-
Notifications
You must be signed in to change notification settings - Fork 317
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
New command: teams report directroutingcalls
#1772
Comments
|
Hi All, I'd like to work on this. |
|
Woot! All yours @aakashbhardwaj619 👏 |
|
That would be a good question in the MS Graph docs |
|
@aakashbhardwaj619 does it work with Agree with @waldekmastykarz that creating a question issue against the docs is the next step for raising this to the Graph team. |
|
@garrytrinder It doesn't work with I just checked in the Graph docs that there is already an issue created for this missing permission scope. https://github.com/microsoftgraph/microsoft-graph-docs-contrib/issues/4758 |
|
Thanks for the update @aakashbhardwaj619 I’ve also reached out to the Graph team to see if this can be looked at, referencing the GH issue, this has been acknowledged so hopefully this will be resolved quickly. Until then, let’s place this issue on hold until we hear of any progress. |
|
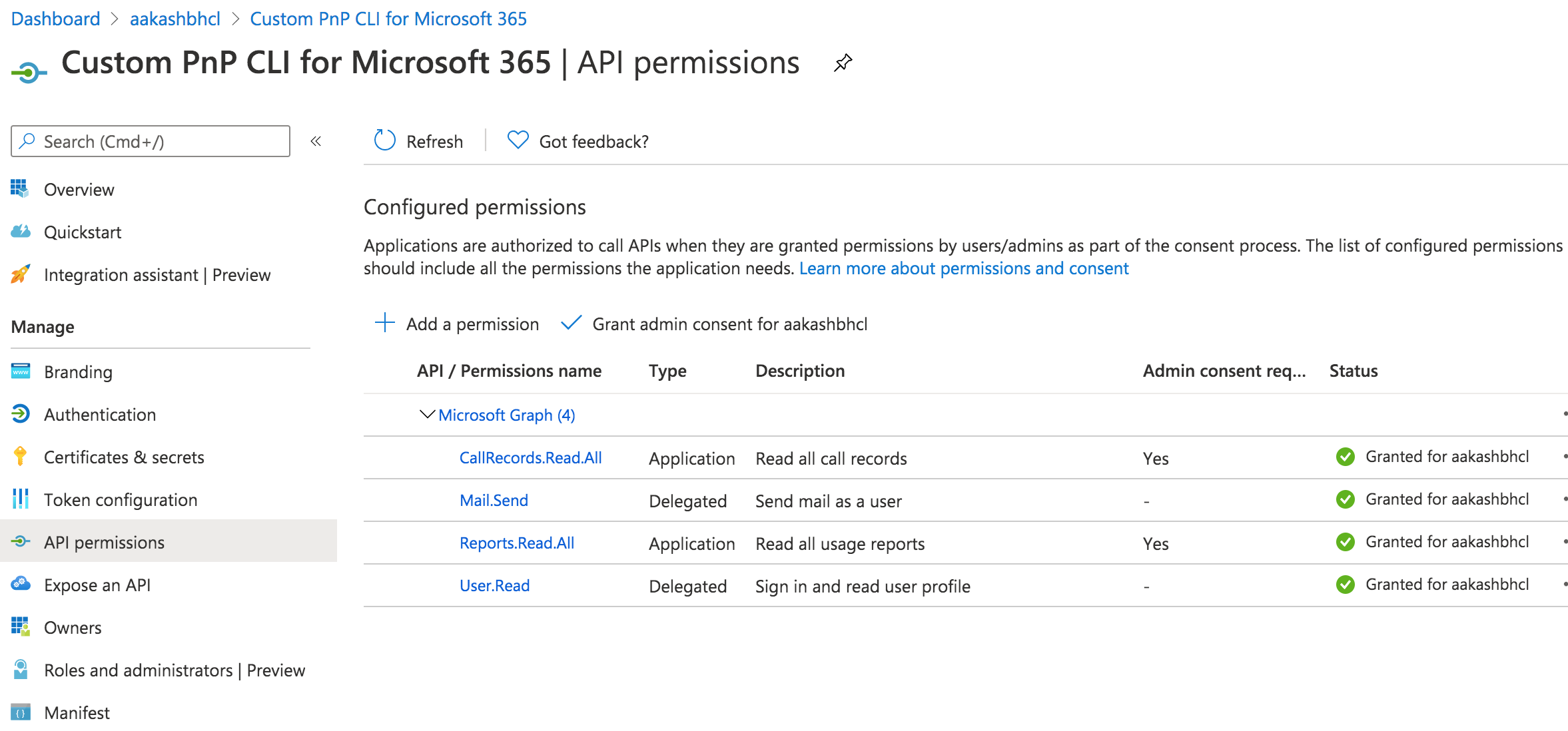
Following the closure of https://github.com/microsoftgraph/microsoft-graph-docs/pull/9859 the permission required for this endpoint is now |
|
I'll add them to our AAD app after the PR is approved. Until then, during dev, @aakashbhardwaj619 you can use a custom AAD app. |
|
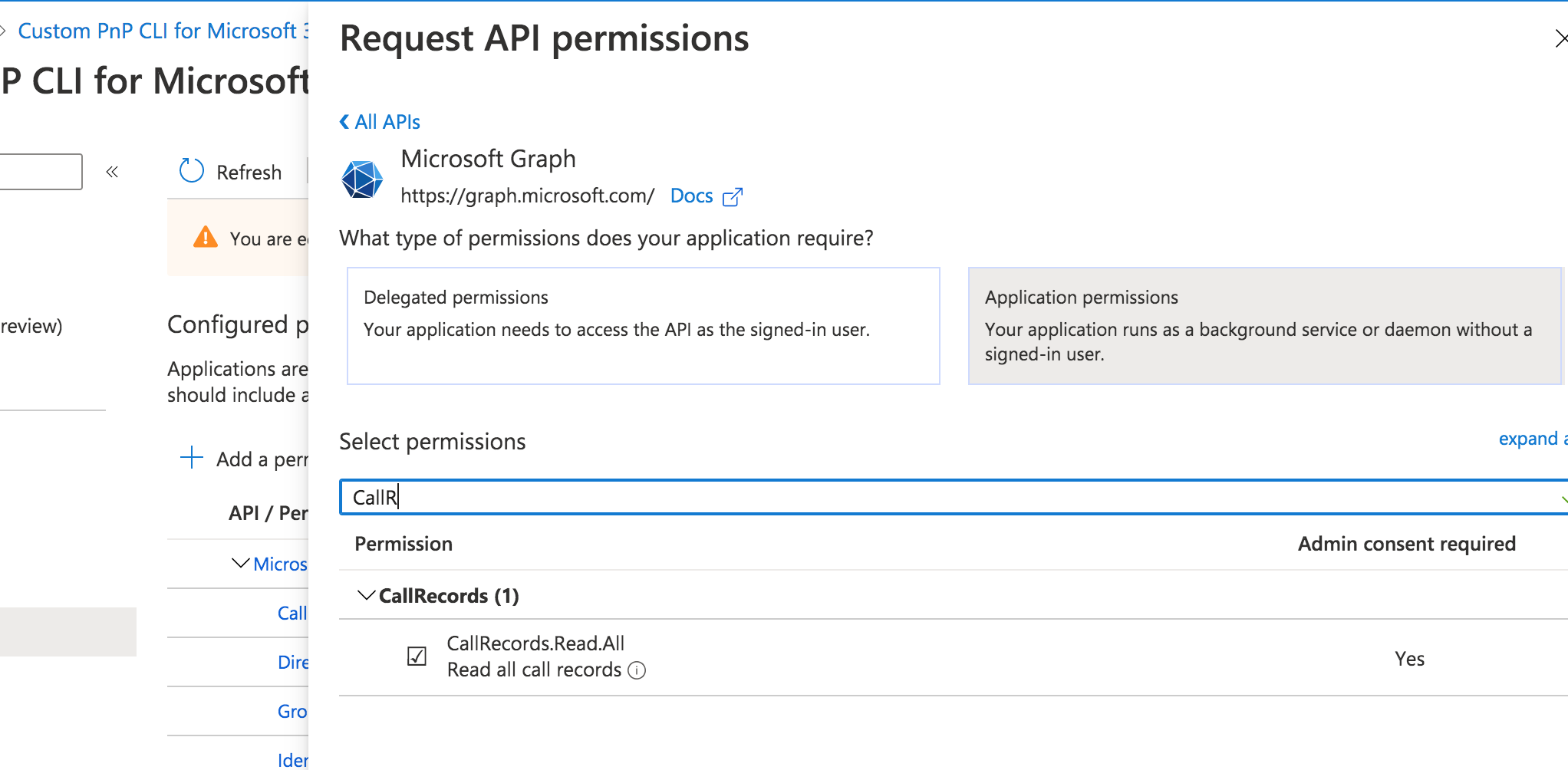
Hi guys, I started working on this command but struggling with getting the appropriate access token. I've granted the |
|
You assigned an app-only permission so if you're authenticating with user credentials, that permission won't be included in the token. |
|
@aakashbhardwaj619 you will need to authenticate using Certificate auth that uses a Custom Azure AD application that has the relevant app permission assigned to it. I don't think we have any docs covering that scenario end to end, so something we should consider adding gong forwards. I've found this article which may be able to help. |
|
Hey @aakashbhardwaj619 👋🏻 How are you getting on with this command? Feel free to reach out if you have any questions. |
|
Discussed with @aakashbhardwaj619 offline, he's happy to let someone else take this on. @leeford as discussed, this is all yours, thanks again for your help ❤️ |
|
Thank you, will get started 👍 |
Usage
teams report directroutingcalls [options]Description
Get details about Direct Routing calls made within a given time periodOptions
--fromDateTime <fromDateTime>--toDateTime [toDateTime]-o, --output [output]json,text. Defaulttext--verbose--debugAdditional Information
GET https://graph.microsoft.com/beta/communications/callRecords/getDirectRoutingCalls(fromDateTime=2019-11-01,toDateTime=2019-12-01)CallRecords.Read.AllApplication permissionThe text was updated successfully, but these errors were encountered: