporting
$ vuls report
Vuls detects vulnerabilities via accessing WPVulnDB.com via HTTP.
- Slack
- TUI
- Full-Text
Changelog
6a1fc4f Merge branch 'master' of https://github.com/future-architect/vuls
9008d0d Add news to readme
583f457 fix goreleaser.yml
e5716d5 Add news to readme
7192ae1 Bump up version
99c65ef feat(scan): WordPress Vulnerability Scan (core, plugin, theme) (#769)
91df593 Editorial fixes (#798)
07aeaeb update go-exploitdb (#797)
cfeecda update pkgs (#796)
564dfa8 update cve dictionary (#795)
75dd6f2 Specify VOLUME using json syntax (#791)
e26fd0b fix(report): Critical Bug Fix for CPE based scanning #793 (#794)
d630680 feat(slack): enable -format-one-line-text with -to-slack (#792)
1723c3f fix(report): cpe match bug: go-cve-dictionary#120 (#790)
53dd903 fix(scan): parse error on SUSE #515 (#786)
5c6e06b Handle no-auth SMTP Servers and one liner email fix (#772)
cf6fb0c models: fix no-op append calls (#785)
e0e71b2 add scanner info in -to-saas (#783)
53f4a29 change implemention of integration (#780)