New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fix ELF argv encoding #1303
Fix ELF argv encoding #1303
Conversation
// gcc -fno-stack-protector -no-pie -m32 bof.c -o bof.bin
#include <stdio.h>
#include <string.h>
void never_called() {
puts("qiling power");
}
int fun(char *str) {
char buffer[20];
strcpy(buffer, str);
return 0;
}
int main(int argc, char *argv[]) {
fun(argv[1]);
return 0;
}from qiling import Qiling
from qiling.const import QL_VERBOSE
ql = Qiling(["./bof.bin", "A"*32 + "\x86\x91\x04\x08"], "/", verbose=QL_VERBOSE.DEFAULT)
ql.run()Platform: Here is the minimum test script i use to test this PR, and I found out that the output is different from the normal execution. The payload does nothing but simply overwrite saved-eip in stack with another function address for hijacking execution flow. qiling logstraceExpected outputtrace log (verbose=DISASM)Also, I noticed that trace log is some how incomplete, the function |
|
nvm, i got it though. I think this PR is good to merge. |
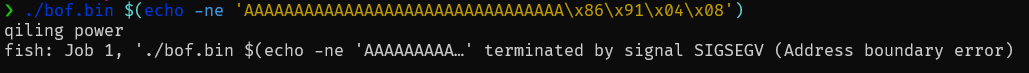

Changed ELF argv encoding from "utf-8" to "latin" to avoid corruption of specially crafted command line arguments (more details in the fixed issue).
Fixes #1269