This is a use case for using Cisco Duo APIs to bring Multifactor Authentication (MFA) to protect access control in different setup, this prototype uses a simple RFID reader on a Raspberry Pi to emulate the user experience. When the user presents an RFID tag to the reader, the user will get a push notification from Cisco Duo to authorise the access before access is granted.
NOTE — please ensure both git and pip are installed in your environment by running the following command:
$ sudo apt-get -y install git python-pip
$ git clone https://github.com/gve-sw/DNAC_usecase
$ pip install pad4pi
$ pip install webexteamssdk
$ pip install duo_client
$ pip install mfrc522
$ pip install RPi.GPIO
Before starting to play with this prototype you need to create accounts in Cisco Duo & Webex Teams and get the relevant credentials.
You can create a free account for 10 users at Duo, follow this link for details. For this project we are using the Duo Auth API, you can find documentation here. The documentation will guide you through the creation of an application protection for our RFID client. Once created you can copy the application keys to export as environment variables.
$ export ikey='your Integration key (DI...)'
$ export skey='your Secret key'
$ export host='your API hostname (api-....duosecurity.com)'
Create a user from the Duo admin panel, with the name 'test' this same username will be used in the RFID tag.
You can create a free account in Webex Teams here. Once created you can follow the documentation here to create your first BOT, take note of the bot token as it will need to put it in an environment variable:
$ export WEBEX_TEAMS_ACCESS_TOKEN="Your webexteams bot token here"
Update duo_rfid.py with your own email address:
# Add people to the new demo room
try:
email_addresses = ["exmple@exmple.com"]
for email in email_addresses:
api.memberships.create(demo_room.id, personEmail=email)
except Exception as e:
print(e)This project is run on a Raspberry Pi 3 model B with Raspbian OS. You can find documentation here on how to setup your Raspberry Pi. In addtion you will need the following:
- 3x LED (red, green, blue)
- 3x 100 resistance
- Raspberry Pi 4X4 Keypad
- Raspberry Pi RFID RC522 Reader
- RFID tags
The keypad used here is a 4x4, but you can use a 3x4 keypad by changing the keypad matrix. You can find here more details on the matrix and wiring .
# Setup Keypad
KEYPAD = [
["1","2","3","A"],
["4","5","6","B"],
["7","8","9","C"],
["*","0","#","D"]
]
# same as calling: factory.create_4_by_4_keypad, still we put here fyi:
ROW_PINS = [5, 13, 19, 26] # BCM numbering
COL_PINS = [12, 16, 20, 21] # BCM numberingYou can test your keypad using the keypadtest.py file.
The RFID reader used in this project is the common RC522. Uou can use rfidwrite.py file and rfidread.py to write the username in your RFID tags. Follow this tutorial for more details.
Please make sure that the username you are writing on the RFID is the same user you created in your Duo account.
Leds will show notifications of what is happening with the demo, and here is how to read those. Leds need to be wired.
- Green blinking : access granted
- Red blinking : access denied
- Blue blinking : timeout, use the keypad for pin
run duo_rfid.py
$ python duo_rfid.py
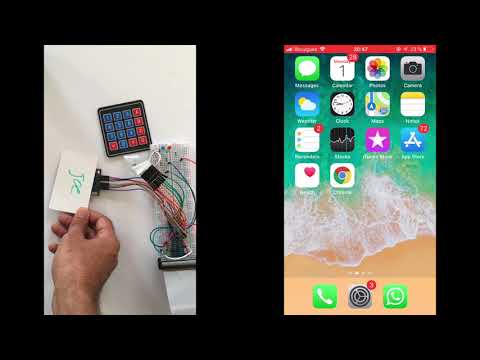
Hold a tag near the reader
Note: please make sure to update the keys for Duo in the code and export a variable for the Webex Teams token.
- User puts the RFID tag on the reader
- User approves the Duo authorisation notification
- User is granted access
- User presents a new RFID tag to reader
- User is not granted access
- Enrollment process is sent over Webex Teams for new user
- User puts the RFID tag on the reader
- Duo autorisation does NOT happen (timeout, connectivity...)
- Pin is generated and sent through Webex Teams
- User is granted access using a PIN code