-
Notifications
You must be signed in to change notification settings - Fork 83
HTTPSB's fixNoscriptTags() doesn't fix noscripts #177
Comments
|
The problem you report here is of a different breed. It appears that when using Content Security Policy to block javascript, the browser doesn't render as if javascript was disabled (which would cause |
|
I can't look at the fix right now, give me time I will look later. |
|
No problem. You don't have look at my fix. Its probably the wrong way to do it. You know what you're doing and you're on another level. I'm just messing around. |
|
Can you submit a pull request, I want to pull your code in the project. Also, before you do, you can get rid of the now obsolete (commented out) The behavior you fixed is not actually a bug in Thanks for contributing, much appreciated. More contributions welcomed at any time. |
|
Fixed in pull request #180. |
|
Umm... This I checked Firefox's NoScript setting and Before I found HTTPSB, I used ScriptSafe for Chromium and it also had So I think the way you had it before was better. Parsing Sorry gorhill |
|
There is nothing wrong, HTTPSB will block these 1x1 pixel image (or likes) anyways. I like that they are reported, I dislike that these would be removed without the user being informed they existed. That's what HTTPSB is about, showing what a web page tried to do. I checked with Wired yesterday and I saw only legit images, so I don't think Wired is wrong. I will check again today to see. |
|
In your first picture, you where on
Etc. I want the user to know that the web page tried to pulled data from blocked 1st- and 3rd parties. This is the whole point: an informed user. Now not all 1x1 pixel images are bad. There are many of them on Wired I saw today, and it's for the purpose of "lazy loading", i.e. they want the images to load after the main page has fully loaded and is in idle mode, in order to make their page load faster. |
|
Just to show you how "hiding" is a bad solution. I went to Firefox + Noscript, and checked the option |


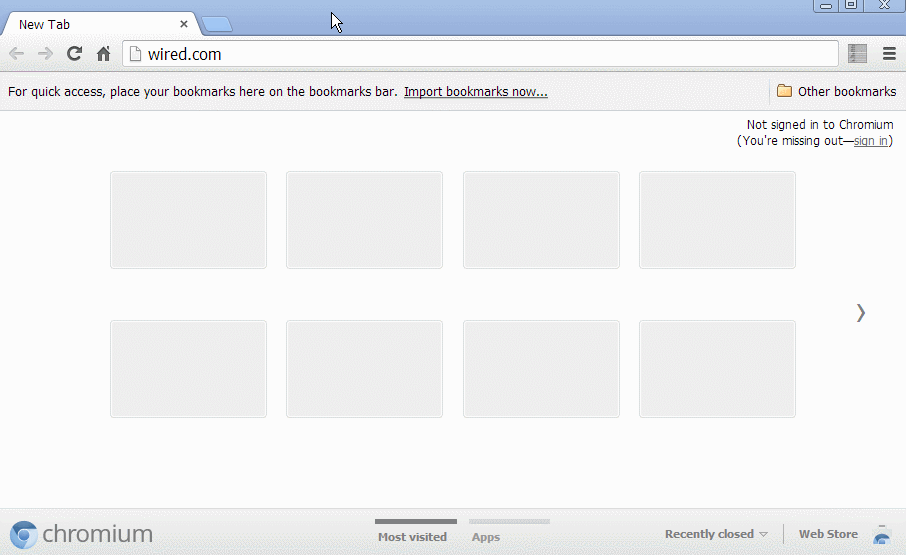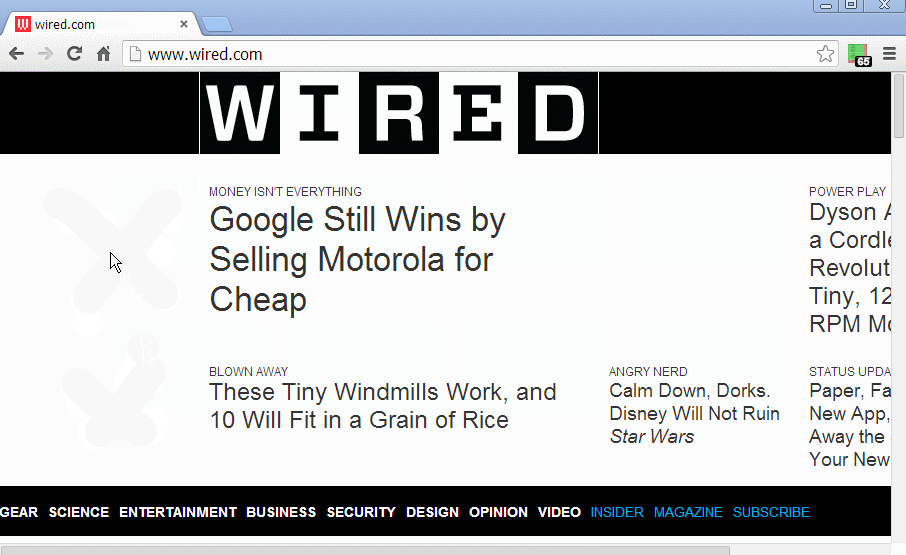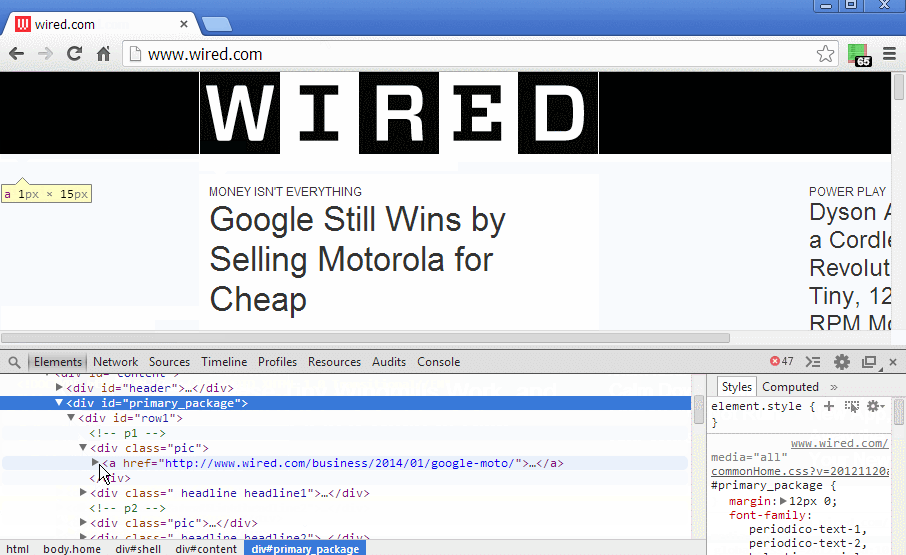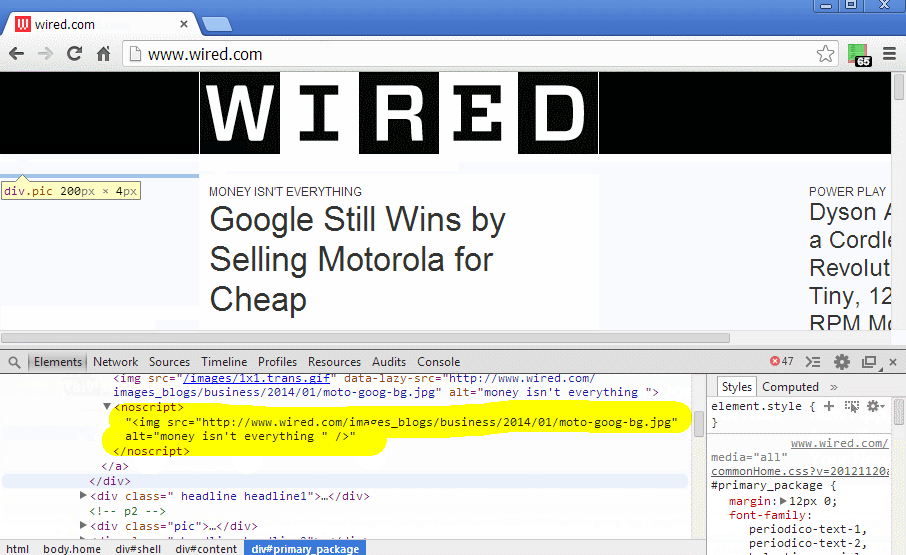
You can see that there are images shown which are inside the noscript tag.
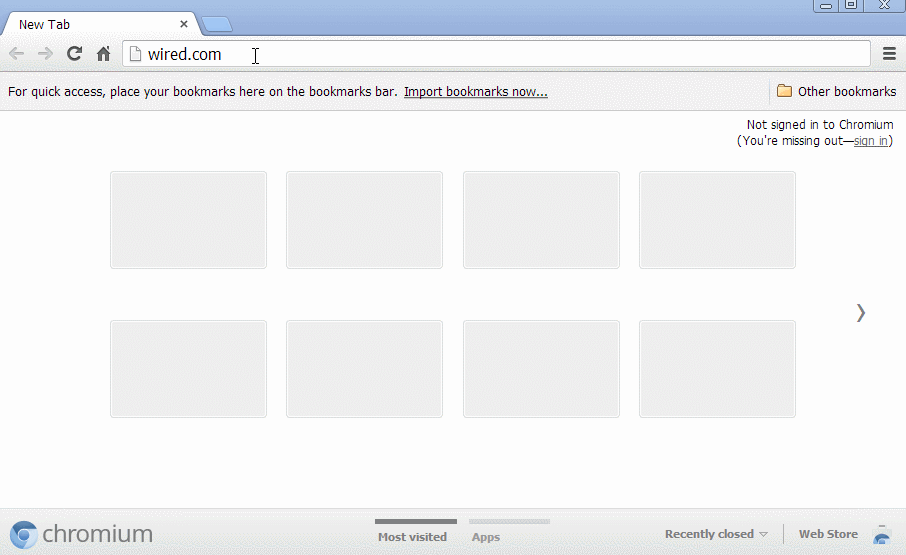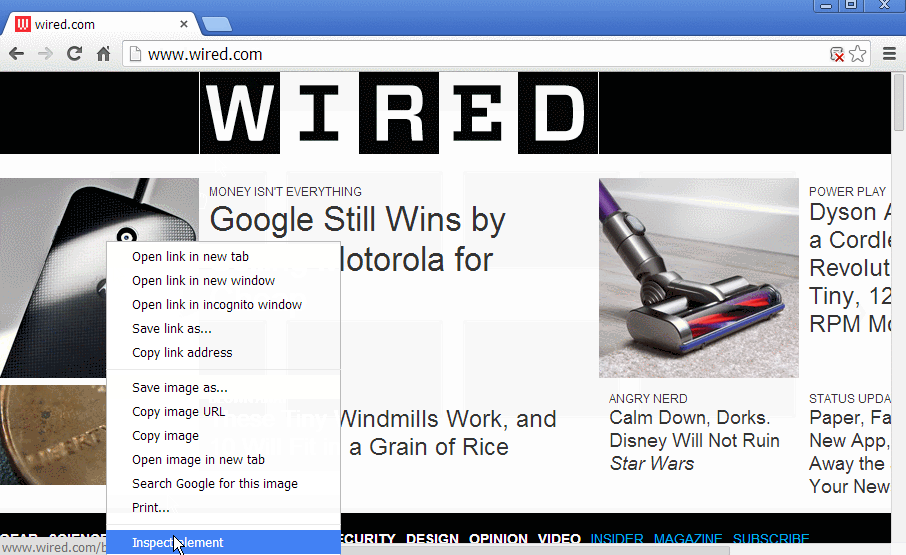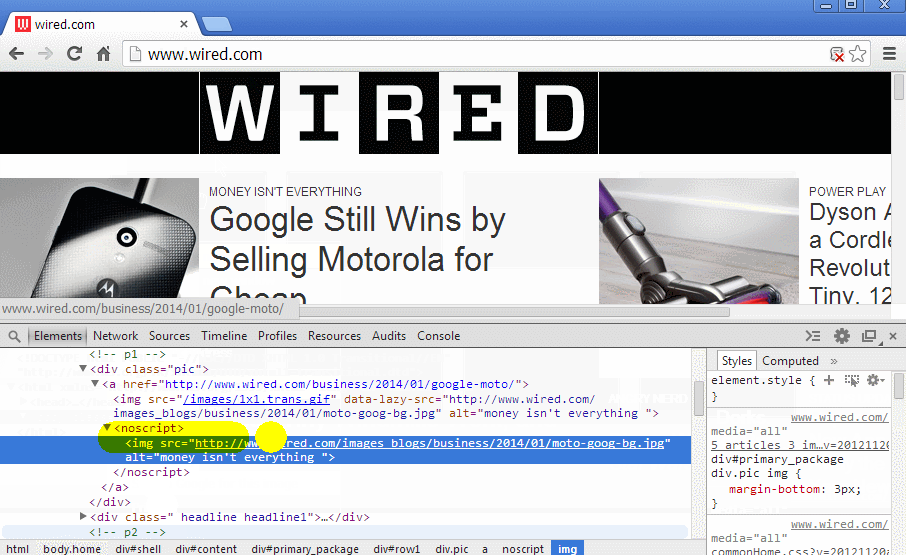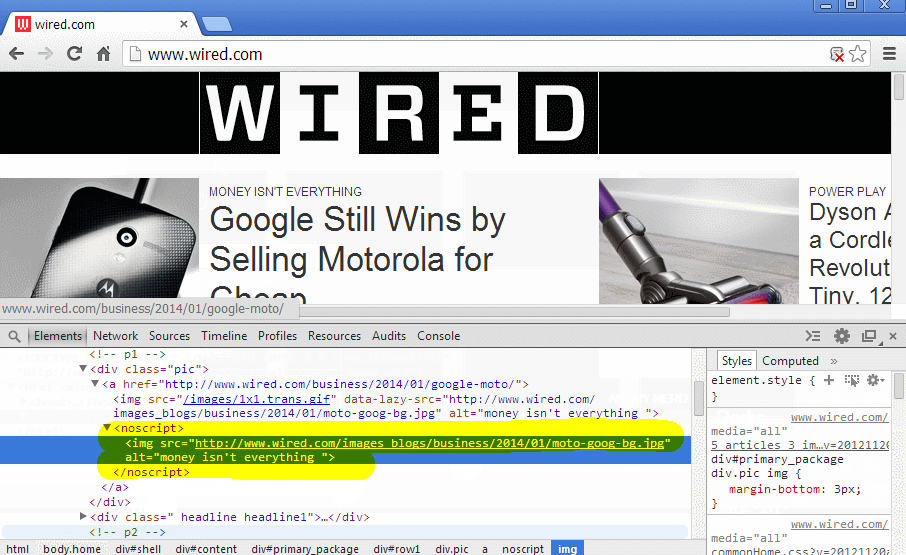
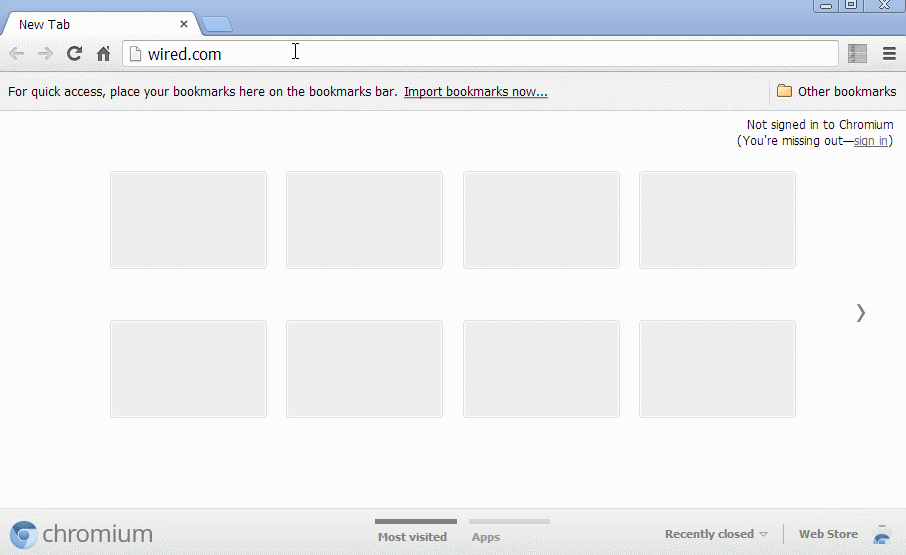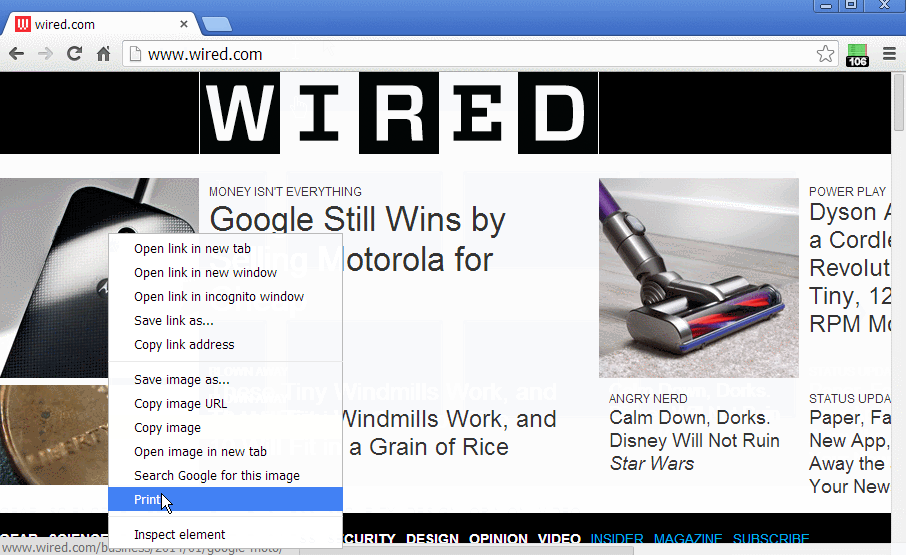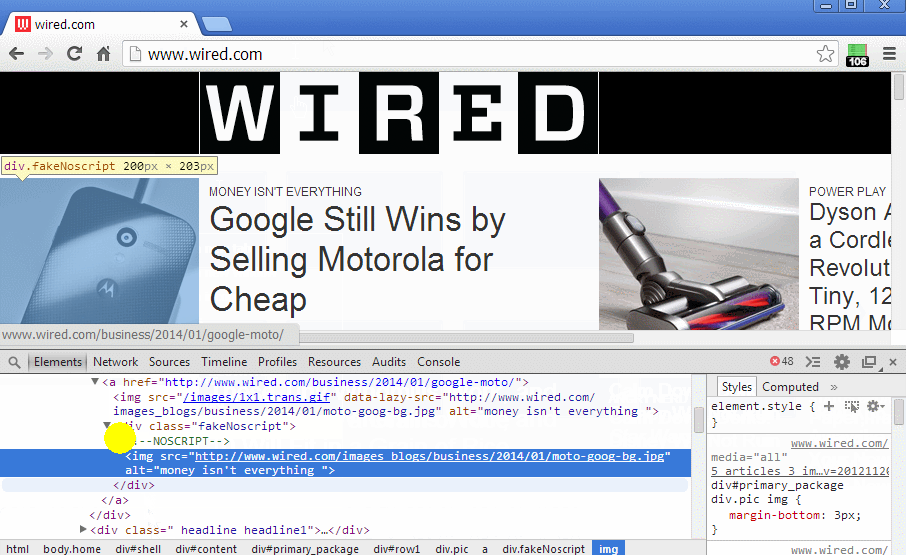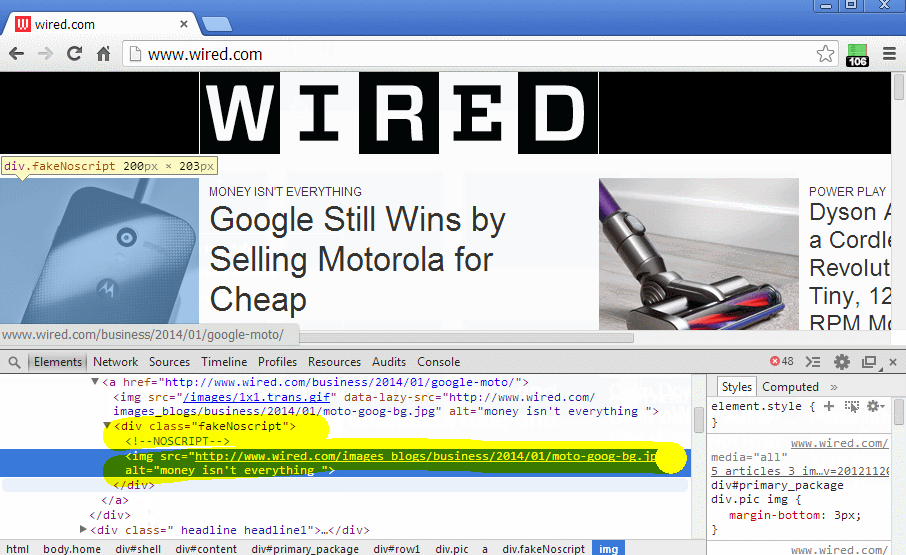
The function fixNoscriptTags() didn't force the DOM Parser to parse the noscript tag. If you inpsect the noscript element you will see Its still text.
A workaround would be to replace the noscript tag with a div that parses the children of the noscript, only if scripts are blacklisted.
Trying to learn to use github. I forked it to try and mess around. Here's my workaround.
my-password-is-password@a93530d
I still don't know how to use github so forgive me if I'm getting in your way. :)
The text was updated successfully, but these errors were encountered: