New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
HAProxy - Add more Tuning Option in Public Service #1188
Comments
|
I'm commenting on this issue because I ran into similar issue configuring haproxy in opnsense for Airsonic as described here: https://airsonic.github.io/docs/proxy/haproxy/ Oddly, I was able to add the: to the front end fine using the Advanced mode "option pass thru" text box on the public service so I'm not sure why that doesn't work for the OP as his/hers would be similar I think (I am running latest 19.1 so maybe it didn't exist prior). However, where I ran into problems was on trying to add the: http-response replace-value Location ^http://(.*)$ https://\1 to the real servers backend config - if you used the advanced pass thru option on that dialog, it appends whatever you type to the end of the server line rather than putting it on its own line(s). I have manually edited the conf file for now, but since it is generated, a fix for the gui would be nice eventually. Kudos to you all for the work you have done though. Even with this minor issue, the haproxy/letsencrypt setup in opnsense is top notch and allows me to run a bunch of different VMs at my house behind a single ip all with valid certificates - no muss - no fuss. |
|
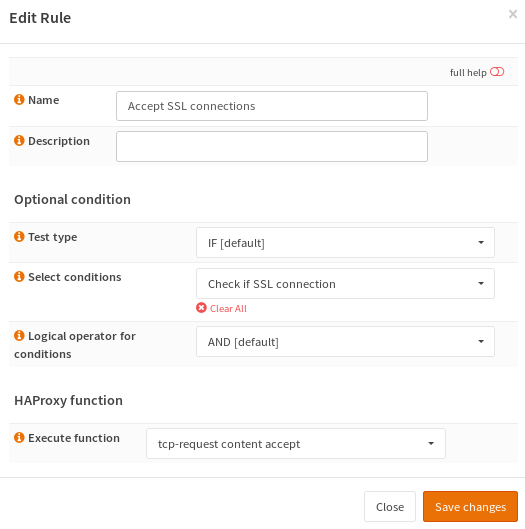
@oasisck First, add a condition to check if communication is SSL/TLS: Add a rule to accept the TCP connection if the SSL/TLS condition matches: Afterwards add this rule to your Public Service (frontend) and apply the configuration change. Only the "inspect-delay" is missing. I'm not sure if it's absolutely required for this use-case. I'll add support for it to the GUI soon, it will then be available in rules. @MolallaComm Add another rule to add the X-Forwarded-Proto header. Afterwards add both rules to your Public Service (frontend) and apply the configuration changes. I strongly recommend to remove everything from all "advanced pass thru" options, because this might break your installation in future releases (i.e. when we upgrade HAProxy to a new major release we cannot guarantee that these options are still compatible). |
|
Hi @fraenki thanks for your support and update By the way I got a warning with your rule about tcp request accept ssl and about the rule inspect-delay (maybe I'm wrong with my cond/rule) it's very slow to load the webpage than directly put in option like tcp request content accept if { req_ssl_hello_type 1 } Maybe I miss something ? |
|
@oasisck There was a mistake in my example... Indeed, "tcp-request connection accept" is invalid, because it cannot be used for content inspection. Sorry for the confusion, I've updated the screenshots accordingly. FWIW, the HAProxy documentation contains a nice section which explains the difference between those two options: |
|
@fraenki it works 👍 |




Important notices
Before you add a new report, we ask you kindly to acknowledge the following:
[x] I have read the contributing guide lines at https://github.com/opnsense/core/blob/master/CONTRIBUTING.md
[x] I have searched the existing issues and I'm convinced that mine is new.
Is your feature request related to a problem? Please describe.
Not able to reverse proxy mode TCP using NSI with GUI without thoses parameters
Describe the solution you'd like
Add more Tuning Option in Public Services or a box for adding multiple lines just after mode tcp
Describe alternatives you've considered
Add thoses lines manually in /usr/local/etc/haproxy.conf
Additional context
https://forum.opnsense.org/index.php?topic=11362.msg52592#msg52592
Thanks for your amazing work
The text was updated successfully, but these errors were encountered: