Runtime merge proposal #33
Comments
|
Thank you for submitting the proposal @sameo :) |
|
Add some basic goals of the merging proposal:
|
|
@gnawux Done, please let me know if that looks fine to you. |
|
Thanks @sameo! lgtm |
|
cc @jon |
|
This seems sane to me! |
I didn't see that listed below, or is that the same thing as
Would it be possible to list the specific places it falls short here? Or would that require a more involved analysis?
I'd be interested in seeing a bit more justification for this, even if it's just one sentence. What's the alternative, and why is this preferred? |
virtcontainers is where the entire Clear Containers logic lives. The Clear Containers runtime ( Do you feel that's clearer? |
It needs some further analysis. We need to compare the current virtcontainers API with PR #32 to fully where the gaps are, if any. |
|
Thanks for clarifying. LGTM. |
|
What about multi-architecture support? The above summary seems to only mention multi-hypervisor support. The runV hypervisor driver is both hypervisor-agonistic and architecture-agonistic. It has support for ARM64, AMD64, PPC64 and s390x. Are we going to only keep the hypervisor-agonistic part of it? |
@tallclair Not just the VM factory. The entire set of API is being discussed here #32 |
|
This LGTM, I like this idea. One thing, currently |
|
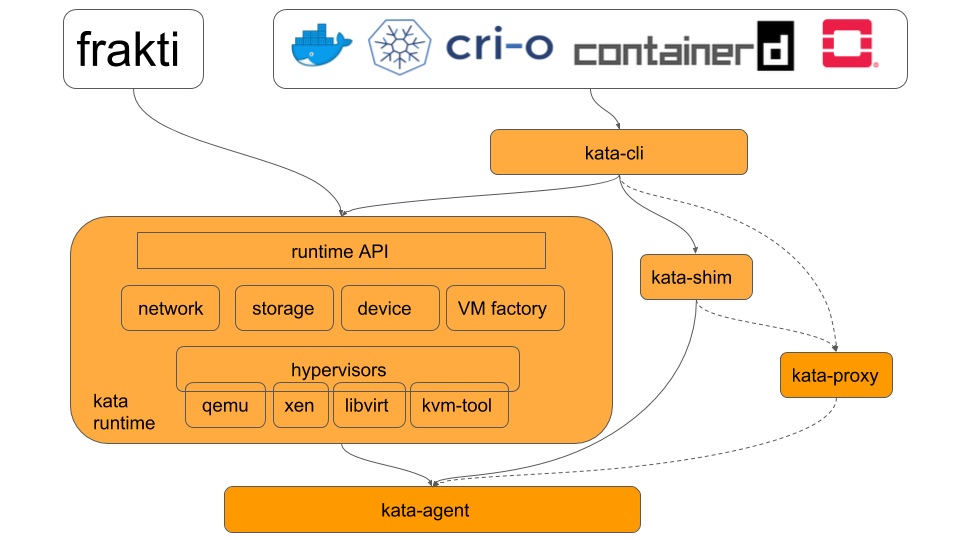
@sameo one nit about the architecture graph -- the agent/shim/proxy are outside of virtcontainers and shim/proxy are not used by frakti. |
Certainly not. It has to be architecture agnostic as well, and as an example we recently merged ARM support for QEMU into the virtcontainers. I'll add a mention to it to the proposal, thanks. |
We initially put I will send a PR for that purpose tomorrow or early next week, I first need to know what was the output of yesterday's discussion on this proposal. |
Right, what I meant with this diagram is to show that virtcontainers provide support for managing different kind of proxies, shims and agents. Not that the proxies and shims implementations are done inside virtcontainers. Not sure how to make that clearer with such high level diagram though... |
How about renaming virtcontainers to kata-runtime, and kata-runtime in the graph to kata-cli? Then we can link shim/proxy under kata-cli and agent under kata-runtime. Current separation of kata-runtime and virtcontainers makes it unclear because virtcontainers essentially is part of kata-runtime. |
|
@sameo I've drawn a sample architecture graph based on the above suggestion. Please feel free to modify or use it directly. The components in orange are kata components. |
This is a virtcontainers 1.0.7 import into Kata Containers runtime. virtcontainers is a Go library designed to manage hardware virtualized pods and containers. It is the core Clear Containers framework and will become the core Kata Containers framework, as discussed at kata-containers#33 Some more more pointers: virtcontainers README, including some design and architecure notes: https://github.com/containers/virtcontainers/blob/master/README.md virtcontainers 1.0 API: https://github.com/containers/virtcontainers/blob/master/documentation/api/1.0/api.md Fixes kata-containers#40 Signed-off-by: Samuel Ortiz <sameo@linux.intel.com>
This is a virtcontainers 1.0.8 import into Kata Containers runtime. virtcontainers is a Go library designed to manage hardware virtualized pods and containers. It is the core Clear Containers framework and will become the core Kata Containers framework, as discussed at kata-containers#33 Some more more pointers: virtcontainers README, including some design and architecure notes: https://github.com/containers/virtcontainers/blob/master/README.md virtcontainers 1.0 API: https://github.com/containers/virtcontainers/blob/master/documentation/api/1.0/api.md Fixes kata-containers#40 Signed-off-by: Samuel Ortiz <sameo@linux.intel.com>
|
Since we have the initial requirements pr merged and virtcontainers is now merged, can this issue be closed? I'll open a new issue to detail vm templating. |
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
- Add kata-runtime - Add unit test - Add Makefile to build cli Fixes: #33 Signed-off-by: Julio Montes <julio.montes@intel.com> Signed-off-by: James O. D. Hunt <james.o.hunt@intel.com> Signed-off-by: Jose Carlos Venegas Munoz <jose.carlos.venegas.munoz@intel.com>
CoC: Add Code Of Conduct
Problem Statement
The Kata Containers project is a merge of 2 hardware virtualization based runtimes: Intel’s Clear Containers and Hyper’s runV. As of Feb 13th, 2018, the two runtimes live alongside under the Kata Containers runtime github repository. Having two codebases is confusing the community and impeding potential contributors to really commit to the project.
Although each runtime has its strengths and gaps, the next step for the Kata Containers project should be about combining the two runtimes into a single code base, and merging each runtime feature set into a larger one.
To reach that goal, these two approaches are proposed:
During the Feb 5th, 2018 Kata Containers Architecture meeting, the community decided to initially go with the first solution, i.e. picking one runtime over the other.
We believe this solution is a little too aggressive and may underestimate the engineering costs of filling the technical gaps of either runtime.
Goals
The goal of this proposal is to show that the second approach is viable and can be implemented. We think by mixing the best of the two runtime components we can accelerate the runtime merging process and reach the Kata Containers 1.0 release sooner.
This proposal aims at:
High Level Architecture
By picking the virtcontainers framework that already implements the entire Clear Containers feature set, together with the runV hypervisor drivers, VM factory library and runtime API, we would combine the 2 runtimes features sets. Building the Kata Containers runtime on this combination of components would thus fulfill the Kata Containers runtime requirements.
The Kata Containers runtime would then be based on the following components:
The text was updated successfully, but these errors were encountered: