Hi! I'm *Muhammad Abdullah*, a Pentester || Linux Admin || Cybersecurity Consultant || IT Support Technician.
- 💻 My laptop runs on Windows 10 Pro
- 👨💻 For my terminal, I use Kali Linux and Parrot Security.
- 🛠️ For IDEs, I use Visual Studio code, and Python for scripting.
- 🐳 For containerization, I use Docker.
- 🌊 Currently, I post all my blogs to a Medium.
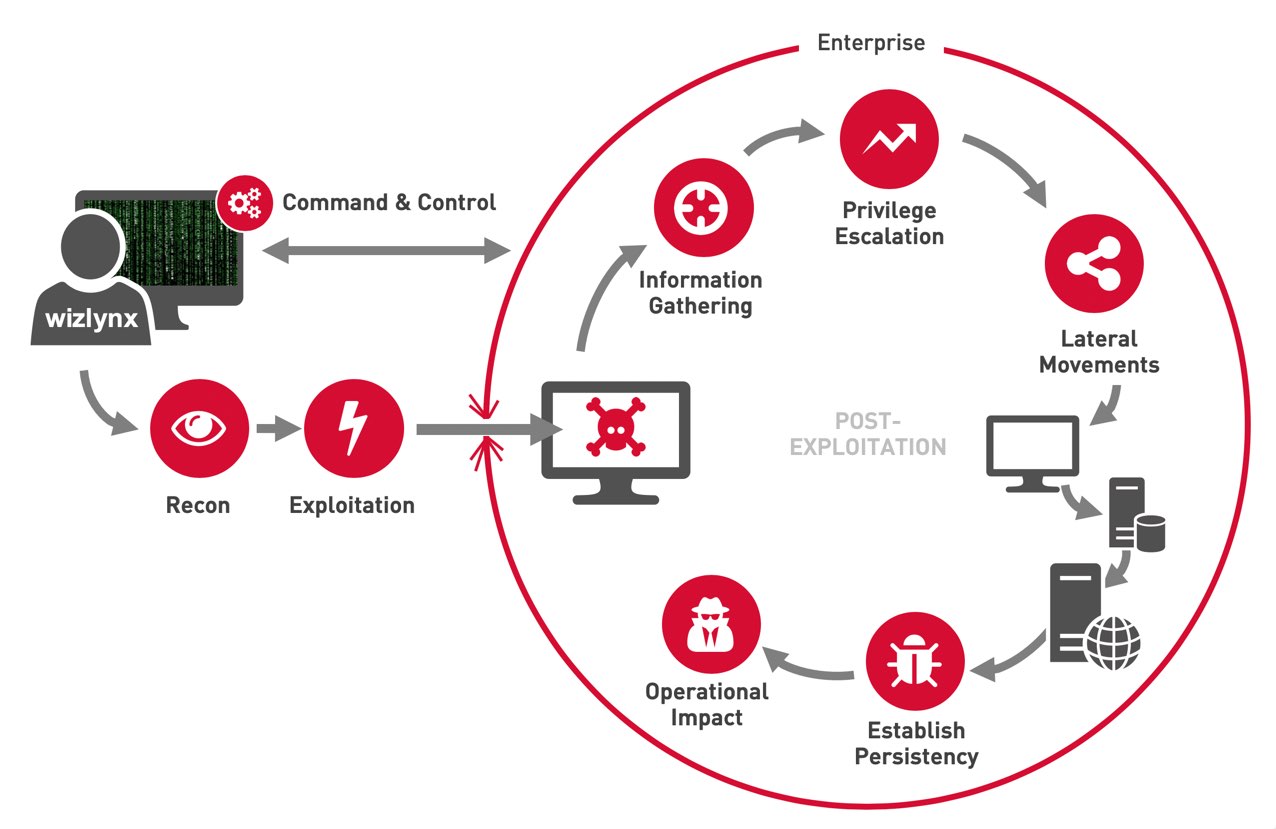
- 📘 If working on a defense side, I would most likely use Nessus, OpenVas, snort, and MITRE framework.
- 📕 If working on an offensive side, I would most likely use Nmap, Nikto, Burp Suite, Metasploit, and Python for workflow automation.
- 🏫 University Lately, I developed a Linux GUI application using Python to automate banner grabbing and vulnerability analysis. The application simplified essential cybersecurity tasks, including Network Scanning, Subdomain Enumeration, Content Discovery, Web Analysis, Technology Detection, and Vulnerability Analysis. It also provided comprehensive reporting for these tasks.
- 🏴Capturing the flags on tryhackme and HTB.
- 🔨 If you want to read more about some of the blogs I've written on, visit my online Blogging Site.
- 🏫 I'm doing the Red Team Path on TryHackme and also capturing the flag (CTF) rooms.
- 💻 Tryhackme is a great hands-on online platform by Ashu Savani and Ben Spring. When examining TryHackMe's stellar reputation within the cyber security sector on multiple platforms, it's clear that it is extraordinarily well suited to newbies.
- 🐍 Effective Python by Brett Slatkin is a great book full of advice that will help anyone write better Python code. The book contains a bunch of self-contained lessons that shine a light into the language strengths and expressiveness. It is truly excellent!
- 🦈 OverTheWire by Steven Van Acker Through engaging games, the OverTheWire community can assist you in learning and applying security ideas. They provide a variety of wargames to improve your skills.
- ⏰ Cracking the Coding Interview. This book is pretty dense, but it's an excellent resource for preparing for a technical interview in any language.
- 🤝 To learn more about my journey, visit my LinkedIn profile, and let's connect. I'm always happy to chat with fellow developers.