New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Deleting passcode doesn't disconnect the client #36146
Comments
I think it disconnects with some delay. (Session is still valid, you could verify with |
|
After one hour it is still connected. When I change a password, the client asks for a new one after around 4 minutes |
|
@HanaGemela Quit the client, then restart? @jvillafanez You were working with the sessions recently, could you have a look? |
|
Server issue, not Desktop issue. You can move the issue to that repo :)
…Sent from my iPhone
On 3. Sep 2019, at 14:02, Michael Stingl ***@***.***> wrote:
@HanaGemela Quit the client, then restart?
@jvillafanez You were working with the sessions recently, could you have a look?
—
You are receiving this because you are subscribed to this thread.
Reply to this email directly, view it on GitHub, or mute the thread.
|
|
Selective sync list knows it is not connected with 10.2 server almost immediately. Even though the client shows it is connected. With aplha2 everything looks connected |
|
I've checked some places where I expect the code should go through but it didn't. I think the passcode is used only for the "initial" authentication, then the next requests use the session created without using the passcode. The session itself is still valid even though the passcode isn't. The problems we have are:
A possible solution could be to store the passcode inside the user session. Having the association session -> passcode , we could logout from the session if the associated passcode is invalid or missing. I don't think the solution will be ready within 10.3 taking into account we'll be touching session code. We'll need to manually tests all the authentication mechanisms again. If someone can explain why it works with 10.2..... |
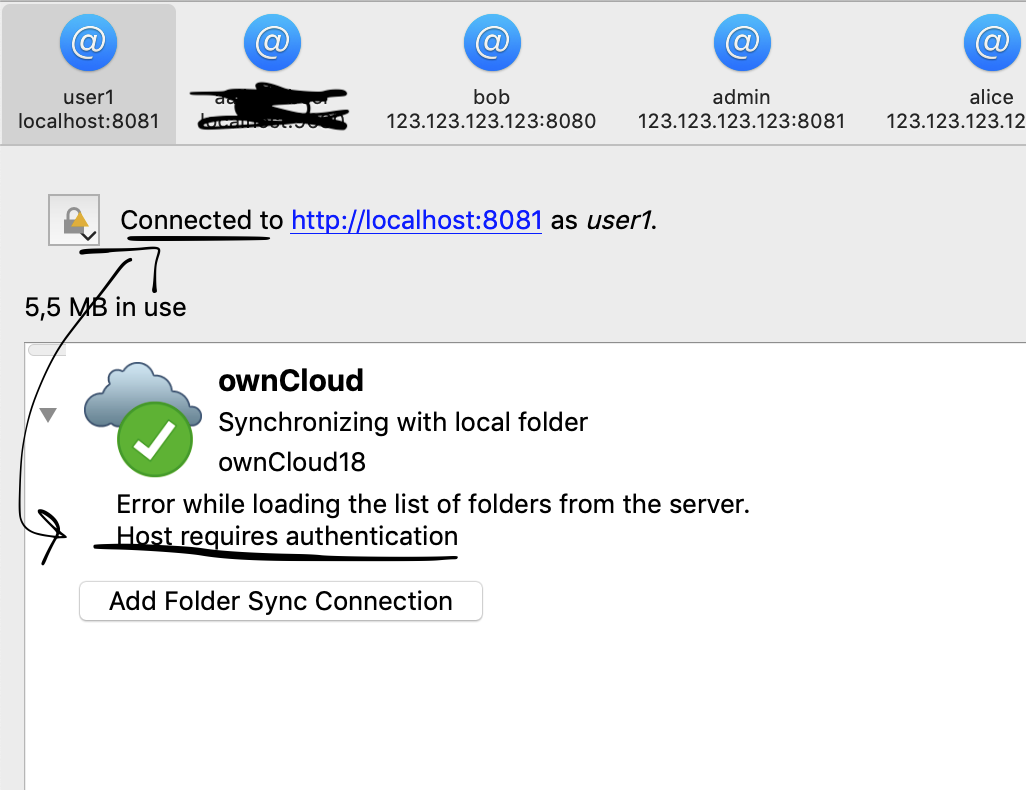
Server: 10.3.0 alpha2 (testing)
Client: 2.6.0-daily20190820 (build 12341)
macOS 10.14.6
Actual result: Client is still connected even though the delete button on the server has 'Disconnect' tooltip.
Expected result: Client has been disconnected
The text was updated successfully, but these errors were encountered: