New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Force TLS email traffic over port 587 #366
Comments
|
You can use We have port 2525 open as well as 25 to get around some SMTP restrictions. Have a look at #306 (comment) |
|
I did that, now when I telnet into port 587: MacBook-Pro-van-William-David:~ server$ telnet . 587 Not sure why, because it's just an iptables rule... |
|
Does your plugin work in spite of the telnet issues? |
|
Nope... |
|
Does telnet work on port 25? |
|
Yes, on port 25 it works perfectly fine and I'm able to negotiate using the |
|
Could you try 2525 and see if telnet still works through that port? |
|
Nope, connection refused. Same with firewall disabled. |
|
I am unable to replicate your issues, I get working telnet with any forwarded port. Which server provider are you using? Could there be any curious filtering occurring? |
|
That is very odd. We're using Linode for this customer and I can assure you there is no filtering on any level. |
|
Can you check with |
|
Hi, I figured I'd send the entire output: When grepping on |
|
Going back a few steps....
Did you run the |
|
No, I have not. Why would I? I don't have a firewall. |
|
By the way, there is nothing listening on port 2525 either: |
|
If you have used Does that make sense? |
|
Apologies! Probably a lack of sleep :) I disabled the firewall completely to see what'd happen. To my surprise, port 587 still works, but not with SSL... I setup However, like I mentioned, SSL does not work. Without SSL everything functions fine. So I figured that might be a problem on my system. I tried that same command on a server, which does not work either, returning: The entire output: |
|
Ah have you configured a certificate in We manually created a letsencrypt certificate for the server so just recycled that: |
|
Yep, definitely, although it is self-signed (but that shouldn't be a problem). I appended the last three lines from the default settings ( Configuration: |
|
If you aren't changing the values, there shouldn't be a need to include the defaults I would have hoped! Have you verified that certificate file exists? There have been some .cert/.crt mix ups recently. |
|
Hi there, Yes, both files definitely exist: Sorry that the solution isn't more obvious ;-) |
|
Can you try SSL connecting over 25 from your terminal? The self signed part might be an issue, are you able to generate a real certificate? Finally, heres my |
|
When I do, I get the following error: And again, from a server: I could try using a certificate signed by a CA, but that shouldn't matter. After all, it is an SSL certificate. |
|
Our Postal is running on Ubuntu 16.04 with openssl version 1.0.2g, are you running the same? |
|
Yes, we are: Anyway, I replaced the certificate with a Let's Encrypt one. Same error. |
|
I also tried replacing the path to the certificate and the private key with the full path ( |
|
I have a feeling Postal doesn't pass SSL through at all. When I telnet to port 25, 2525 or 587, I can use I'm able to execute But from what I remember, STARTTLS should be chosen automatically. Or am I mistaken? |
|
Traditionally you would have opportunistic/explicit SSL/TLS with STARTTLS on port 25 and/or 587 and implicit SSL/TLS (depreciated) on port 465. The key difference is that with opportunistic/explicit SSL/TLS the mail server advertises that it has the STARTTLS capability and if the client supports it then it issues the STARTTLS command to upgrade the connection from plain text to TLS encrypted. You can test opportunistic/explicit SSL/TLS using the openssl client as follows:
Whereas with implicit SSL/TLS you would use: With |
|
Thanks for the explanation!
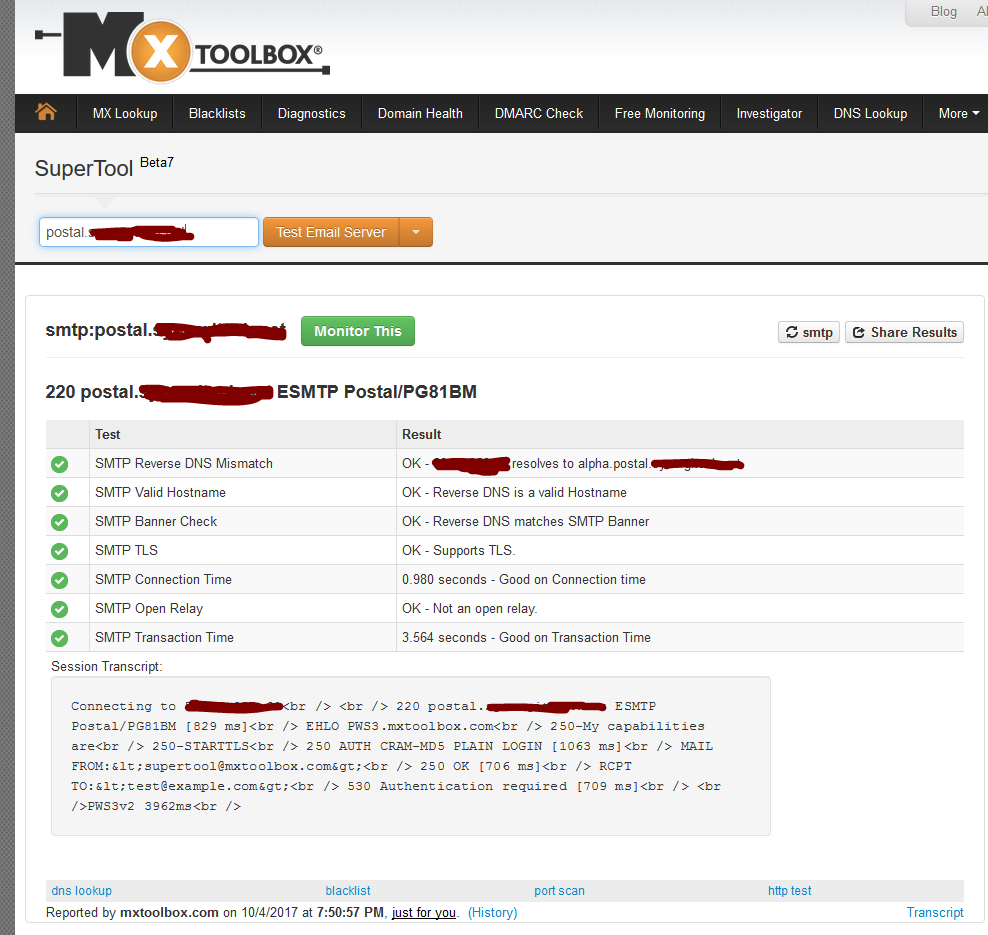
Also mxtoolbox is pretty happy So @WilliamDEdwards is everything working now? |
|
Hi, It does not work yet. On MxToolbox it mentions "SMTP TLS | OK - Supports TLS." However, it still doesn't work in AcyMailing which is a problem... |
|
Is AcyMailing expecting implicit or explicit TLS? |
|
"Acymailing supports both implicit or explicit TLS connections." |
|
For some reason it suddenly works now. Just out of nowhere... |
|
I did face the same problems, after a lot of testing I found the problem to be related that the postal user couldn't read the letsencrypt certs. To test if this is the case I did face a Permission denied. Solution was to give read access to both etc/letsencrypt/live and etc/letsencrypt/archive as the cert in /live is a symlink to the archive dir. Hope this help someone else having the same problem in the future. |
Hello,
Currently, we have STARTTLS enabled on port 25 on Postal. I am aware that port 25 using STARTTLS functions perfectly fine. However, AcyMailing (a Joomla! plugin for newsletters and the like) refuses to send email over that port. For usage of TLS (or SSL for that matter) it requires email to be sent from either port 465 or 587, naturally, the latter being preferred.
This boils down to the question: how do we send TLS email from port 587, despite it functioning on port 25?
Thanks.
The text was updated successfully, but these errors were encountered: