New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Authentication error #1121
Comments
|
Hi, br, |
Yes, same error persists. |
|
Oh wait, what is the reason of having Implicit Grant enabled? Not required in this case from my point of view. |
|
Edit: Update the steps for a better follow-up.
Afterward, you do not have to authenticate against any CLI calls until you are not explicitly executing a logoff operation. It would be interesting to understand what exactly you want to achieve. In theory, the steps above should be sufficient for command-line automation scenarios. br, |
|
Hi @plamber,
I don't exactly follow this. I am not trying to run office365 cli. What I want to achieve is the ability to send out emails from my python application. For this, my understanding is that I need to first download the access token file by authenticating through the following steps: Is this not the way of generating the access token file? Thanks, |
|
I haven't tried it with Phyton. I am working in PowerShell. Nevertheless, the concept should be similar. I installed the CLI on my host.
Before running the CLI Authentication Performing commands You can find an example on how to integrate the CLI in scripts here: https://blog.mastykarz.nl/building-scripts-office-365-cli/ At first glance, I do not see the requirement for you to try to get the token differently. Maybe, I misunderstood your requirements. |
|
In addition to what @plamber mentioned: |
|
Ok, from what I understood from your comments, I did the following:
I went to https://microsoft.com/devicelogin and entered the code which then asked username and password. But when I provided the credentials, I was given this message: Am I making any mistake? Thanks, |
|
Edit: with correct screenshots If you do not have the "Suggested redirect URLs" enabled for public clients enabled, then a fake redirect URL und "Redirect URIs" solves your current issue. This is how I configured it in my application. On the other hand, if you change the settings as done in the screen below, this might be more appropriate for the CLI setup. |
|
Hi, Thanks @plamber. I was able to login successfully into office365 by giving credentials in https://microsoft.com/devicelogin. But how do I send out emails from the authenticated account after this (using a Python script)? I am following the instructions given here: https://github.com/O365/python-o365#usage This produces the error: Thanks, |
|
Hi, From my point of view, you should either use the other project's methods or with the CLI presented here. br, |
|
Ok got it. Thanks |
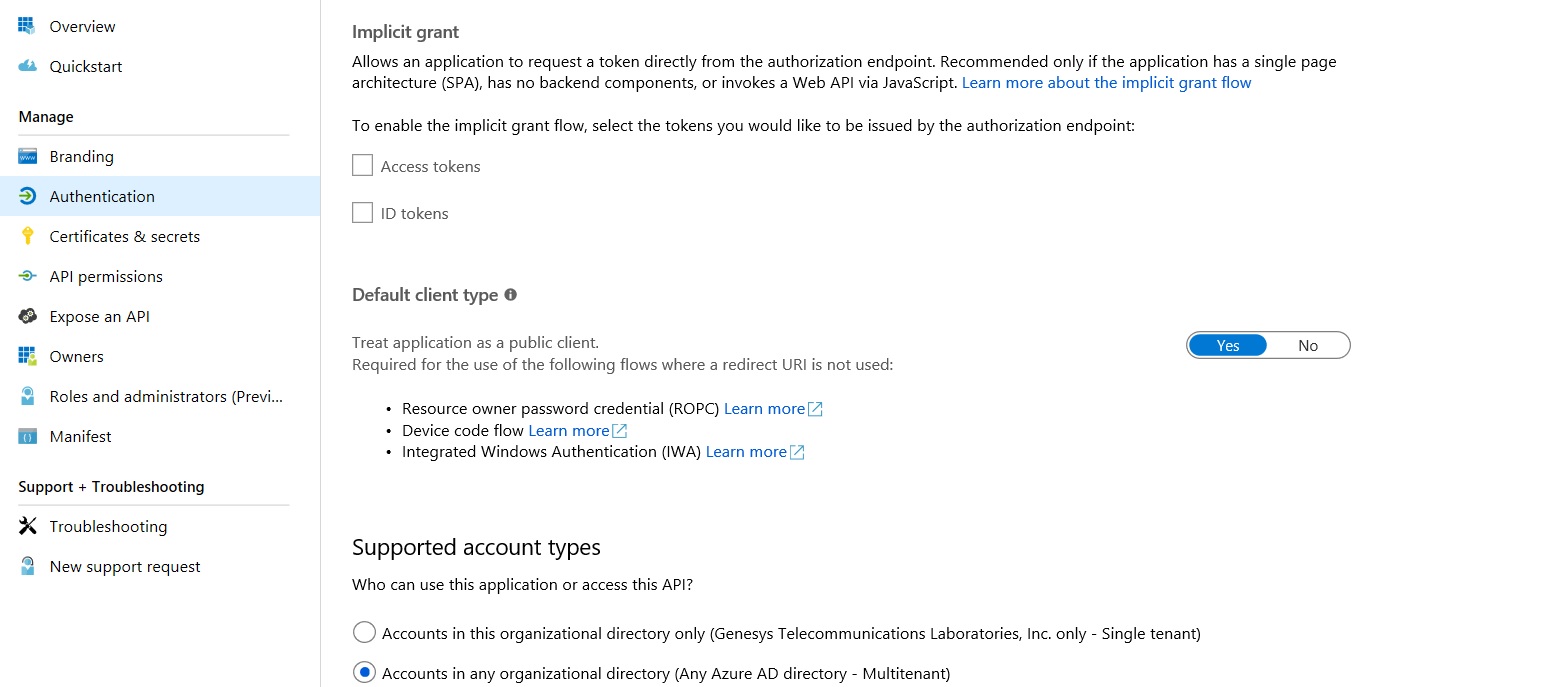
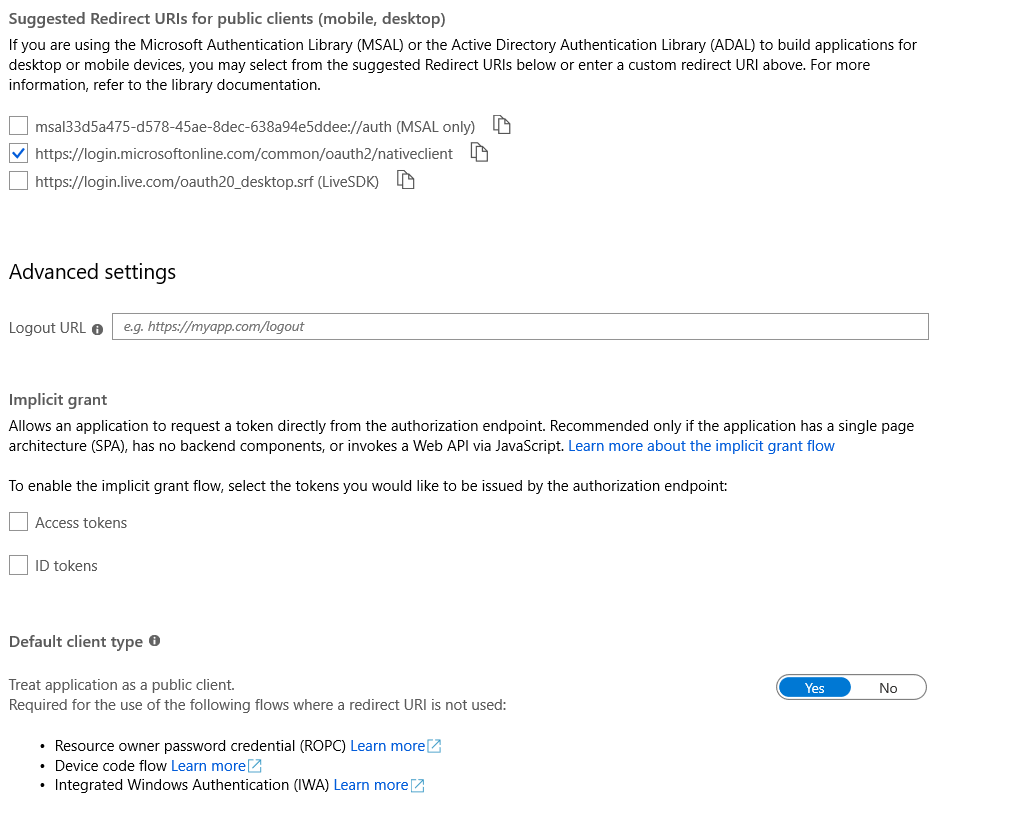

Hi,
I went through other related issues for this repo but none seems to solve my problem.
I am unable to authenticate and get access token.
These are the steps I followed in command-line:
Visit the following url to give consent:
https://login.microsoftonline.com/common/oauth2/v2.0/authorize?response_type=code&client_id=XXXX&redirect_uri=https%3A%2F%2Flogin.microsoftonline.com%2Fcommon%2Foauth2%2Fnativeclient&scope=https%3A%2F%2Fgraph.microsoft.com%2FMail.ReadWrite+https%3A%2F%2Fgraph.microsoft.com%2FUser.Read+https%3A%2F%2Fgraph.microsoft.com%2FMail.Send&state=8uYYgVKgZVdyAAB9wJYo4dCcPte2N6&access_type=offlinePaste the authenticated url here:
https://login.microsoftonline.com/common/oauth2/nativeclient?code=OAQABAAIAAAAP0wLlqdLVToOpA4kwzSnxc2V5yW7WGqV0QgL_QhC6P8_AQxTPZqMH6Y1_o3vA9S6mR6oOBPvQIYFh_s7DGsp7ytKxGrJ4DJPdcHLao5S4LO2kCX1MWPuhRvoY6XboWPPpjfQ-CLFBpy_2ZXY_F9_KL6aN4isT52gjwWfto-h8_KX4BhR_eAHggyIELOH_PRg3smfOe9KTf9Ml8GWgc2wpQjmOlNrcTp8IztO4-MbJ81VNsLg0fFukS1_exL8d13ktQ5nmmreZ6FrtoQ07yF8OyFwfXIZaiFeEE8622w7uC7RsoUlSJq9GhgkQuTqf4mwOc4oHSxW790aarq2j6C6nNVBjLy4M_yBiDvR047rzrVitmhzkT0Bxw_gF_cOxNBVDgDHeebO30eQ8JZcgu2ttecYsM8vygsoQpdlatJ-aUFq8S1br3vw8xtN7EfDN3ZTA-heDyU-V-O8rBL2ZQ0F0L5umYyzpXElWCYD8hOey9ySEesYO1yQNb-skTR9Tz5IVuYTVGolauDrggsgGiY6iBvdYRyOIWCOsRC4dQRAHQClzfdMbsYrsr-3U3Agv_mce_H6Tr9yWyW1ZbASKD8aI1oS0KdgQVgoBhBLmIhYNQbf_ezs5ag7TUfa6j5WJGk98dV2EnbzJ0i4eZ22Rhh5IK4oesg5btHCF5Oi3d7LB98a7PObBYk9192qEL8Jj6eY_PtP3BTLyIYvzAWJ9FqVIFxxk1olS0khpZKqVQRORZ9x-5lEdIiWWhJcUrFVKh7XXXX&state=YqSQyBKZpw769L91S2VFgcal5tiu4J&session_state=54f91bd3-4b36-4168-8fca-03c4ad65f861The pasted URL was received after logging into the account. But I receive the following error:
The following are some screenshots of my Azure App Registration portal:
Please help.
Thanks.
The text was updated successfully, but these errors were encountered: