Releases: future-architect/vuls
v0.6.0
New Features
- Display exploit codes information for each detected CVE-IDs
Changelog
9865eab Display exploit codes information for each detected CVE-IDs (#729)
678e72a fix(gost): a bug of parseCwe (#726)
ec41899 check cve_contents init (#725)
b2d913c Bump Go versions and use '.x' to always get latest patch versions (#724)
bc86c24 update pkg (#723)
87a77dd update pkgs (#720)
e8188f3 add ms gost (#718)
50506be [WIP] feat(report): show repository of affected pkgs (#713)
4ded028 config: remove commented-out code from tomlloader (#714)
6da8b3c commands: simplify s[:] to s (#715)
d5c92cb report: simplify x = x <op> y to x <op>= y (#716)
ed5f98d change syslog pkg (#717)
f854b8f fix(report): fix an error while loading cveDict.type in config.toml (#711)
de7a615 remove table.SetHeaderColor codes (#709)
6090a34 fix(cpe): update deps to avoid parsing err of cpeNames (#708)
f566745 fix(config): a DB URL error 'does not validate as url' #705 (#706)
153234b update readme
ac510d2 fix(scan): fix err msg when unable to connect via SSH (#702)
v0.5.0
Clever vulnerability detection of non-OS-packages
https://vuls.io/docs/en/usage-scan-non-os-packages.html
Before v0.5.0, Vuls can detect only by exact match of CPE.
After v0.5.0, Vuls supports NVD JSON Feed
NVD JSON Feed has detailed affected version information.
"cpe" : [ {
"vulnerable" : true,
"cpe22Uri" : "cpe:/a:ibm:security_guardium",
"cpe23Uri" : "cpe:2.3:a:ibm:security_guardium:*:*:*:*:*:*:*:*",
"versionEndIncluding" : "8.2"
}, {
Using this information, Vuls can detect vulnerabilities of non-OS-packages more cleverly than before, because vuls compares versions of specified CPEs in config.toml and the version in the feed.
related ( #599 )
Significant improvement in scanning
Support knqyf263/gost (go-security-tracker)
New version Vuls 0.5.0 now possible to detect vulnerabilities that patches have not been published from distributors using new datasource named gost.
RedHat API
before
One Line Summary
================
c74 Total: 38 (High:12 Medium:18 Low:7 ?:1) 36/36 Fixed 708 installed, 288 updatable
after (with gost)
One Line Summary
================
c74 Total: 459 (High:48 Medium:326 Low:84 ?:1) 36/457 Fixed 708 installed, 288 updatable
Debian Security Tracker
before
One Line Summary
================
deb8 Total: 105 (High:22 Medium:39 Low:9 ?:35) 55/103 Fixed 513 installed, 43 updatable
after (with gost)
One Line Summary
================
deb8 Total: 524 (High:56 Medium:148 Low:21 ?:299) 53/522 Fixed 512 installed, 43 updatable
HTTP Server mode - One-Liner Scanning
Vuls can scan vulnerabilities with one-liner like below.
$ curl -X POST -H "Content-Type: text/plain" \
-H "X-Vuls-OS-Family: centos" \
-H "X-Vuls-OS-Release: 6.9" \
-H "X-Vuls-Kernel-Release: 2.6.32-696.30.1.el6.x86_64" \
--data-binary "`rpm -qa --queryformat "%{NAME} %{EPOCHNUM} %{VERSION} %{RELEASE} %{ARCH}\n"`" \
http://localhost:5515/vuls
For detials, see the Doc
Enable to define scan mode for each servers in config.tom
fast scan with internet access
- config.toml
[servers]
[servers.localhost]
host = "192.168.100.111" # or "127.0.0.1"
port = "22"
scanMode = ["fast"]fast scan without internet access
- config.toml
[servers]
[servers.localhost]
host = "192.168.100.111" # or "127.0.0.1"
port = "22"
scanMode = ["fast", "offline"]fast-root scan
fast-root scan with internet access
- config.toml
[servers]
[servers.localhost]
host = "192.168.100.111" # or "127.0.0.1"
port = "22"
scanMode = ["fast-root"]fast-root scan without internet access
- config.toml
[servers]
[servers.localhost]
host = "192.168.100.111" # or "127.0.0.1"
port = "22"
scanMode = ["fast-root", "offline"]deep scan
deep scan with internet access
- config.toml
[servers]
[servers.localhost]
host = "192.168.100.111" # or "127.0.0.1"
port = "22"
scanMode = ["deep"]Reports
The following items were added
- Display CWE name
- OWASP TOP 10
- Affected Packages, Processes
- Mitigation
TUI
report -format-full-text
report -format-list
Slack Notification
Stride Notification
https://vuls.io/docs/en/usage-report.html#example-send-scan-results-to-stride
#624

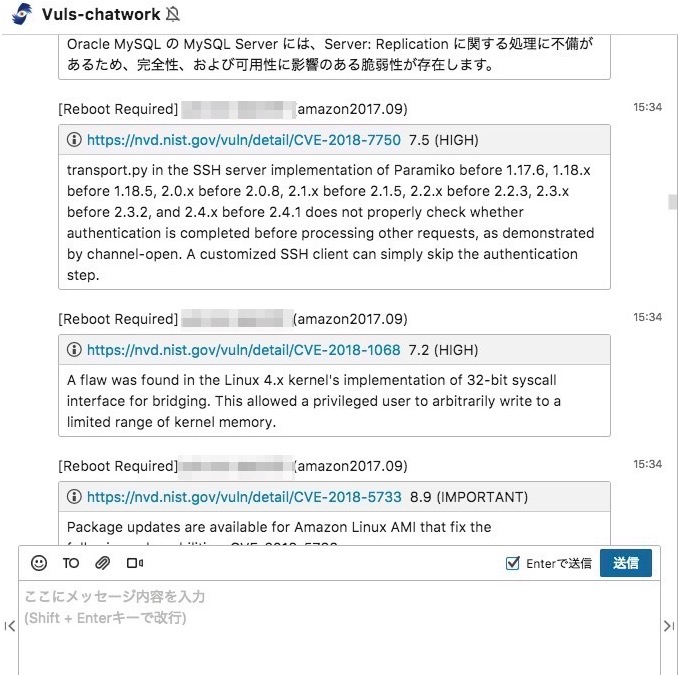
Charwork Notification
#634
https://vuls.io/docs/en/usage-report.html#example-send-scan-results-to-chatwork
go-cve-dictionary list subcommand
Change the format of ScanResult
Model has changed.
https://github.com/future-architect/vuls/tree/master/models
Change the format of config.toml
$ ./vuls discover 127.0.0.1/32
# Create config.toml using below and then ./vuls -config=/path/to/config.toml
[cveDict]
type = "sqlite3"
path = "/path/to/cve.sqlite3"
#url = ""
[ovalDict]
type = "sqlite3"
path = "/path/to/oval.sqlite3"
#url = ""
[gost]
type = "sqlite3"
path = "/path/to/gost.sqlite3"
#url = ""
# https://vuls.io/docs/en/usage-settings.html#slack-section
#[slack]
#hookURL = "https://hooks.slack.com/services/abc123/defghijklmnopqrstuvwxyz"
##legacyToken = "xoxp-11111111111-222222222222-3333333333"
#channel = "#channel-name"
##channel = "${servername}"
#iconEmoji = ":ghost:"
#authUser = "username"
#notifyUsers = ["@username"]
# https://vuls.io/docs/en/usage-settings.html#email-section
#[email]
#smtpAddr = "smtp.example.com"
#smtpPort = "587"
#user = "username"
#password = "password"
#from = "from@example.com"
#to = ["to@example.com"]
#cc = ["cc@example.com"]
#subjectPrefix = "[vuls]"
# https://vuls.io/docs/en/usage-settings.html#http-section
#[http]
#url = "http://localhost:11234"
# https://vuls.io/docs/en/usage-settings.html#syslog-section
#[syslog]
#protocol = "tcp"
#host = "localhost"
#port = "514"
#tag = "vuls"
#facility = "local0"
#severity = "alert"
#verbose = false
# https://vuls.io/docs/en/usage-report.html#example-put-results-in-s3-bucket
#[aws]
#profile = "default"
#region = "ap-northeast-1"
#s3Bucket = "vuls"
#s3ResultsDir = "/path/to/result"
#s3ServerSideEncryption = "AES256"
# https://vuls.io/docs/en/usage-report.html#example-put-results-in-azure-blob-storage<Paste>
#[azure]
#accountName = "default"
#accountKey = "xxxxxxxxxxxxxx"
#containerName = "vuls"
# https://vuls.io/docs/en/usage-settings.html#stride-section
#[stride]
#hookURL = "xxxxxxxxxxxxxxx"
#authToken = "xxxxxxxxxxxxxx"
# https://vuls.io/docs/en/usage-settings.html#hipchat-section
#[hipchat]
#room = "vuls"
#authToken = "xxxxxxxxxxxxxx"
# https://vuls.io/docs/en/usage-settings.html#chatwork-section
#[chatwork]
#room = "xxxxxxxxxxx"
#apiToken = "xxxxxxxxxxxxxxxxxx"
# https://vuls.io/docs/en/usage-settings.html#default-section
[default]
#port = "22"
#user = "username"
#keyPath = "/home/username/.ssh/id_rsa"
#scanMode = ["fast", "fast-root", "deep", "offline"]
#cpeNames = [
# "cpe:/a:rubyonrails:ruby_on_rails:4.2.1",
#]
#owaspDCXMLPath = "/tmp/dependency-check-report.xml"
#ignoreCves = ["CVE-2014-6271"]
#containerType = "docker" #or "lxd" or "lxc" default: docker
#containersIncluded = ["${running}"]
#containersExcluded = ["container_name_a"]
# https://vuls.io/docs/en/usage-settings.html#servers-section
[servers]
[servers.127-0-0-1]
host = "127.0.0.1"
#port = "22"
#user = "root"
#keyPath = "/home/username/.ssh/id_rsa"
#scanMode = ["fast", "fast-root", "deep", "offline"]
#type = "pseudo"
#memo = "DB Server"
#cpeNames = [ "cpe:/a:rubyonrails:ruby_on_rails:4.2.1" ]
#owaspDCXMLPath = "/path/to/dependency-check-report.xml"
#ignoreCves = ["CVE-2014-0160"]
#containerType = "docker" #or "lxd" or "lxc" default: docker
#containersIncluded = ["${running}"]
#containersExcluded = ["container_name_a"]
#[servers.127-0-0-1.containers.container_name_a]
#cpeNames = [ "cpe:/a:rubyonrails:ruby_on_rails:4.2.1" ]
#owaspDCXMLPath = "/path/to/dependency-check-report.xml"
#ignoreCves = ["CVE-2014-0160"]
#[servers.127-0-0-1.optional]
#key = "value1"
Enable to define CpeNames for each container.
To detect the vulnerability of Ruby on Rails v4.2.1 on specific container, cpeNames needs to be set in the servers>containers section.
The following is an example of running Ruby on Rails v4.2.1 on dockerA.
[servers]
[servers.172-31-4-82]
host = "172.31.4.82"
user = "ec2-user"
keyPath = "/home/username/.ssh/id_rsa"
containerType = "docker"
containersIncluded = ["${running}"]
[servers.172-31-4-82.containers.dockerA]
cpeNames = [
"cpe:/a:rubyonrails:ruby_on_rails:4.2.1",
]
Enable to define a path of OWASP Dependency Check XML for each container.
The following is an example of how to specify a XML of OWASP DC to the specific con...
v0.4.2
How to update
- Update goval-dictionary
$ rm -rf $GOPATH/pkg/linux_amd64/github.com/kotakanbe/goval-dictionary/
$ rm -rf $GOPATH/src/github.com/kotakanbe/goval-dictionary/
$ cd $GOPATH/src/github.com/kotakanbe
$ git clone https://github.com/kotakanbe/goval-dictionary.git
$ cd goval-dictionary
$ make install
$ goval-dictionary -v
goval-dictionary dca4f21
- Update Vuls
$ rm -rf $GOPATH/pkg/linux_amd64/github.com/future-architect/vuls/
$ rm -rf $GOPATH/src/github.com/future-architect/vuls/
$ cd $GOPATH/src/github.com/future-architect
$ git clone https://github.com/future-architect/vuls.git
$ cd vuls
$ make install
$ vuls -v
vuls v0.4.2 e788e6a
Changelog
e788e6a Support Alpine Linux #194 (#545)
d00e912 Replace strings.HasPrefix with strings.Index for SuSE scanner (#546)
8ebb663 Fix yum changelog option (#543)
445ffc4 Update README.md (#542)
6af49f4 Fix false positive: ignore oval info when kernel major version is different. (#541)
1de9e8c Fix: Misdetection of OvalMatch for CentOS and Scientific in oval/util.go (#536)
59b0812 Fix: "Reboot Required" detection process in scan/redhat.go (#534)
719785c Remove README.fr.md because unable to maintenance..
8e5f627 README Typo Update (#538)
5ced3c7 Insert sudo only at the beginning of command in deep scan #495 (#539)
c002f01 Fix config.toml validation (#537)
00c690f Add pseudo server type for non-ssh scanning (only cpe scan) #512 (#531)
ab68ad5 README Update (#530)
5c84ebe Update README
eb2acaf send slack msg by api (#525)
84d0655 fix typo Privious -> Previous (#523)
e137ebb Fix package query fails on debian based container (#519) (#522)
10d690d fix typo from "enviroment" to "environment" (#518)
14611d2 Fix typo in config/jsonloader.go (#517)
0665bfe Modified Spell Miss of "README.md". (#516)
Automated with GoReleaser
Built with go version go1.8 linux/amd64
v0.4.1
Changelog
473096d Fix .goreleaser.yml
0eae26e Merge branch 'master' of https://github.com/future-architect/vuls
a32845f Fix a bug of making channels when fill oval information via HTTP (#514)
15a0f7e Merge branch 'master' of https://github.com/future-architect/vuls
5a0a6ab Fix OVAL detection on Debian and Ubuntu (#509)
032b8d9 Merge branch 'master' of https://github.com/future-architect/vuls
5798e3a Add filter options to tui subcommand (#508)
8e15b9c Add filter options to tui subcommand (#508)
7a1f132 Add -ignore-unfixed option to report subcommand #485 (#507)
a8483b2 Add goreleaser to distribute binaries (#460)
83bbbd0 Add goreportcard to README
132432d Support SUSE Enterprise Linux (#487)
e5eb8e4 Debian: Use --showformat flag to get status of packages and ignore n(not-inst… (#484)
1095ebe fix vulsrepo dockerfile (#496)
1541a60 Update README.ja.md (#498)
03a141c Fix typos (#499)
5f2183f Check repoquery with sudo nopasswd in deep scan mode on RedHat (#492)
820831f Fix sort order of servers on TUI (#481)
6d2d767 Fix a arg of report subcommand (#479)
e0c3a72 Fix ping option of discover subcommand #471 (#472)
ec92f77 add windows type (#470)
0ba490c Merge pull request #469 from usiusi360/use_vulsrepo-server
cfd668e use_vulsrepo-server
Automated with GoReleaser
Built with go version go1.8 linux/amd64
v0.4.0 (No Backward Compatibility)
v0.4.0
We are pleased to announce the new Version, v0.4.0.
This version is not backward compatible.
But many new functions have been added.
How to install newly
How to update to the latest verison
Fast nosudo scan mode and Deep scan mode
Fast nosudo scan mode (Default)
-
This mode scans
- Ultra high speed
- Without root privilege
- Not consume so much resources on the servers to be scanned.
- Scanning is possible in an environment without Internet connection
- Some OS needs internet connection ... Amazon, FreeBSD, Raspbian
-
Scan Method
- RHEL, CentOS, Debian, Ubuntu, Oracle
- Only collect information of the packages installed
- Amazon
- yum-plugin-security
- FreeBSD
- pkg-audit
- RHEL, CentOS, Debian, Ubuntu, Oracle
-
Report
- Compare package version to detect CVE-IDs using local OVAL DB.
- Use vulnerability information such as NVD, JVN, OVAL
Deep scan mode
-
https://github.com/future-architect/vuls#deep-scan
This mode may consume resources on the server to be scanned and some commands may need root privilege. However, deep scan mode is more accurate vulnerability detection and more detailed information than fast scan mode. -
Scan Method
- Ubuntu, Debian
- parse changelog to detect CVE-IDs
- need sudo(apt-get update)
- CentOS
- parse changelog to detect CVE-IDs
- no sudo
- RHEL
- collect changelogs (no parse)
- collect information of yum-plugin-seucrity
- need sudo
- Amazon Linux
- collect changelogs (no parse)
- collect information of yum-plugin-seucrity
- no sudo
- Ubuntu, Debian
-
Report
- Compare package version to detect CVE-IDs using local OVAL DB.
- Use vulnerability information such as NVD, JVN, OVAL
Improvement of vulnerabilities detection accuracy
- OVAL Support (CentOS, RHEL, Debian, Ubuntu, OracleLinux)
- Use vulnerability information of OVAL when reporting.
- Use version comparison when parsing change log (CentOS, Ubuntu, Debian)
Detect the vulnerability that is not yet fixed
- CentOS
- There are many packages that has been fixed in RedHat, but not been fixed in CentOS.
- Ubuntu, Debian
- OVAL has this information
Notify Reboot Required
Vuls warns when the scan target server was updated the kernel etc. but not restarting it.
Change the structure of models
The structure of the model has changed.
This version is not backward compatible.
Obtain changelog
- Use
yum changelogin yum-utils instead ofyum update --changelogin yum-plugin-changelog to fetch changelogs without root privilege. - Use version comparison logic when parsing change log (Ubuntu, Debian)
Display the information of yum plugin-security on TUI
Changelog
These fine people have contributed
v0.3.0
Add Report Subcommand
see https://github.com/future-architect/vuls/blob/master/CHANGELOG.md
The main pull request is below
#270