New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Your web server is not properly set up to resolve "/.well-known/webfinger". #189
Your web server is not properly set up to resolve "/.well-known/webfinger". #189
Comments
|
Could you do a couple things please:
|
|
Can't reproduce. Works fine here. Browse to |
Linuxserver.io version:- 21.0.0-ls124 Build-date:- 2021-02-25T19:56:09+00:00
|
|
On Chrome One redirects to public.php and the other to index.php |
|
redirects are 301 (permanent), which are cached by the browser. You need to clear your browser cache for it to redirect to the new urls that nextcloud v21 expects to see |
I had tried cleaning everything from cache to storage for this domain, even cleaned windows dns and firewalls dns. Thanks for your time. |
|
Clearing the cache doesn't work for all scenarios and this should be re-opened and investigated more thoroughly. For example, I am using the swag container as a reverse proxy to my nextcloud container and this still happens. It happens even if I change the nextcloud configuration like here # Make a regex exception for `/.well-known` so that clients can still
# access it despite the existence of the regex rule
# `location ~ /(\.|autotest|...)` which would otherwise handle requests
# for `/.well-known`.
location ^~ /.well-known {
# The following 6 rules are borrowed from `.htaccess`
location = /.well-known/carddav { return 301 /remote.php/dav/; }
location = /.well-known/caldav { return 301 /remote.php/dav/; }
# Anything else is dynamically handled by Nextcloud
location ^~ /.well-known { return 301 /index.php$uri; }
try_files $uri $uri/ =404;
} |
|
Are you using subfolder? Then that's the reason. |
|
I am not using subfolder. That is why it needs to be investigated more thoroughly. |
|
We don't see the issue when setting up a new container and all of our existing ones updated to latest doesn't have it either. So it's hard to troubleshoot more when we don't have the issue. |
|
Dang it. My apologies, I missed this thread For anyone still having issues, change the default nginx config for the container if you've been using the same container for a long time. |
|
Lol. It's even in this issue. |
|
Ya, maybe you should make it more clear or perhaps create some documentation for changing the configuration. LOL |
|
I honestly don't know how to make it any clearer? https://github.com/linuxserver/docker-nextcloud#versions It says: |
|
Ah, I see. You would expect me to go searching all over the repo for the answer and skip the issue all together. Great. But I don't understand how you can't see that as unclear. In this case, viewing an issue with many comments is not practical BECAUSE it leaves the read to miss things. To make it more clear, once a workaround for the issue is discovered it should be linked in the initial issue. This keeps a person researching the error from having to sift through a bunch of investigative posts. Because, the thread that updates the config looks like someone providing the configuration for investigation. I believe it is common practice to update the initial issue with the workaround if one is found too. Additionally, I apologized for my mistake in assuming that the configuration followed the application's direct documentation. It would make it more helpful for people asking for clarity to not reply with with LOL's and sarcastic assumptions. Instead, reply with a direct link to the release notes that articulate this information. Wouldn't you agree? |
|
Well, before you update ANY software, you should read the changelog. If you didn't and this caused problems, it's not developers fault, it's the administrator that did the update. The changelog was there BEFORE the release. So, no it's not a workaround it's an info provided along with the release. And no, they can't just put a script to delete the old config and replace with the new. Some people have custom configs in there. Just a friendly reminder to read changes before updating something :) PS. I have nothing to do with the LSIO team. |
|
That's not at all what I was expecting. I would never expect them to create a script to delete the old config in a docker environment. Docker environments are supposed to be immutable and since the updates happen outside of the docker environment I assumed that the container just used the default configuration. However, I was asked how to make it more clear. In my opinion, to make it more clear, elaborate the fix in the original issue thread. That's all I am saying. Arguing about who is at fault or responsible is not what I am talking about. I already apologized and assumed partial responsibility for not reading the whole thread. Don't get me wrong. I understand that open source is hard and I am not expecting that everything be handed to us. I am just saying that it could have been documented better. Accept the feedback or don't and make adjustments or don't. Simple as that. In either case, next time I update your containers, I will make sure to do it very cautiously. |
Just to avoid any misunderstandings. |
@tobbenb: Iam using SWAG + NC subfolder and I still have this problem. Deleted the configs and also tested with a PC that never opened nextcloud before. So is this error normal with subfolder and is there a way to fix it? |
|
You have to edit the proxy conf and add the fixes from the subdomain conf. I'll see if I find the fix I posted on Discord. |
|
Found it. Can you try to replace the below in your nextcloud.subfolder.conf Change it to: |
|
Yes, its working now, thanks alot :-) |
|
I'll update the subfolder conf then. |
|
Bump |
|
Hey everyone came across this post which clears up subfolder use...what about subdomain? I am using Nginx Proxy Manager when i added the following to my custom nginxconfig i get more warnings than just the webfinger and nodeinfo b ut also for the carddev and caldev When i rename the default.conf file in /appdata/nextcloud/nginx/site-confs/ the site becomes no longer available I am using HSTS and all the security trimming that are free at Cloudflare anyone got a fix while using Cloudflare proxied DNS CNAMES and a subfolder with nginx proxy manager |
|
found a fix here added all to my NPM custom config and did a force refresh in chrome with crtl reload button and all checks pass now |
|
Unfortunately none of the above fixes this in NC version 25.0.6. nginx version is 1.18, php-fpm is 7.4. A similar setup with Apache using Please let me know if more information is required. |
|
This is a 2 year old post. The webfinger stuff went through so many iterations during that time. The setting in the nextcloud image's default site conf is correct and is sufficient. You don't have to change anything manually. Just make sure NC is using the latest site conf. Check the container log to see if that's the case. You can open a new issue or visit our discord if you're still having issues. Locking this issue |




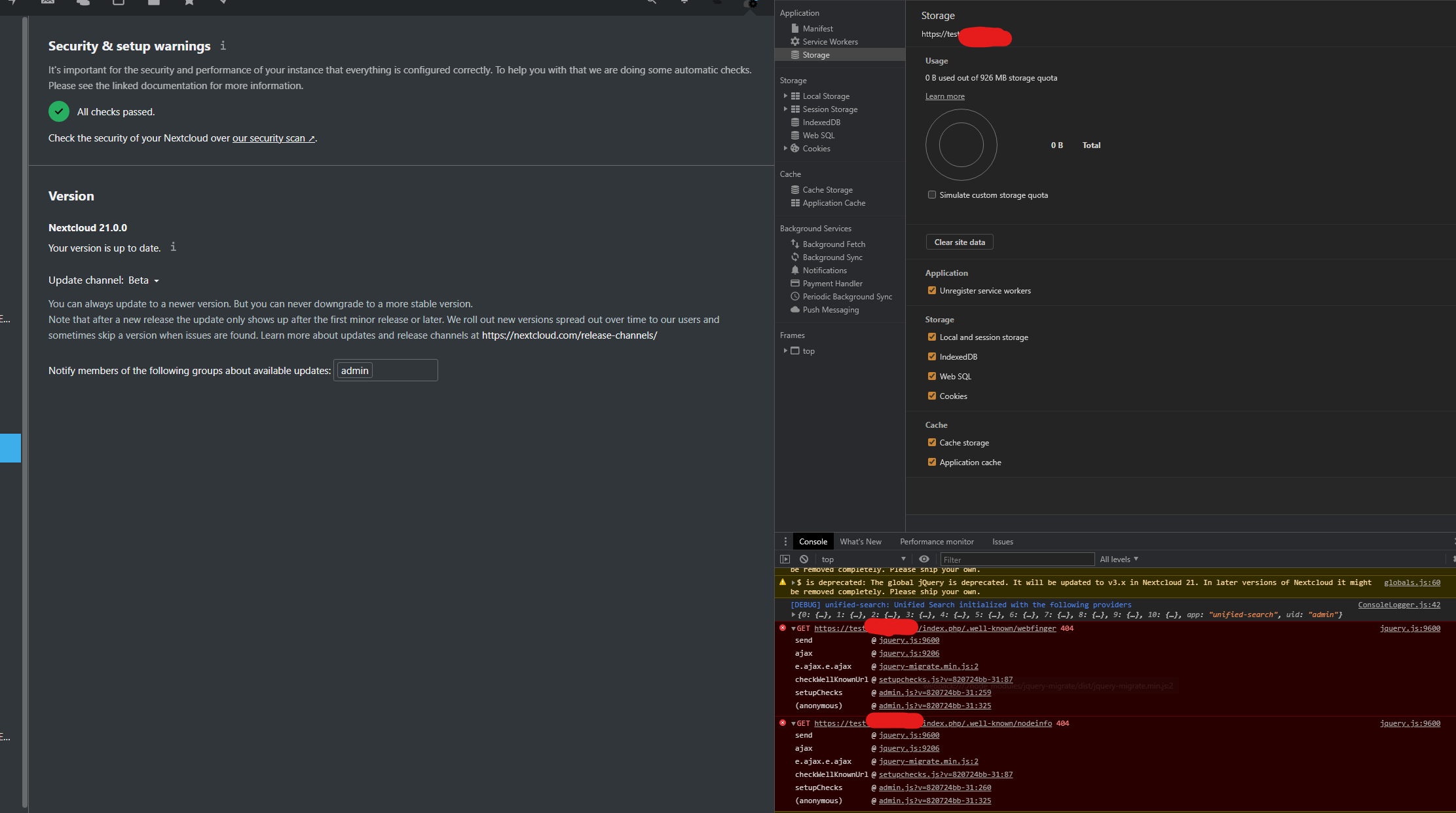
Continuing from #185, the #188 PR has fixed the warning about nodeinfo but not webfinger.
Expected Behavior
Checks pass all tests
Current Behavior
Checks return warning
Your web server is not properly set up to resolve "/.well-known/webfinger".
Steps to Reproduce
Environment
OS: Unraid 6.9.0 rc2
CPU architecture: x86_64
How docker service was installed: Installed from Community apps
Command used to create docker container (run/create/compose/screenshot)
Docker logs
The text was updated successfully, but these errors were encountered: