-
-
Notifications
You must be signed in to change notification settings - Fork 1.4k
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
IKEv2 fails to connect with NO_PROPOSAL_CHOSEN (Docker Image) #298
Comments
|
@NLJM Hello! What is your Docker host's Linux distribution and version? I could not reproduce this issue on a Ubuntu 22.04 Docker host with the Alpine-based hwdsl2/ipsec-vpn-server Docker image. IKEv2 works fine in my tests. Your logs show [1] https://github.com/hwdsl2/docker-ipsec-vpn-server#update-docker-image |
|
Hi @hwdsl2, I am running Docker version 20.10.3, build 55f0773 on a Synolgoy NAS (DSM 7.1-42661 Update 1). Everything is updated to the most recent verslons (DSM, Docker and Docker Image). I've recreated the container without --priviledged and now I am getting the pluto logs: 2022-06-16T16:43:00.852183+00:00 05be34b19461 pluto[374]: packet from 172.18.0.1:41287: ISAKMP_v2_IKE_SA_INIT message received on 172.18.0.15:500 but no suitable connection found with IKEv2 policy Ok, it seems Synology doesn't support MOBIKE. After disabling it it does connect however for some reason my Synology crashes completely and reboots. So I guess it is requesting access to some resource it can't handle. |
|
@NLJM Thanks for the update! Regarding MOBIKE, I think you're right. The IKEv2 setup script (which runs as part of the Docker container initialization) cannot currently detect Synology host OS from within the Docker container (although it can try to detect e.g. Ubuntu). When MOBIKE is set to "on" on an unsupported OS, the IKEv2 connection will fail to initialize and not be enabled. Turning off MOBIKE manually in ikev2.conf resolves it. But it looks like Synology doesn't support running IKEv2 in the Docker container due to other reasons, as you mentioned. |
- Disable MOBIKE when running on Synology NAS. MOBIKE is not supported on these systems and prevents IKEv2 from working if enabled. Ref: hwdsl2/docker-ipsec-vpn-server#298
- Improve MOBIKE detection by checking whether the IKEv2 connection is successfully loaded. If not, the server's Linux kernel may not support MOBIKE, and we disable it in ikev2.conf. - This will help prevent the issue where the IKEv2 connection fails to load on some systems due to lack of MOBIKE support. Note that the script already has checks for MOBIKE support that cover common cases. - Related issues: hwdsl2/docker-ipsec-vpn-server#330 hwdsl2/docker-ipsec-vpn-server#298 hwdsl2/docker-ipsec-vpn-server#247
Describe the issue
I am running the docker container using auto-setup. Am able to connect to the VPN using Cisco IPSec however IKEv2 is not happening.
To Reproduce
Steps to reproduce the behavior:
When I try to connect using Cisco IPSec the VPN is working.
Expected behavior
I expect IKEv2 to connect.
Logs
This is all I get in the logs.
1cb06121aa01:/opt/src# grep pluto /var/log/messages
2022-06-14T16:40:59.626148+00:00 1cb06121aa01 /etc/init.d/ipsec[1877]: checkpath: /var/run/pluto: could not open run: No such device or address
2022-06-14T16:42:21.540793+00:00 1cb06121aa01 /etc/init.d/ipsec[229]: checkpath: /var/run/pluto: could not open run: No such device or address
1cb06121aa01:/opt/src#
I did however also trace on my macOS using wireshark
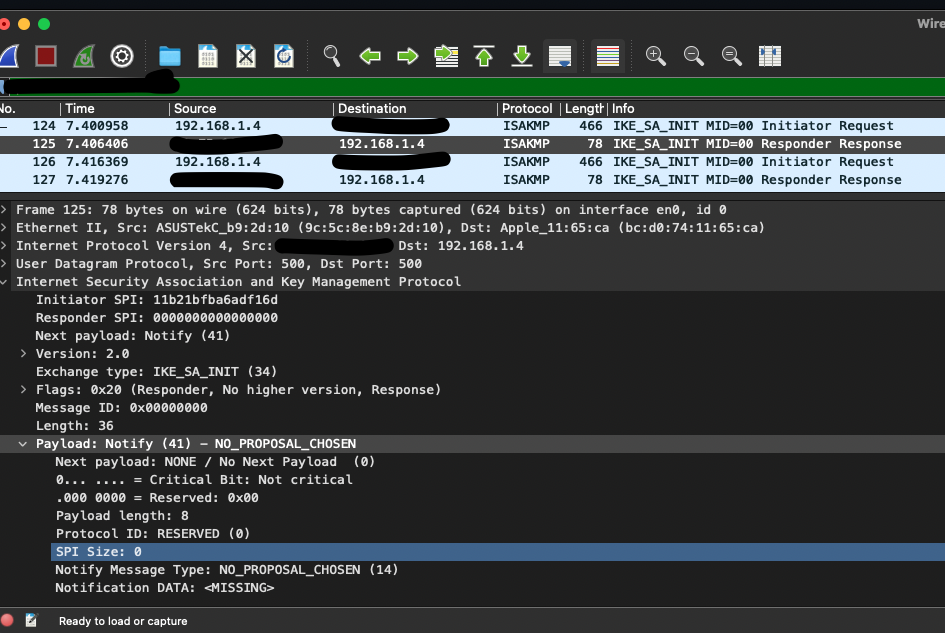
Server (please complete the following information)
Client (please complete the following information)
Client (please complete the following information)
The text was updated successfully, but these errors were encountered: