-
Notifications
You must be signed in to change notification settings - Fork 150
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Websocket support #513
Websocket support #513
Conversation
653ebbb
to
5a118fe
Compare
|
The only issue with this so far is in regards to using proxies that require authentication. If a proxy requires authentication, you can call However, this is also effectively a global variable, and thus impacts any usage of To mitigate this, we could define an option used to construct a new |
6e642a1
to
a913657
Compare
…called which was caused by the websocket "close body" to be returned from the input stream.
a913657
to
0c19373
Compare
|
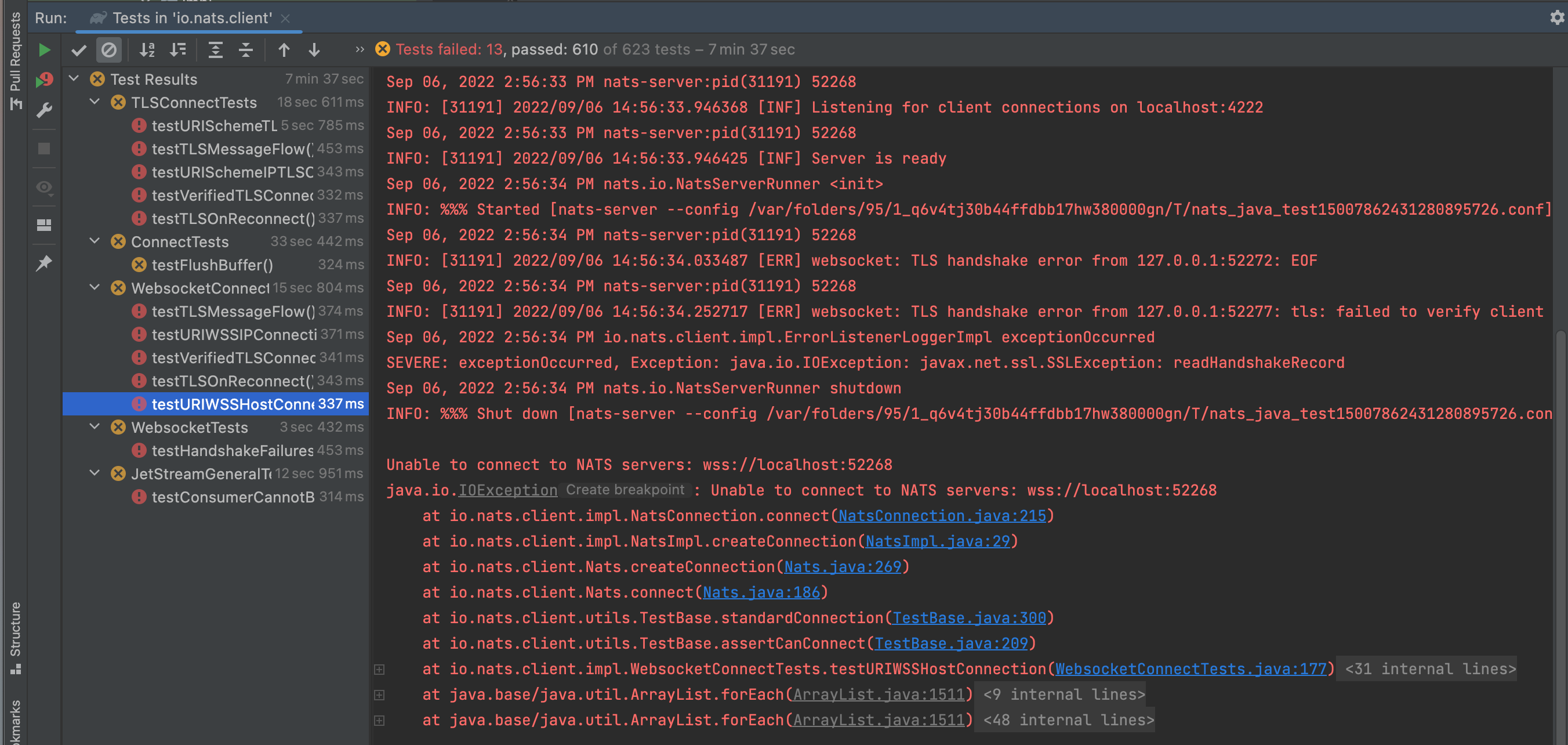
Tried to review this. Checked out the branch, and the WebSocket tests were failing. There were 13 WebSocket tests that are failing. |
|
Hi @RichardHightower what tests where failing? Last time I checked out the branch the tests succeeded, although some of the tests are unreliable (not due to the websocket code, just in general some of the tests have been unreliable in the past... and I even put together some PRs in the past to fix those). |
|
@brimworks We are revisiting this as a review of open PR's with some work we are considering doing to add in Vert-x. I though your interface changes might be re-usable or at least a roadmap. I will try to get to the conflicts, they look to be relatively minor. |
|
Closing this in favor of #826 ...as that seems to be the path forward. Thanks for moving this along! |
This is the simplest possible implementation of websockets with a net increase in code coverage.
I'm planning to use these changes in our production environment within the next few weeks.
Being critical of myself, these are the points that are lacking:
Sec-WebSocket-Extensions: permessage-deflate(aka websocket level compression... which should really be combined withNats-No-Masking: TRUEto really get the full benefits).Note that this PR replaces #426 which was posted before I had access to the
nats-io/nats.javarepository (and for some reason that other PR isn't working with coveralls).For more information on websockets, I'd really recommend reading the RFC: https://datatracker.ietf.org/doc/html/rfc6455
A 4x more complex PR which involves a DataPort refactor was posted here:
I've closed out the 4x more complex PRs, since the guiding principle that @scottf suggests is simplicity... and this is as simple as it gets.