Automatic re-enable of CloudTrail in case of malicious or accidentally disable.
This is a security enforce module for CloudTrail.
If somebody hacks your AWS account the first action would be disabled or delete the CloudTrail to cover his tracks. Receive an alert, in this case, can save our business from huge and expensive disasters.
The project catches 2 events one is the StopLogging the other is DeleteTrail.
- StopLogging cause the CloudTrail enabling again and sends an email to the SNS topic.
- DeleteTrail sends an email to the SNS topic.
The Terraform module creates the components in the red square.
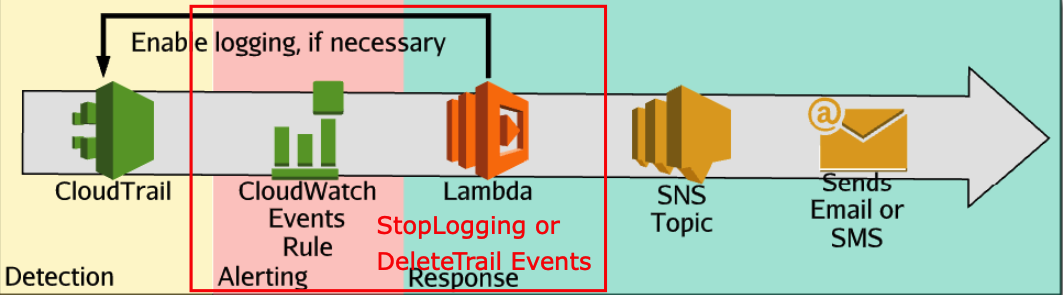
These 2 elements should be already created.
- CloudTrail
- SNS with Email confirmation
Use this code in your terraform project
module "cloudtrail-automatic-re-enable" {
source = "giuseppeborgese/cloudtrail-automatic-re-enable/aws"
prefix = "ts"
sns = "arn:aws:sns:us-east-1:01234567:giuseppe-sns"
}if you like this module leave a comment or a thumbs up in the youtube video, subscribe to my youtube channel https://www.youtube.com/channel/UC-NS9CMNufWQglUyVQzaFqQ and follow my article on medium https://medium.com/@giuseppeborgese
If you want to know more about Security in AWS take a look to this course https://linuxacademy.com/course/aws-certified-security-specialty/
