New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
[BB-3622] Add course creation condition for organisation #26616
[BB-3622] Add course creation condition for organisation #26616
Conversation
|
Thanks for the pull request, @farhaanbukhsh! I've created OSPR-5631 to keep track of it in JIRA, where we prioritize reviews. Please note that it may take us up to several weeks or months to complete a review and merge your PR. Feel free to add as much of the following information to the ticket as you can:
All technical communication about the code itself will be done via the GitHub pull request interface. As a reminder, our process documentation is here. Please let us know once your PR is ready for our review and all tests are green. |
|
@farhaanbukhsh Thank you for your contribution. Please let me know once it is ready for our review. |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
👍 Can you remove the [WIP] tag from the PR and mark it ready by moving it out of the draft status?
- I tested the changes in this PR when reviewing [BB-3622] Restrict user create course open-craft/edx-platform#319 and verified that:
- Superusers and global staff users can always create courses in any organization with or without this feature flag enabled.
- When the feature flag is enabled, in addition to having the course creation permission via course creator groups (enabled by default), the user should also have a role (any role would suffice as the user is already a course creator) in the course's organization to be able to create a course under an organization.
- When the feature flag is disabled (the current and default behavior), the existing behavior allowing course creator users to create courses in all organizations is preserved.
- I read through the code
-
I checked for accessibility issuesNA -
Includes documentationNA
|
@farhaanbukhsh Is this ready for edX review? |
|
@natabene this PR is ready for review. :) Thanks for your patience. |
|
Thanks for your patience @farhaanbukhsh , I'll take a look at this soon! |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
First off, I think this feature is a great addition to CMS. It seems like a no-brainer that we should be able to restrict content creation based on org. Thanks for submitting this PR!
My concern is that we are adding it in a way that is orthogonal to the current content creation auth scheme. As far as I can tell, the current scheme is essentially:
- if
DISABLE_{COURSE,LIBRARY}_CREATION, reject all content creation, except for global staff. - if
ENABLE_CREATOR_GROUP, check if the user has theCourseCreatorRolerole. - Otherwise, allow all content creation.
But by building the org-based creation restriction using has_studio_write_access, we are instead checking the Instructor and Staff roles, which seem to be intended for already-created content. The resulting flow is that a complicated interaction between several different roles would determine one's effective creation permissions.
I believe it would be better to instead build this on top of the existing CourseCreatorRole and the related access checking functions. What do you think?
|
Hey @kdmccormick, thanks a lot for reviewing the code. I agree with the fact that the flow is a bit complicated. I am just wondering what can be a better approach? As I see it we check CourseCreator permission here. So we introduce a check here, if the user has a CourseCreator role then it goes ahead and does a check that the user should be present in an organization using the courseaccessrole model. Am I understanding this correct? Thanks a lot for the help here again :) |
|
@farhaanbukhsh Right, so there is a CMS model called CourseCreator that tracks status of a user's request to be able to create content in Studio. I could see us adding a nullable That model raises a signal which is caught in course_creators/views.py, which updates the That Finally, in |
|
@kdmccormick Thanks for the elaborate explanation, this looks like a legitimate good solution. I will try to implement this and ping once done 😄 |
e5676f9
to
b7a7c7e
Compare
A Many to many field makes more sense here, what do you say? Since a course creator can be a part of many organizations. |
Good point! How do you suggest we indicate that a CourseCreator has global creation access, though? Treating an empty many-to-many relation as "global access" seems dicey; it would be very surprising if removing every org from the relation gave you access to create courses under every org! Perhaps: a boolean |
This looks like a good approach for now where we can use the boolean, to toggle between CourseCreator Role and OrgContentCreator Role. So if the boolean is False, we don't create CoureCreatorRole for the user instead for each Organization we give the user an OrgContentCreator role. If the boolean is switched we just need to add/remove ContentCreatorRole accordingly. Hope I am understanding this correctly. I am working on this and will push the changes soon. :) |
|
@farhaanbukhsh Sounds right to me! |
a92ceb7
to
1512587
Compare
cms/djangoapps/course_creators/migrations/0002_auto_20210418_0806.py
Outdated
Show resolved
Hide resolved
Signed-off-by: Farhaan Bukhsh <farhaan@opencraft.com>
Signed-off-by: Farhaan Bukhsh <farhaan@opencraft.com>
bd75561
to
07ea7da
Compare
|
@kdmccormick I have rebased the PR, feel free to use the commit message while doing a Squash+Merge. :) Thanks for the amazing reviews and a crazy lot of patience. :) |
|
Your PR has finished running tests. There were no failures. |
|
EdX Release Notice: This PR has been deployed to the staging environment in preparation for a release to production. |
|
EdX Release Notice: This PR has been deployed to the production environment. |
…6616) Current State (before this commit): Studio, as of today doesn't have a way to restrict a user to create a course in a particular organization. What Studio provides right now is a CourseCreator permission which gives an Admin the power to grant a user the permission to create a course. For example: If the Admin has given a user Spiderman the permission to create courses, Spiderman can now create courses in any organization i.e Marvel as well as DC. There is no way to restrict Spiderman from creating courses under DC. Purpose of this commit: The changes done here gives Admin the ability to restrict a user on an Organization level from creating courses via the Course Creators section of the Studio Django administration panel. For example: Now, the Admin can give the user Spiderman the privilege of creating courses only under Marvel organization. The moment Spiderman tries to create a course under some other organization(i.e DC), Studio will show an error message. This change is available to all Studio instances that enable the FEATURES['ENABLE_CREATOR_GROUP'] flag. Regardless of the flag, it will not affect any instances that choose not to use it. BB-3622
…6616) Current State (before this commit): Studio, as of today doesn't have a way to restrict a user to create a course in a particular organization. What Studio provides right now is a CourseCreator permission which gives an Admin the power to grant a user the permission to create a course. For example: If the Admin has given a user Spiderman the permission to create courses, Spiderman can now create courses in any organization i.e Marvel as well as DC. There is no way to restrict Spiderman from creating courses under DC. Purpose of this commit: The changes done here gives Admin the ability to restrict a user on an Organization level from creating courses via the Course Creators section of the Studio Django administration panel. For example: Now, the Admin can give the user Spiderman the privilege of creating courses only under Marvel organization. The moment Spiderman tries to create a course under some other organization(i.e DC), Studio will show an error message. This change is available to all Studio instances that enable the FEATURES['ENABLE_CREATOR_GROUP'] flag. Regardless of the flag, it will not affect any instances that choose not to use it. BB-3622
…6616) feat: grant course/library creation rights by the organization (openedx#26616) This reverts commit 5ca2ce2. Current State (before this commit): Studio, as of today doesn't have a way to restrict a user to create a course in a particular organization. What Studio provides right now is a CourseCreator permission which gives an Admin the power to grant a user the permission to create a course. For example: If the Admin has given a user Spiderman the permission to create courses, Spiderman can now create courses in any organization i.e Marvel as well as DC. There is no way to restrict Spiderman from creating courses under DC. Purpose of this commit: The changes done here gives Admin the ability to restrict a user on an Organization level from creating courses via the Course Creators section of the Studio Django administration panel. For example: Now, the Admin can give the user Spiderman the privilege of creating courses only under Marvel organization. The moment Spiderman tries to create a course under some other organization(i.e DC), Studio will show an error message. This change is available to all Studio instances that enable the FEATURES['ENABLE_CREATOR_GROUP'] flag. Regardless of the flag, it will not affect any instances that choose not to use it. BB-3622 Signed-off-by: Farhaan Bukhsh <farhaan@opencraft.com>
|
I added notes about this new feature to the Maple release notes page. |
…penedx#26616)" This reverts commit a85f2d0.
…penedx#26616)" This reverts commit a85f2d0.
…6616) Current State (before this commit): Studio, as of today doesn't have a way to restrict a user to create a course in a particular organization. What Studio provides right now is a CourseCreator permission which gives an Admin the power to grant a user the permission to create a course. For example: If the Admin has given a user Spiderman the permission to create courses, Spiderman can now create courses in any organization i.e Marvel as well as DC. There is no way to restrict Spiderman from creating courses under DC. Purpose of this commit: The changes done here gives Admin the ability to restrict a user on an Organization level from creating courses via the Course Creators section of the Studio Django administration panel. For example: Now, the Admin can give the user Spiderman the privilege of creating courses only under Marvel organization. The moment Spiderman tries to create a course under some other organization(i.e DC), Studio will show an error message. This change is available to all Studio instances that enable the FEATURES['ENABLE_CREATOR_GROUP'] flag. Regardless of the flag, it will not affect any instances that choose not to use it. BB-3622 Signed-off-by: Farhaan Bukhsh <farhaan@opencraft.com>
…6616) (#437) Current State (before this commit): Studio, as of today doesn't have a way to restrict a user to create a course in a particular organization. What Studio provides right now is a CourseCreator permission which gives an Admin the power to grant a user the permission to create a course. For example: If the Admin has given a user Spiderman the permission to create courses, Spiderman can now create courses in any organization i.e Marvel as well as DC. There is no way to restrict Spiderman from creating courses under DC. Purpose of this commit: The changes done here gives Admin the ability to restrict a user on an Organization level from creating courses via the Course Creators section of the Studio Django administration panel. For example: Now, the Admin can give the user Spiderman the privilege of creating courses only under Marvel organization. The moment Spiderman tries to create a course under some other organization(i.e DC), Studio will show an error message. This change is available to all Studio instances that enable the FEATURES['ENABLE_CREATOR_GROUP'] flag. Regardless of the flag, it will not affect any instances that choose not to use it. BB-3622 Signed-off-by: Farhaan Bukhsh <farhaan@opencraft.com>
Product Change Description
Current State
Studio, as of today doesn't have a way to restrict a user to create a course in a particular organization. What Studio provides right now is a
CourseCreatorpermission which gives anAdminthe power to grant a user the permission to create a course.For example: If the
Adminhas given a userSpidermanthe permission to create courses,Spidermancan now create courses in any organization i.eMarvelas well asDC.There is no way to restrict
Spidermanfrom creating courses underDC.Purpose of this PR
The changes done here gives
Adminthe ability to restrict a user on an Organization level from creating courses,For example: Now, the
Admincan give the userSpidermanthe privilege of creating courses only underMarvelorganization. The momentSpidermantries to create a course under some other organization(i.e DC), we are showing the following error message:Admin's Responsibility
With this PR the
Admincan give users the permission to create courses underanyorganization or under aspecificset of organizations.If
Adminchecks theAll Organizationcheckbox then theuserwill be granted permission to create courses under any organization.If
Adminaddsspecificorganizations under the selected lists then theuserwill only be able to create courses under those organizations.There are few edge cases that can be encountered and below are the screenshot of how we inform the Admin/User about it
When
All Organizationis unchecked and noOrganizationis added to the listWhen
All Organizationis checked and specificOrganizationare added as wellError message when the user enters organization name for which user doesn't have permission
Engineering Implementation
The condition added to ensure that if the feature is enabled
user will not be able to create the course outside of the organisation
in which they belong.
JIRA tickets: BB-3622
Discussions: Link to any public dicussions about this PR or the design/architecture. Otherwise omit this.Dependencies: None
Screenshots:
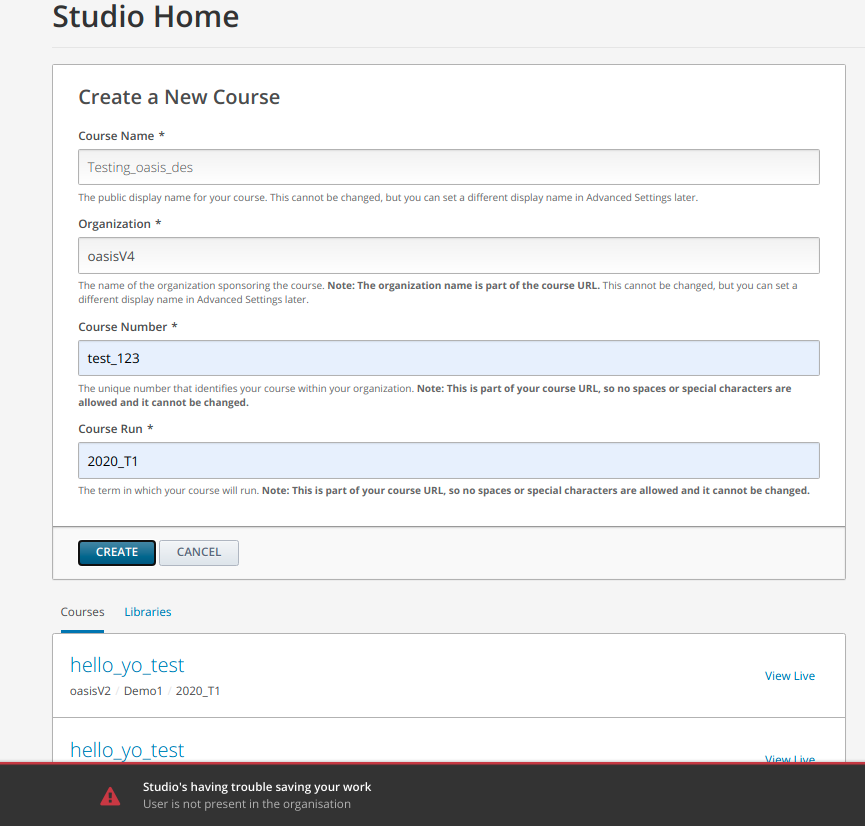
Sandbox URL: TBD - sandbox is being provisioned.Merge deadline: "None" if there's no rush, "ASAP" if it's critical, or provide a specific date if there is one.Testing instructions:
make dev.shell.studioThe below changes are also required to be done
In theFEATURESdictionary addRESTRICT_NON_ORG_COURSE_CREATION: trueGo to theadminpage and in localhost:18010/admin/student/courseaccessrole/ create a new entry, add the user, give it instructor privilege, don't add theOrgyetall_organization field, course_content_group role s created in http://localhost:18010/admin/student/courseaccessrole/ and on disabling it and adding org, OrgContentCreator role is created.Additional Manual Tests
Author notes and concerns:
Reviewers