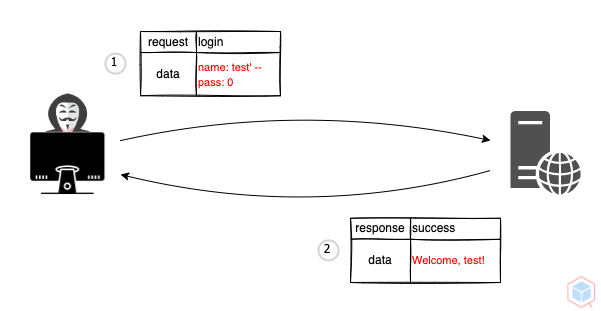
A threat actor may alter structured query language (SQL) query to read, modify and write to the database or execute administrative commands for further chained attacks (The threat actor may get output or verbose errors while performing the injection)
- Threat actor sends a malicious SQL query to a vulnerable target
- The target process the query and return the result
app.post("/query", (request, response) => {
const query = "SELECT * FROM users WHERE username = '"+ request.body.username +"' AND password = '"+ request.body.password +"'"
connection.query(query, (error, result) => {
response.json({"result":result,"err":error});
});
});test';--
Welcome, test!
High
- SQL injection
- Read & write data
- Command execution
- Input validation
- Parametrized queries
- Stored procedures
85b0dbbc-1d39-4d96-9816-319276d2c0e2