A TypeScript implementation of the Enigma M3 encryption machine used during World War II.
Key features:
- Core components of the Enigma: plugboard, rotors and reflector.
- Rotor stepping and turnover, including the infamous double stepping anomaly.
- Configurable Enigma settings in JSON format.
- Optional logging of every letter permutation.
The Enigma M3 was a remarkable electro-mechanical cypher machine used by the German Navy (Kriegsmarine). This device, part of a series designed by the German engineer Arthur Scherbius in the early 20th century, had a pivotal role in the encryption and decryption of military communications, safeguarding the secrecy of critical information during World War II.
The Enigma M3 posed a formidable challenge to Allied codebreakers. A significant breakthrough occurred in Poland through the reverse engineering of this machine, followed by tireless decryption efforts, most notably at Bletchley Park in the United Kingdom. These endeavors played a vital role in Allied intelligence during the war by providing invaluable insights into German military strategies and communications.
While the successful deciphering of the Enigma code marked a momentous achievement, the Enigma M3, with its intricate design and advanced encryption capabilities, continues to stand as an enduring symbol of wartime cryptography. It epitomizes the enduring battle of wits between those who create codes and those who seek to break them, illustrating the enduring legacy of this extraordinary era in the history of encryption. [1]
Enigma operates as a rotor machine to achieve polyalphabetic substitution. This means the letter substitution scheme is not fixed but changes with the propagation of Enigma's rotating ciphering wheels and thus, with the letter's position in a text. The wheels advance stepwise with every keystroke, thereby triggering, in some positions, the adjacent wheel to the left to perform a step as well, pretty much as in a mechanical counter. Inside a wheel each letter position is biuniquely rendered to another position through a fixed set of wires. By combining and rotating the wheels, however, a very complex substitution code is obtained. Furthermore, the inner wiring as a whole can be rotated against the outer position indicator ring and, more importantly, against the trigger notches (this is known as "ring setting"). In some models, pairs of letters can be additionally swapped by interconnecting plugs ("stecker") on a plugboard via cables. [2]
Enigmas are equipped with a typewriter-like keyboard for input, while output is shown on a lampboard that in its layout resembles the keyboard. With every keystroke, the signal is routed first through the plugboard (if present), then through the fixed entry wheel and the rotor set, arriving at the reflector wheel. From there it is sent back on a different path – but with all rotor positions still the same – through the rotors, the entry wheel and again the plugboard until it reaches the lampboard where it lights the bulb corresponding to the substitute letter. A letter was therefore never encoded to itself, which would prove to be Enigma's most serious weakness. The symmetrized signal path and the resulting symmetric encryption however make it possible to decipher a message using the same machine setting it was encrypted with. [2]
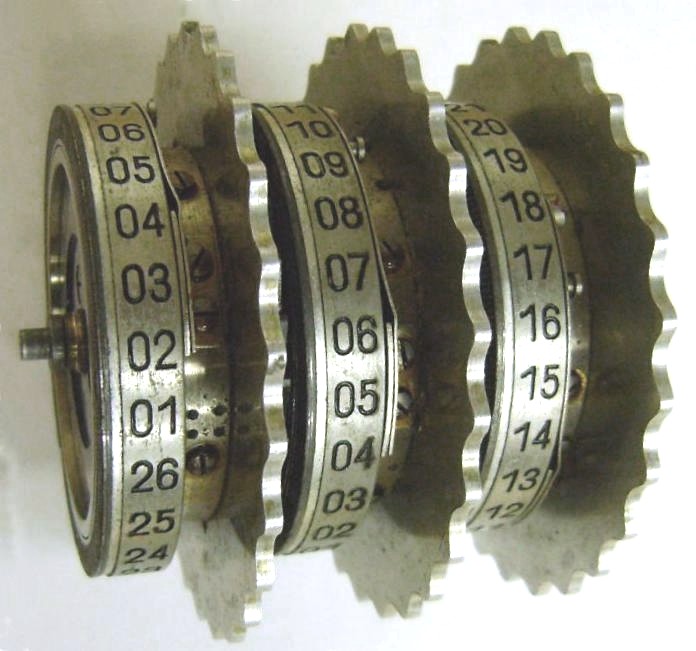
An original Enigma M3, three of the rotors used and a key sheet [3]
An Enigma machine's setting (its cryptographic key in modern terms) specified each operator-adjustable aspect of the machine:
- Wheel order (Walzenlage) – the choice of rotors and the order in which they are fitted.
- Ring settings (Ringstellung) – the position of each alphabet ring relative to its rotor wiring.
- Plug connections (Steckerverbindungen) – the pairs of letters in the plugboard that are connected together.
- In very late versions, the wiring of the reconfigurable reflector.
- Starting position of the rotors (Grundstellung) – chosen by the operator, should be different for each message.
For a message to be correctly encrypted and decrypted, both sender and receiver had to configure their Enigma in the same way; rotor selection and order, ring positions, plugboard connections and starting rotor positions must be identical. Except for the starting positions, these settings were established beforehand, distributed in key lists and changed daily. [4]
Import Enigma class:
import { Enigma, EnigmaInterface, SettingsInterface } from "node-enigma-m3";
const enigma: EnigmaInterface = new Enigma(false); // Instantiate with true to enable logging
const message = "MY MESSAGE";
const settings: SettingsInterface = {
plugboard: ["AB", "CD", "EF", "GH", "IJ", "KL", "MN", "OP", "QR", "ST"], // Plugboard pairs
reflector: "B", // Reflector types: "A", "B", "C", "B Thin", "C Thin"
rotors: [
// Rotors are defined from left to right
// Offset and Position: "A" to "Z" or 1 to 26
// Types: "I", "II", "III", "IV", "V", "VI", "VII", "VIII"
{ offset: "A", position: "A", type: "III" },
{ offset: "A", position: "A", type: "II" },
{ offset: "A", position: "A", type: "I" }
]
};
enigma.configure(settings);
const encodedMessage = enigma.cypher(message);
console.log(`Encoded message: ${encodedMessage}`); // Encoded message: LD KLKXPWPInstall project dependencies:
npm installBuild development version:
npm run buildThe build will be available in the dist folder.
Generate the documentation:
npm run docsThe documentation will be available in the docs folder.
The unit tests are available in the __tests__ folder. In order to run the tests:
npm testBesides unit tests, original cyphered messages from that period [3] were also included in __tests__/messages.test.ts.
This message is taken from a German army instruction manual for the Enigma I (interoperable with the later navy machine, Enigma M3).
Encrypted message:
GCDSE AHUGW TQGRK VLFGX UCALX VYMIG MMNMF DXTGN VHVRM MEVOU YFZSL RHDRR XFJWC FHUHM UNZEF RDISI KBGPM YVXUZ
Decrypted message:
FEIND LIQEI NFANT ERIEK OLONN EBEOB AQTET XANFA NGSUE DAUSG ANGBA ERWAL DEXEN DEDRE IKMOS TWAER TSNEU STADT
Readable format:
(German) Feindliche Infanterie Kolonne beobachtet. Anfang Südausgang Bärwalde. Ende 3km ostwärts Neustadt.
(English) Enemy infantry column was observed. Beginning [at] southern exit [of] Baerwalde. Ending 3km east of Neustadt.
Settings:
{
"plugboard": ["AM", "FI", "NV", "PS", "TU", "WZ"],
"reflector": "A",
"rotors": [
{ "offset": "X", "position": "A", "type": "II" },
{ "offset": "M", "position": "B", "type": "I" },
{ "offset": "V", "position": "L", "type": "III" }
]
}Sent from the Russian front on 7th July 1941.
Encrypted message:
EDPUD NRGYS ZRCXN UYTPO MRMBO FKTBZ REZKM LXLVE FGUEY SIOZV EQMIK UBPMM YLKLT TDEIS MDICA GYKUA CTCDO MOHWX MUUIA UBSTS LRNBZ SZWNR FXWFY SSXJZ VIJHI DISHP RKLKA YUPAD TXQSP INQMA TLPIF SVKDA SCTAC DPBOP VHJK
Decrypted message:
AUFKL XABTE ILUNG XVONX KURTI NOWAX KURTI NOWAX NORDW ESTLX SEBEZ XSEBE ZXUAF FLIEG ERSTR ASZER IQTUN GXDUB ROWKI XDUBR OWKIX OPOTS CHKAX OPOTS CHKAX UMXEI NSAQT DREIN ULLXU HRANG ETRET ENXAN GRIFF XINFX RGTX
Readable format:
(German) Aufklärung abteilung von Kurtinowa nordwestlich Sebez [auf] Fliegerstraße in Richtung Dubrowki, Opotschka. Um 18:30 Uhr angetreten angriff. Infanterie Regiment... (continues in part 2)
(English) Reconnaissance division from Kurtinowa north-west of Sebezh on the flight corridor towards Dubrowki, Opochka. Attack begun at 18:30 hours. Infantry Regiment... (continues in part 2)
Settings:
{
"plugboard": ["AV", "BS", "CG", "DL", "FU", "HZ", "IN", "KM", "OW", "RX"],
"reflector": "B",
"rotors": [
{ "offset": "B", "position": "B", "type": "II" },
{ "offset": "U", "position": "L", "type": "IV" },
{ "offset": "L", "position": "A", "type": "V" }
]
}Sent from the Russian front on 7th July 1941.
Encrypted message:
SFBWD NJUSE GQOBH KRTAR EEZMW KPPRB XOHDR OEQGB BGTQV PGVKB VVGBI MHUSZ YDAJQ IROAX SSSNR EHYGG RPISE ZBOVM QIEMM ZCYSG QDGRE RVBIL EKXYQ IRGIR QNRDN VRXCY YTNJR
Decrypted message:
DREIG EHTLA NGSAM ABERS IQERV ORWAE RTSXE INSSI EBENN ULLSE QSXUH RXROE MXEIN SXINF RGTXD REIXA UFFLI EGERS TRASZ EMITA NFANG XEINS SEQSX KMXKM XOSTW XKAME NECXK
Readable format:
(German) ... 3 geht langsam aber sicher vorwärts. 17:06 Uhr röm eins InfanterieRegiment 3 auf Fliegerstraße mit Anfang 16km ostwärts Kamenec.
(English) ... 3 goes slowly but surely forwards. 17:06 hours [Roman numeral I?] Infantry Regiment 3 on the flight corridor starting 16 km east of Kamenec.
Settings:
{
"plugboard": ["AV", "BS", "CG", "DL", "FU", "HZ", "IN", "KM", "OW", "RX"],
"reflector": "B",
"rotors": [
{ "offset": "B", "position": "L", "type": "II" },
{ "offset": "U", "position": "S", "type": "IV" },
{ "offset": "L", "position": "D", "type": "V" }
]
}This message was sent from the battleship Scharnhorst on 26th December 1943, the day on which it was sunk by torpedoes from British destroyers.
Encrypted message:
YKAE NZAP MSCH ZBFO CUVM RMDP YCOF HADZ IZME FXTH FLOL PZLF GGBO TGOX GRET DWTJ IQHL MXVJ WKZU ASTR
Decrypted message:
STEU EREJ TANA FJOR DJAN STAN DORT QUAA ACCC VIER NEUN NEUN ZWOF AHRT ZWON ULSM XXSC HARN HORS THCO
Readable format:
(German) Steuere Tanafjord an. Standort Quadrat AC4992, fahrt 20sm. Scharnhorst. [hco - padding?]
(English) Heading for Tanafjord. Position is square AC4992, speed 20 knots. Scharnhorst.
Settings:
{
"plugboard": ["AN", "EZ", "HK", "IJ", "LR", "MQ", "OT", "PV", "SW", "UX"],
"reflector": "B",
"rotors": [
{ "offset": "A", "position": "U", "type": "III" },
{ "offset": "H", "position": "Z", "type": "VI" },
{ "offset": "M", "position": "V", "type": "VIII" }
]
}- [1] https://www.ciphermachinesandcryptology.com/en/enigma.htm
- [2] https://people.physik.hu-berlin.de/~palloks/js/enigma/index_en.html
- [3] http://wiki.franklinheath.co.uk/index.php/Enigma/Sample_Messages
- [4] https://en.wikipedia.org/wiki/Enigma_machine
Useful resources: