-
Notifications
You must be signed in to change notification settings - Fork 727
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Adding second WAN with type DHCP makes OPN unreachable #1811
Comments
|
Disabling and enabling DHCP WAN reproduces this problem. root@dialin:~ # ping apple.com system.log and dmesg doesn't show anything interested. |
|
what does |
No default anymore, Google IP fixed routed via WAN (IP 217.X), two DNS servers from DHCP routed via v6(?) |
|
reenabling WAN_DHCP doesn't add any default gateway. |
|
can you try the following in a php script? Usually it should try to setup routing on linkup, but maybe the dhcp client is throwing a race condition in here. |
|
You mean executing this script after enabling WAN_DHCP? |
|
yes, just to be sure that the issue is persistent. |
|
This seems to be the same problem as opnsense/plugins#239. I have posted screenshots there. |
|
@mimugmail I was particularly interested in the first screenshot with both interfaces enabled, can you supply that too? |
|
ok, this doesn't make sense, it should keep your static route as default all the time. I will see if I can reproduce this somewhere... |
|
This would be great! Here's the dhcp log when enabling IF: I switched from DHCP to static with the values I receive via DHCP and then it works. So it seems to be related to dhcp only. |
|
@mimugmail do you have gateway switching enabled on this device? I can't reproduce this on my end. Just to be sure, what does this output when both interfaces are connected and the gateway isn't there? |
|
I just found this feature here #1315 |
|
Ok I just tested with WAN2 as DHCP and now it works fine with gateway switching enabled. P.S.: Really appreciate you help and setup a test env @AdSchellevis |
|
The problem with that feature is that it had multiple bugs and relies on gateway monitoring. Most bugs may be gone since 17.7, but the monitoring it relies on is still problematic. Other problems are that there is no fallback priority / logic, we can't mark gateways to be ignored in switching. It's really just a life saver in the short term, but a long term network failure incident. |
|
But how do you want to manage failover for local services? My tests with pf and failover group didn't work. |
|
I'm closing this one now since it works now with gateway switching enabled and without gwgroups. Thank you guys! 👍 |
|
@mimugmail thank you! maybe we're just missing a few tweaks so thanks for pursuing this :) |
|
@fichtner Perhaps sime easy tweaks, hopefully. I'm doing some testbeds right now, really strange behavior. But with you guys I'm quite sure we'll coming some steps nearer to perfection :) |
|
Hello, OPNsense 18.7.4 (amd64/OpenSSL) here. Tried to I then lost access to the web GUI too, and tried hitting the "11) Reload all services" option over ssh. Big problems for a seemingly innocent change: bringing up a 2nd WAN interface. I did not configure a 2nd gateway before adding WAN2. Working on a link with a hundred people on it, I'd love to know when a change has the potential to disrupt the link in an unrecoverable way. |
|
the bit pointing out the lack of guarantees: not useful. |
|
Sadly, it's not enough. Nobody really bothers testing, not even the OP, likely citing "a link with a hundred people on it" for the reason not to test it. It's a deadlock. Everyone gets what they offer. |
|
Ehh .. sorry, did I miss something? Shall I test something? :) |
|
The discussed dhclient changes are in master via #2542, no further action needed from this ticket‘s perspective. |
|
It would be tricky, but reporting the issue does indicate a willingness to test (at least from me) because I do rely on OPNsense and have a fair understanding of maintainership of free software - although maybe not an understanding of the particular challenges of OPNsense maintainers. |
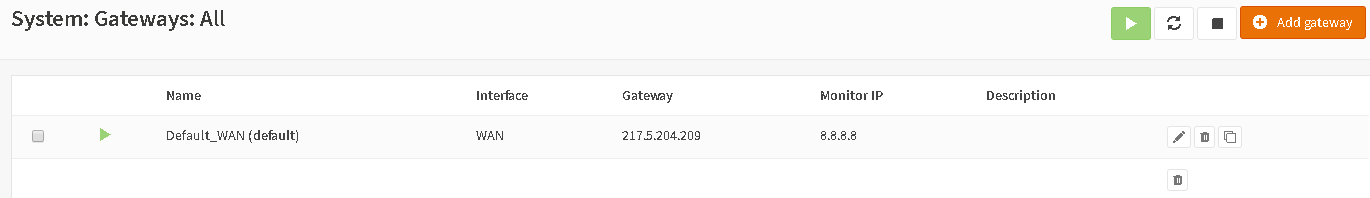
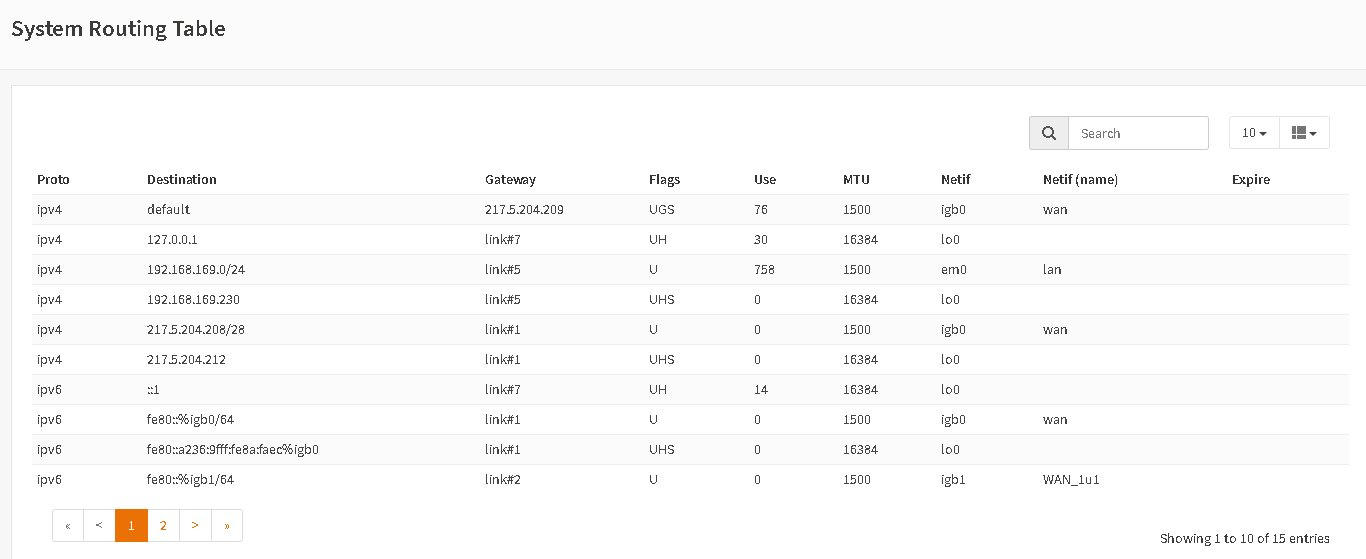



I have a OPN installation with a static WAN IP address.
When I add a second WAN, Type DHCP and plug the cable, the system get's an IP address and a second default gateway from DHCP. After this the firewall isn't reachable anymore via WAN or WAN2.
I can see the packets coming in via the WAN interfaces bot no reply sent back to any IF.
After a reboot it works again via WAN1.
Is this normal behavior? For me it's OK to know that FW has to be restarted, but I think this should work flawless in productive environments.
The text was updated successfully, but these errors were encountered: