New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[Bug]: fork/exec terraform-profider-aws: permission denied #30227
Comments
Community NoteVoting for Prioritization
Volunteering to Work on This Issue
|
|
Hey @robertolopezlopez 👋 It looks like based on the linked issue, this is likely a (local) permissions issue. Have there been any modifications to the permissions on the |
|
Hi Justin,
I checked permissions and ownership for the respective AWS provider binary.
It seemed ok: full permissions for that user.
I repeated the process several times by deleting .terraform directory and
rerunning terraform init. Same error after.
On the other hand, I tried to downgrade the AWS provider to 4.3.0. This
time, I was able to execute terraform apply without any issue.
Thus, this problem looks to me like a bug introduced in the AWS provider
after v4.3.0.
Environment: Ubuntu 20.04 + amd64 architecture.
Please don't hesitate to contact me if you have any questions.
Regards,
Roberto
…On Thu, Mar 23, 2023, 16:33 Justin Retzolk ***@***.***> wrote:
Hey @robertolopezlopez <https://github.com/robertolopezlopez> 👋 It looks
like based on the linked issue, this is likely a (local) permissions issue.
Have there been any modifications to the .terraform directory's
permissions?
—
Reply to this email directly, view it on GitHub
<#30227 (comment)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/AALS623FN45ZCY7OU734PUDW5RUL5ANCNFSM6AAAAAAWFEXZX4>
.
You are receiving this because you were mentioned.Message ID:
***@***.***>
|
|
I may be interested on fixing this problem myself :-)
…On Thu, Mar 23, 2023, 16:33 Justin Retzolk ***@***.***> wrote:
Hey @robertolopezlopez <https://github.com/robertolopezlopez> 👋 It looks
like based on the linked issue, this is likely a (local) permissions issue.
Have there been any modifications to the .terraform directory's
permissions?
—
Reply to this email directly, view it on GitHub
<#30227 (comment)>,
or unsubscribe
<https://github.com/notifications/unsubscribe-auth/AALS623FN45ZCY7OU734PUDW5RUL5ANCNFSM6AAAAAAWFEXZX4>
.
You are receiving this because you were mentioned.Message ID:
***@***.***>
|
Maybe I chose a bad issue to link :-/ I tried the proposed solution over and over, and nothing changed. Just downgrading the aws provider fixed this problem. On the other hand, as mentioned in my previous answer, in my case this is not running on azure pipelines but locally on my desktop work machine (more precisely: ubuntu 20.04 amd64 inside of virtualbox+vagrant+w11) |
|
Hi @justinretzolk , sorry for my multiple comments above. I took my time to find out which is the exact minor revision which introduced this bug. |





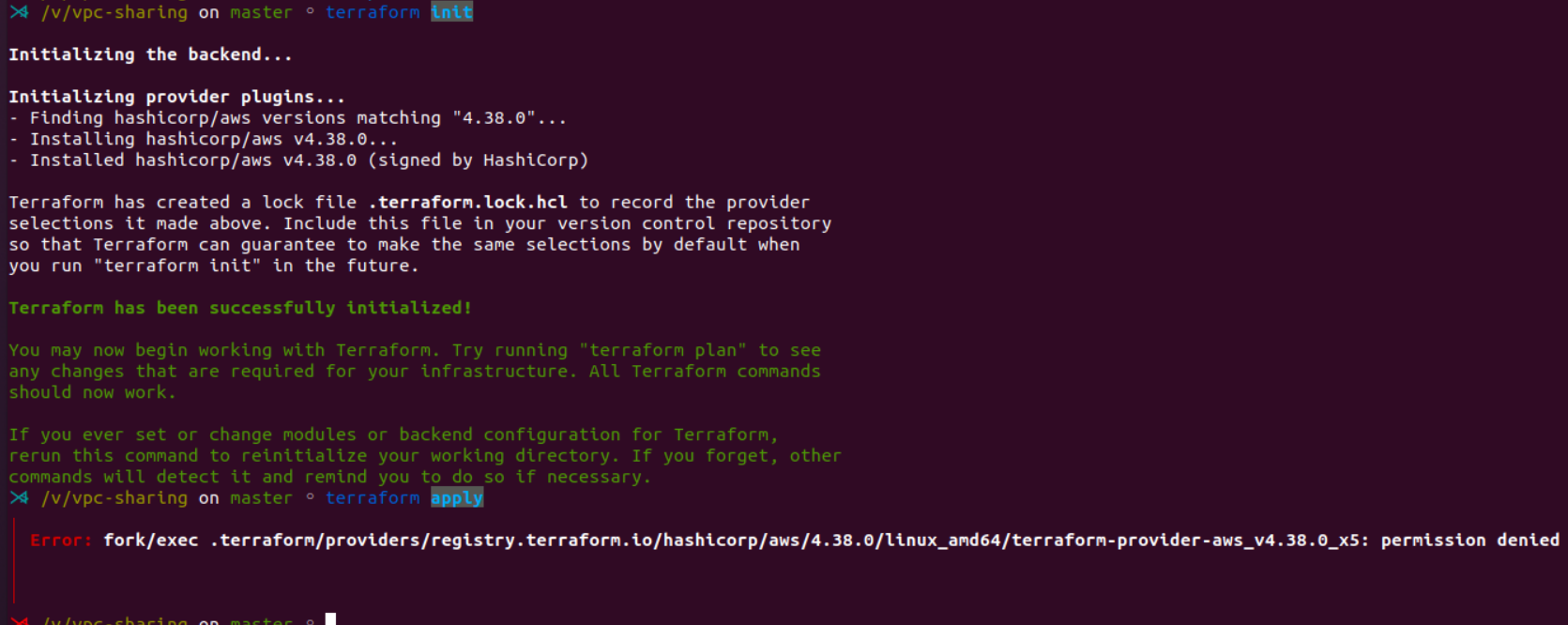
Terraform Core Version
v1.4.2
AWS Provider Version
From v4.38.0
Affected Resource(s)
No response
Expected Behavior
successful terraform init
Actual Behavior
Error: fork/exec .terraform/providers/registry.terraform.io/hashicorp/aws/4.59.0/linux_amd64/terraform-provider-aws_v4.59.0_x5: permission denied
Relevant Error/Panic Output Snippet
No response
Terraform Configuration Files
vpc-sharing.zip
Steps to Reproduce
Debug Output
No response
Panic Output
No response
Important Factoids
No response
References
hashicorp/terraform#24010
Would you like to implement a fix?
Yes
The text was updated successfully, but these errors were encountered: