Today I will be demonstrating a XSS Vulnerability in Rukovoditel 3.1. Rukovoditel is a free web-based open source project management application.
This vulnerabity was found by Kubozz.
GitHub Documentation
Download Rukovoditel 3.1 Below with XAMPP. XAMPP is an open source web-server solution. XAMPP launches the Ruko webserver.
https://sourceforge.net/projects/rukovoditel/files/rukovoditel_3.1_xampp_php7.4.zip/download
After downloading, be sure to extract the packages to your C: Drive
Navigate to your C: Drive.
Locate and open the folder:
xampp
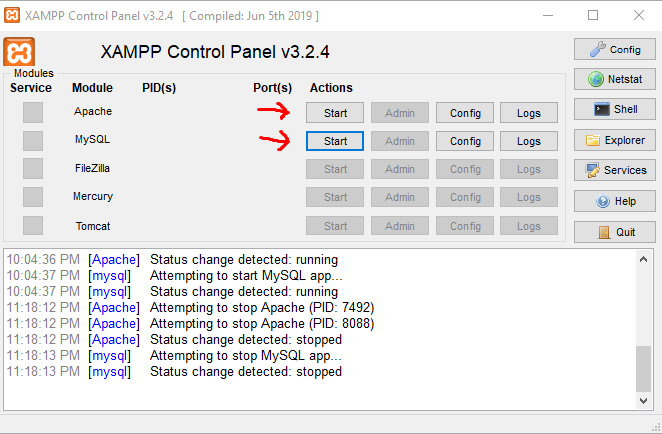
Locate and open the application:
xampp-control
Click Start for Apache and MYSQL Server.
Navigate to this address on your Chromium Browser.
localhost/ruko
Login using these credentials.
user: admin
password: admin
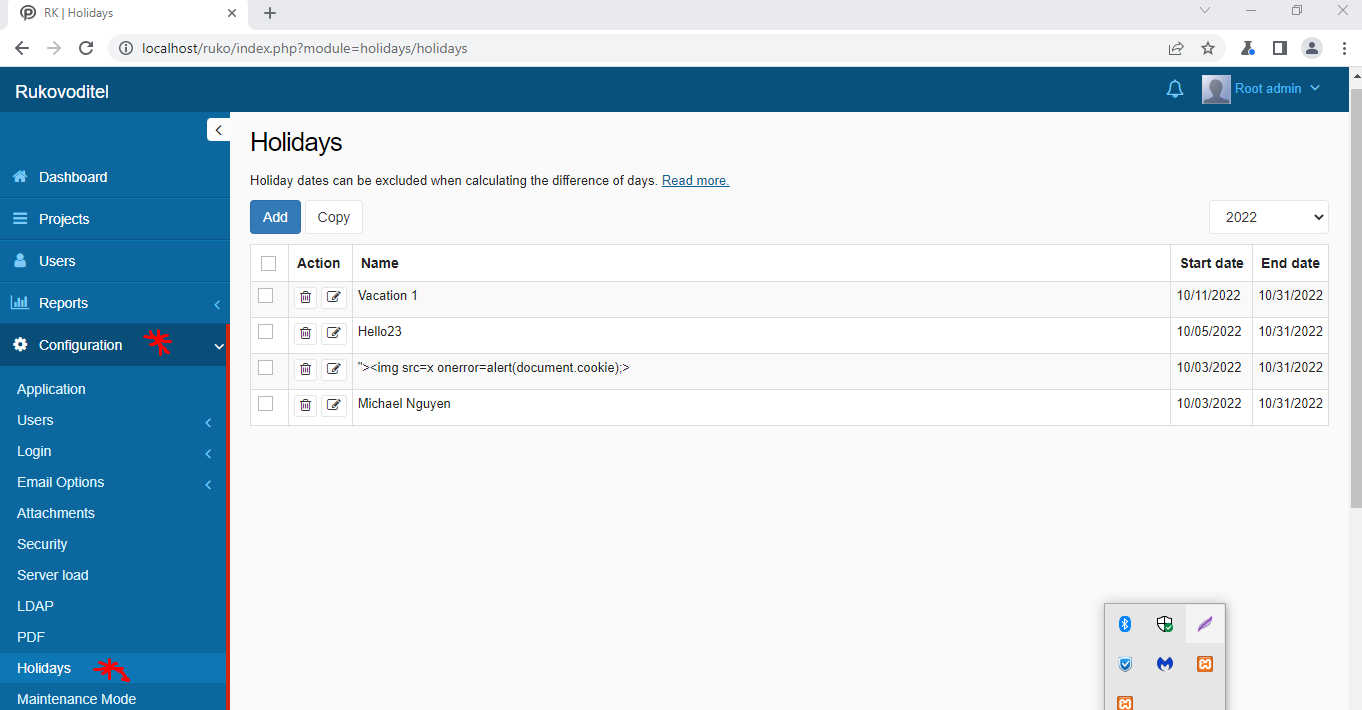
Navigate to Configurations -> Hoildays.
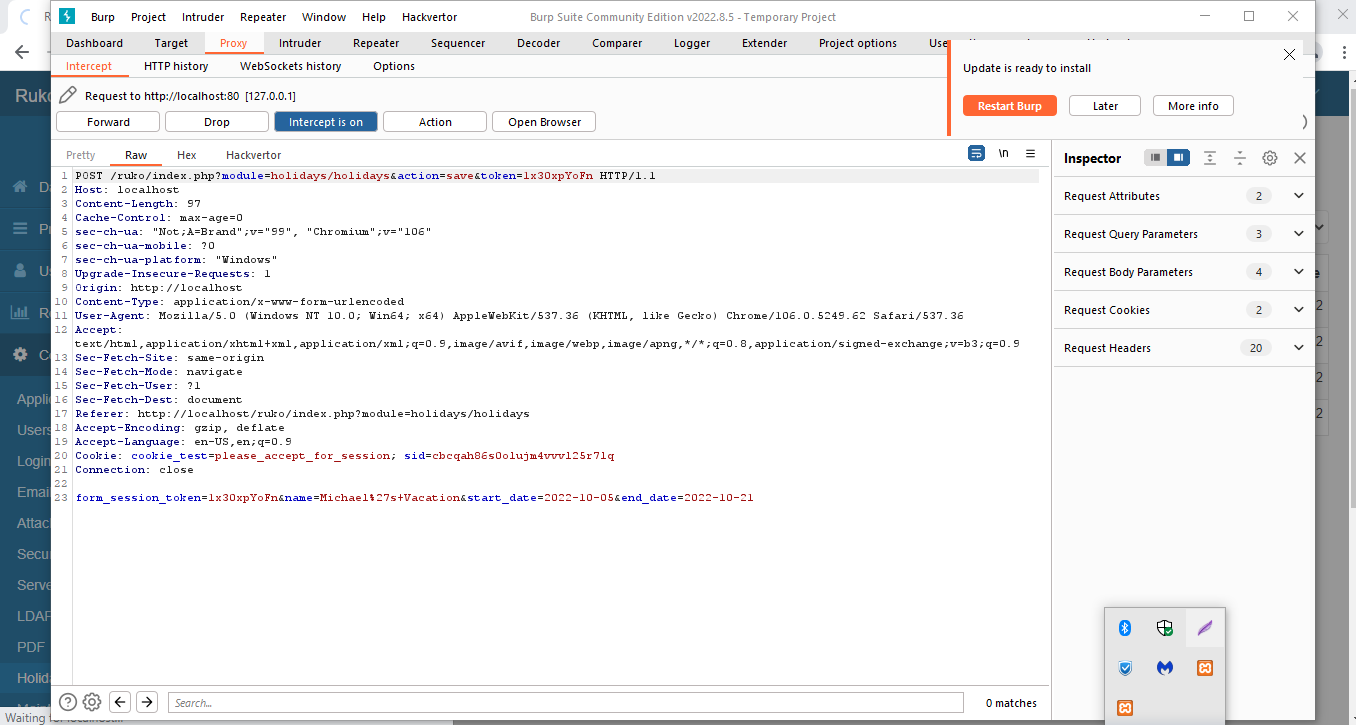
Use Burpsuite to intercept browser.
Click Add and test out request.
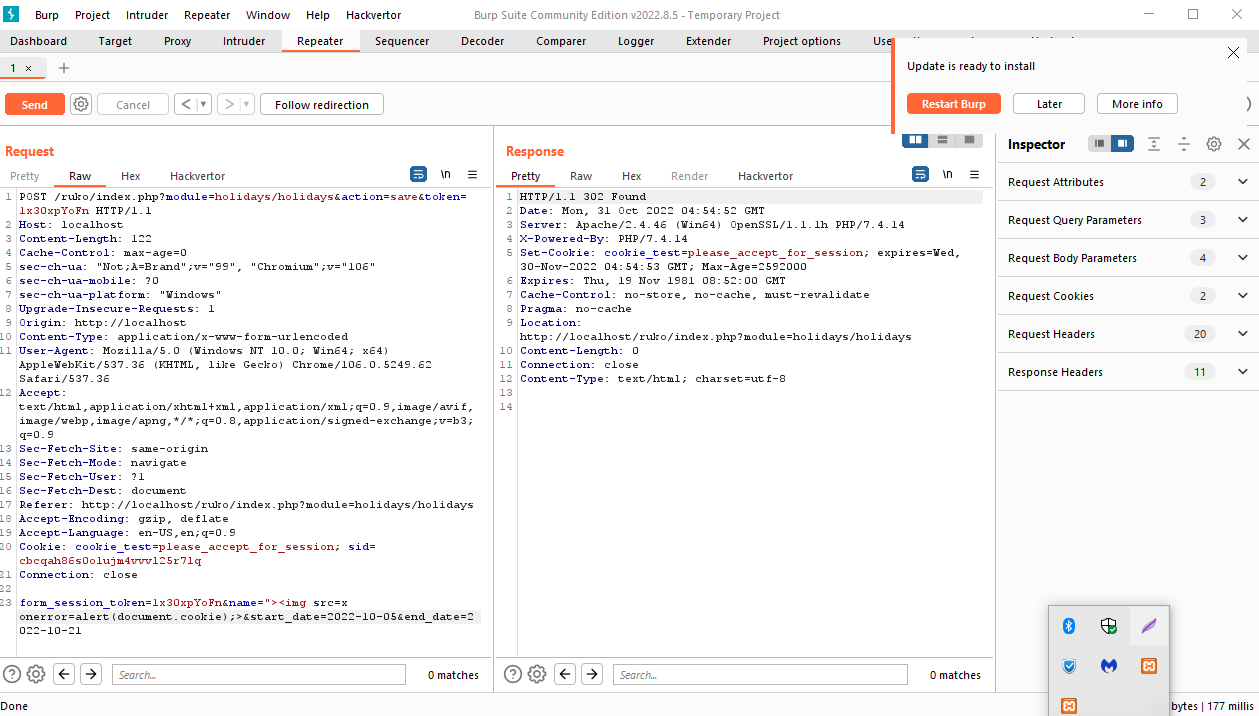
Send Request to the Repeater and test out Response.
Kubozz states that the vulnerability is in the name parameter.
They state that we can make use of the onerror event handler.
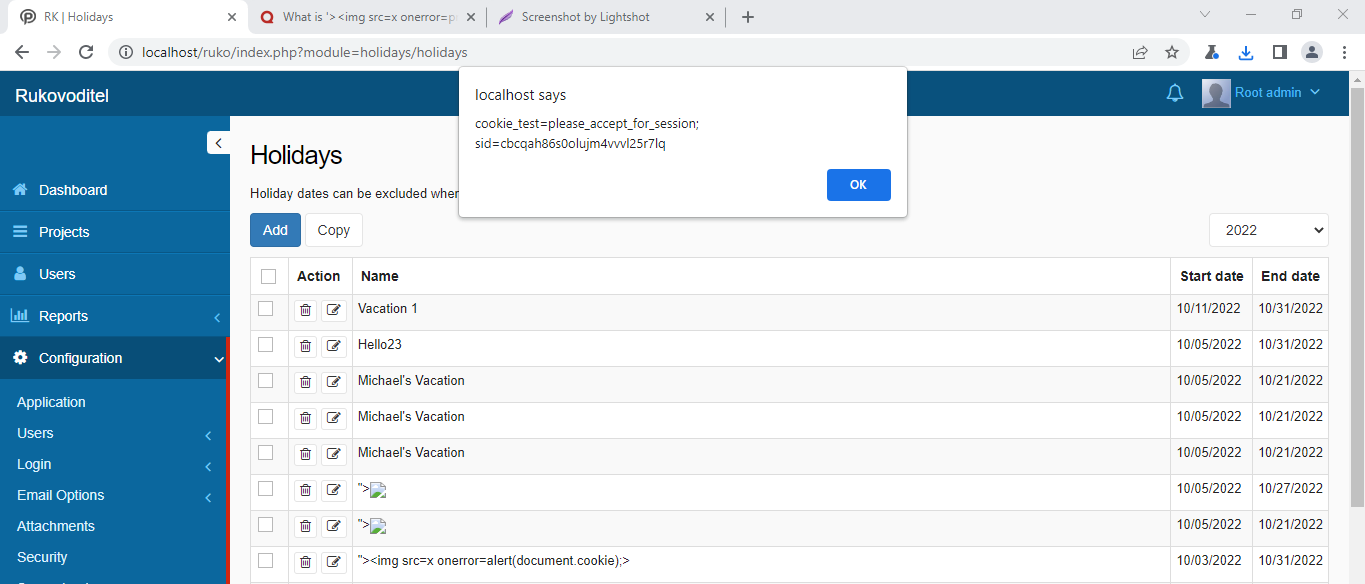
Here is a sample payload that we can use for the name parameter to return the current session cookie.
This payload will make the browser ouput "1" to the page.
An attacker with admin privleges could make use of this vulnerability. These paylods are stored into the web servers database so everytime this page is loaded, these scripts will run one by one.
Kubozz states that the name parameter is vulnerable because the parameter does not encode any output that is reflected back to the page. Removal of script tags is not enough.
First, stop the web server.
Go to your C: Drive and open xampp in VS Code(Preferred)
Finding the actual source code for the vulnerable page was tricky because I cannot execute(or could not figure out how) the code to launch the webserver. Nevertheless, I found the source code for the page.
Go to this path.
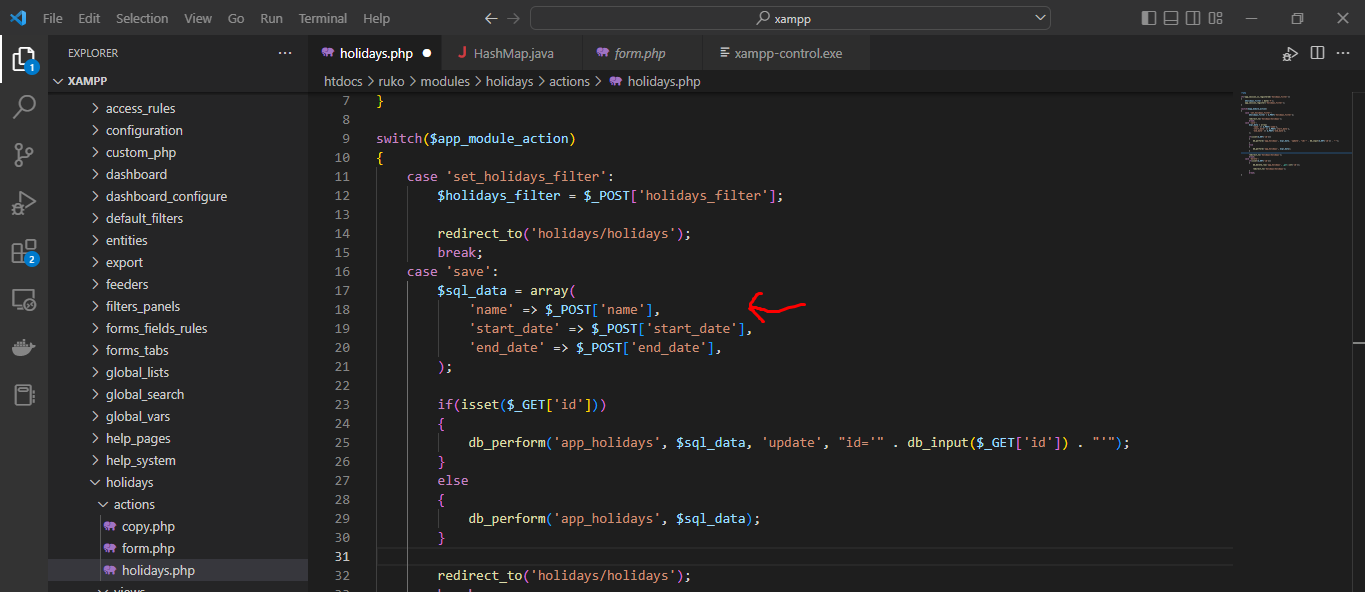
C:\xampp\htdocs\ruko\modules\holidays\actions\holidays.php
As we see in the source code, the web page uses PHP scripting language.
Go to line 18 of holidays.php and observe that the name parameter does not use HTML Entity Encoded to encode any output to the webpage after submitted a holiday.
'name' => ($_POST['name']),
I am not familiar with PHP scripting language but after doing research. I found out the proper way to encode the name parameter.
This how you would encode the name parameter. Replace line 18 with the following code.
'name' => htmlspecialchars($_POST['name']),
After replacing the code. Save the code.
Relaunch the web server using XAMPP.
Navigate yourself back to vulnerable page and you should notice that the previous payloads do not work because the name parameter now encodes any output to the page.