New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
security/acme-client: duplicate Common Names break acme.sh configuration #3127
Comments
|
Thank you for creating an issue. For more information about the policies for this repository, The easiest option to gain traction is to close this ticket and open a new one using one of our templates. |
I've never seen this issue anywhere. How do you verify if the certificate was updated? |
|
As you can see in the logs, "Le_OrderFinalize='https://acme-v02.api.letsencrypt.org/acme/finalize/237870340/125531643127'" the script is supposed to download the updated certificate. BTW: I stopped the automatic cron update and manually updated it after a couple of days, not touching anything until then, and then (with the same log entries) I received a new certificate (using the button "forcefully renew the certificate"). Then I could use th automations to get it into my server. However, this does not seem to be a permanent solution as the script should automatize it. |
|
Did you check
So you are using an Acme Automation to send the certificate to your server, right? This is missing from the logs you've provided. :( Please provide some details about the Automation and log entries that show a failed attempt. |
|
The automation worked fine always. It was always the old certificate in the storage, so even when I checked the storage on my OPNSENSE box, the certificate showed an expiry of Sep 15/2022. I could copy it (via SFTP) to the server, but it was still the old certificate. |
Well, acme.sh claims to have renewed the certificate. Please run the following command: And provide the output here. |
|
Well, unfortunately (see my posting above) I could renew it manually after many tries. I (as written) have changed the cron job from daily to weekly and try to find out if that is the reason. As the certificate is now shown as renewed until Dec 2022 I will actually have to wait to see if it will be renewed. I assume that the "old" certificate is removed when renewed. Please correct me if I am wrong, then I will do what you propose. |
|
I am also having this issue. I recently noticed ACME client is renewing LetsEncrypt cert daily. Further investigation indicates it is not registering the new certs in OPNsense Navigating to It appears the ACME client is not writing the cert to OPNsense's trust storage. I have tried to reimport the cert, but nothing changes. Further info: I have tried removing the old cert from the Trust Store, and re-importing from the ACME client certification. The cert DOES reappear in the trust store, but it is the old cert, not the cert. Logs: I could not identify where to get logs for the trust store Running: |
I cannot spot any errors related to Acme Client in the provided logs. Everything looks good to me, so at first glance there's nothing I can do about it. Some ideas for further investigation:
Next try to find the Acme Client entry for the affected certificate in config.xml: Now compare the
|
|
Certs are scheduled to check if renewal is required daily, but renewal interval is 60. The I'm currently rate-limited by letsencrypt because of the daily renewals; I have set loglevel=debug and will report back once I attempt a manual renewal. |
|
Came here because of the same issue I guess. |
|
@fraenki The cert tried to autorenew this morning with the same issue. Here are the logs: I was able to successfully renew after completely nuking my cert setup and rebuilding. I have not yet validated that a renewal will update the cert in the trust store.
|
Acme Client thinks that your certificate is disabled in the GUI.
So I'm assuming that finding the root cause for your issue will not be possible anymore... :-/
I STRONGLY discourage everyone from doing this. If there's a bug, let's try to find the root cause. If you follow these steps there's nothing we can do anymore. |
I'm pretty sure that's referring to the staging cert that has the same name? I had it disabled b/c I did not want it to continuously renew
Possibly? Based on what I could grok from the ACME logs, it seemed like the issue was the integration between the ACME client and the OPNsense trust store, not the cert renewal process itself. |
Do they share the same name? Pretty confusing, but now the log entry makes sense.
What exactly leads to this conclusion? I was not able to identify this from the logs. |
|
They did share the same name... I wasn't sure how to change, since the description field doesn't seem to impact the name, and the name seems to be derived from the
The logs for ACME showed a successful renewal. The ACME UI indicated an updated cert renewal date. It is only the OPNsense trust store UI (and therefore, the browser window) that did not use the updated cert, even after using ... in retrospect, I did not think to run |
The certificate name cannot be changed. Changing the CA of a certificate is also not supported. If you need to test something with a different CA (Let's Encrypt Staging), I'd recommend to create a 2nd certificate for this purpose (as you did).
We definitely need more information to make some progress on this issue. I don't know what we're looking for, because the logs do not indicate any issue. Maybe we need (in addition to the previously mentioned logs)....
Maybe provide the full output of the openssl command, just in case... |
|
Having the same issue, ACME certificates renew not working (anymore) last ACME status "internal error". Manual update works, tested with the staging environment that did have the same error using automation. OPNsense, packages and plugins are up to date. |
Did you restore OPNsense from a backup or something like that? |
|
No, this OPNsense instance is installed using Ansible (with a mix of using the API, if possible, or changing the config.xml and reloading using |
|
@skipperTux From the logs it seems that something messed up your Acme Client or acme.sh config. I don't think any OPNsense component did this. And the Acme Client plugin will never change a cert ID. So may it was your Ansible, or something else. I don't know. |
|
ACME Client and HAProxy have not been installed using Ansible, have been installed manually, roughly following this guide, as I currently do not have scripts for these Plugins. I also don't get it, the acme.sh command using one path, but in the ACME log the path is different 🤷♂️?? |
acme.sh is the tool that handles the actual creation/renewal of certificates. The "ACME Log" contains the raw log messages from acme.sh. AcmeClient is the OPNsense plugin component, this component only logs to the "System Log". So the AcmeClient plugin thinks that your cert ID is 634c119619e747.53710732, but the acme.sh tool thinks it's 634c116f6097a2.72834012. Like I said, there's no way that the plugin could mess it up this way. That's all I know. |
You may want to check the acme.sh parts for your cert: And maybe also review the contents of the cert config: |
|
Oh wait, did you create two (or more) certificates with the exact same name? |
|
I think you have caught me with this 😮, if you mean by exact same name the certificate Common Name. I first setup everything using Let's Encrypt Staging (Test CA), but using the intended final domains (e.g. *.example.org and *.sub.example.org). After that I switched to production but using the same common names. I did not find any other way to test my setup, but I could not give the certificates an id-name, independent from the intended domain (= common name). Is this setup for Test and Prod CA wrong? Any idea for a better setup (without having two different domains) and how to fix this setup? |
|
That's actually a limitation in the way we use acme.sh: you cannot have two certificates with the exact same common name. I think it is possible to mitigate this limitation in the Acme Client plugin, but it's not trivial and will require code changes and extensive testing. This isn't something that will be ready soon. I'll probably need a lot time for this, so no ETA. However, even when this mitigation is implemented, it will be unable to fix what's currently broken. As a quick fix you might try to remove the certificate(s) from Acme Client and OPNsense Trust and create/issue a new certificate. It should update the broken acme.sh configuration... but be aware that's just guessing on my side. I first need to figure out how to reliably reproduce this issue to know how to properly fix it. |
|
(Sorry for the late reply, I was locked out of Let's Encrypt because of limits.) I can confirm the following steps work to fix an existing duplicate Common Name issue:
Make sure you never have duplicate Common Names when ACME client is running. If you want to switch to a same Common Name certificate (like staging), I assume you have to redo all above steps (not confirmed). |
|
The upcoming os-acme-client 4.0 will officially support duplicate common names. |
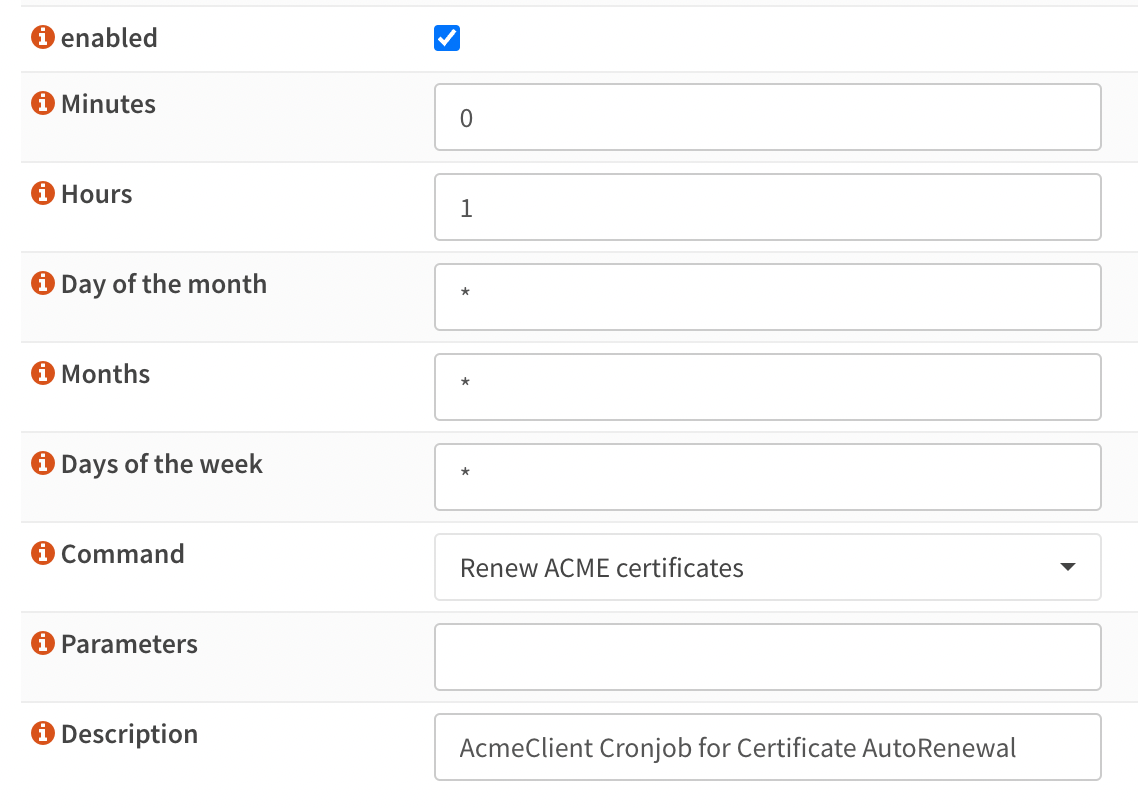
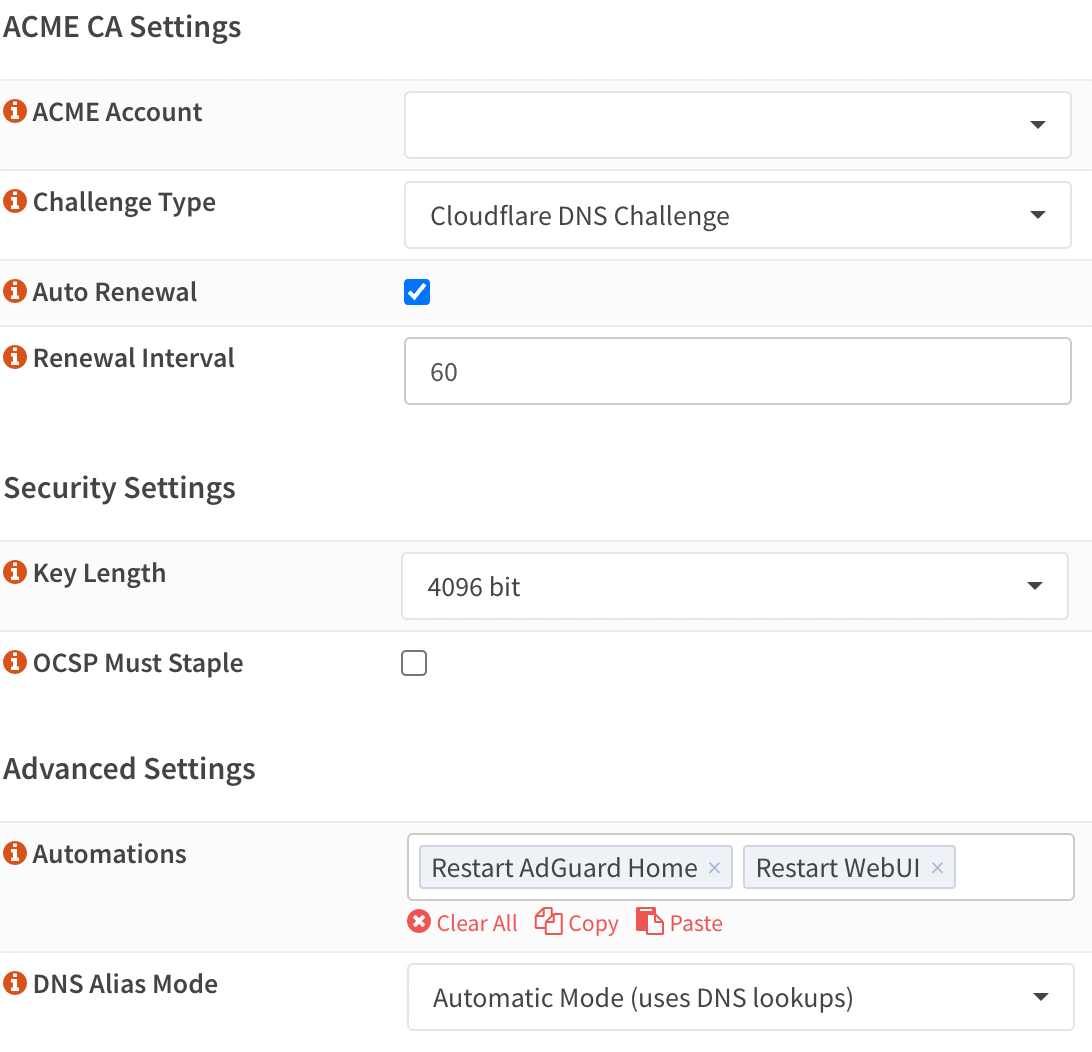

Describe the bug
Using the ACME plugin with OPNSENSE 22.7 out of the box
My last successful updated certificate is from June (3 months old).
The protocol claims to have updated the certificate and stored it in the certificate store.
However, there is only the "old" certificate.
When activating the Staging signing facility, there is no problem and immedaitely a new certificate is issued.
To Reproduce
Steps to reproduce the behavior:
Expected behavior
New certificate stored in certificate store
Relevant log files
Plugin Log:
ACME Log:
Environment
OPNsense 22.7.4-amd64
FreeBSD 13.1-RELEASE-p2
OpenSSL 1.1.1q 5 Jul 2022
The text was updated successfully, but these errors were encountered: