-
Notifications
You must be signed in to change notification settings - Fork 77
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Extension does not play well with Run-From-Zip deployment #239
Comments
|
Thanks for leaving this here. I found your message a bit later than I wished I did. My problem was indeed that the error I received was that ACME "could not reach the token". But the token was never written in the .well-known folder because - as you mentioned - the wwwroot folder is read-only in RunFromZip. However, setting a 0 to that setting does not solve the problem ;). On top of that, my angular app was responsible for routing so I got a bit confused if this should be solved before angular or within angular. So, before I got to trying out your solution, I got it to work by downgrading the deployment method. This finally worked after many different combinations:
web.config.in.subfolder.txt - When the lets encrypt extension has write access to its acme_challenge folder, I think it generates this web.config file. This is not a file for in the root wwwroot folder. I will keep your option in mind, while keeping an eye on this thread. |
|
I just updated one of my sites to use the run from package setup and the way I worked around the
My site doesn't use the
|
|
I didn't want to use a virtual path as @xt0rted did, however, I managed to get this to work by:
Sample Code (.NET Standard): {
log.LogInformation($"Processing Let's Encrypt Request for Code: {code}");
var content = File.ReadAllText(@"D:\home\lets-encrypt\.well-known\acme-challenge\"+code);
return new OkObjectResult(content);
}This approach worked just fine for me and it is much easier to automate without the extra virtual directory. |
|
This was instrumental in getting me unblocked and cert issued. Thanks everyone. Couple of additional wiki notes/my findings as a new comer:
Additionally, in light of shifting limitations of |
|
@iyerusad a few comments, thanks for your feedback. %WEBSITE_HOSTNAME% is well supported, it just expands an environment variable. The WEBSITE_HOSTNAME environment variable is always present it is set by the app service. It is something newer that they support localhost. The route in the C# is not needed as it is implicit from the function and parameter name. I can't really change the default behavior of writing to wwwroot, as it would be a breaking change, unless the extension in some otherway can ensure that it work without the users configuring anything extra. I can't think of a way to do that atm. Suggestions are welcome :) Also please take a look at release 0.8.9 it now supports not writing the challenge file to disk, but instead writing it to blob-storage, that could maybe make life easier for those of you that use deploy from zip. |
|
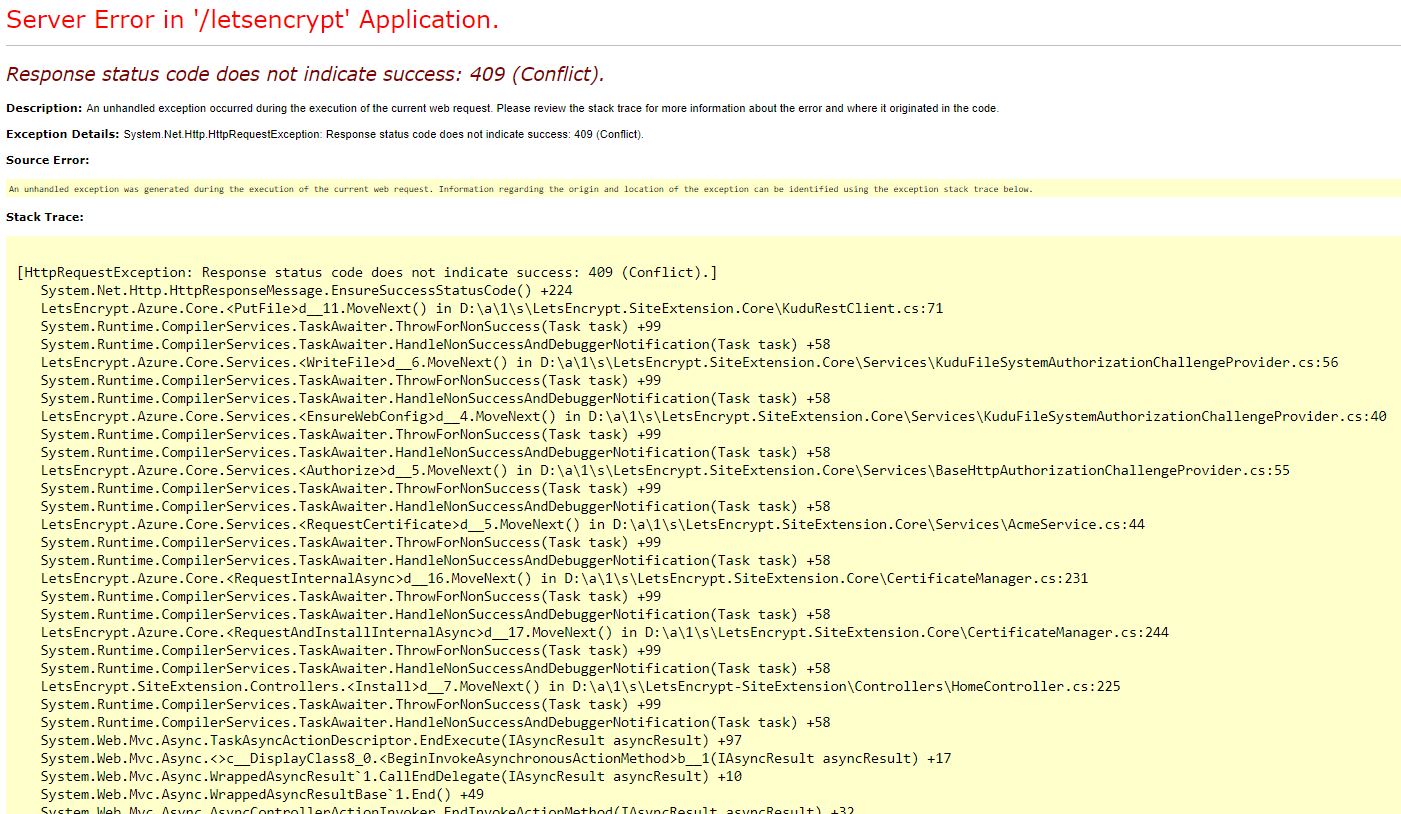
Looks like VSTS deploys default to run from zip now, the Kudu error message has changed too (pasting to make this issue easier to find in search) Server Error in '/letsencrypt' Application. And the stack trace starts with: |
|
@danzel thanks for letting me know. Guess I have to play around with deploy from zip, to make sure it works as smooth as possible. |
|
@xt0rted Thanks so much, this works a treat after a few days of turmoil. !! :) |
|
@tomaszzmuda nothing have been done to fix the problem from the extension side of things. |
|
azure pipeline user, meet the same problem. |
|
plus, microsoft maybe going to work on it? https://feedback.azure.com/forums/170024-additional-services/suggestions/16957756-add-integration-with-let-s-encrypt |
|
Have you heard anything new from Microsoft? It sounds like radio silence to me still. |
|
Emmmmm nope. It's one of the top feedback but opened 2 yrs ago. |
|
Fixed in 0.9.4 |
|
I have the same problem. Does not work out of the box... |
Microsoft has introduced a new way to deploy your WebApps to Azure called Run-From-Zip that will be out of preview at the end of Q3. This method basically allows you to mount a zip file to the wwwroot folder of your app at startup. This comes with some great benefits but also a big downside: the wwwroot folder becomes read-only.
The Let's Encrypt site extension relies on writing the to the wwwroot folder (or whatever folder is specified in
letsencrypt:WebRootPath) for serving the answer of the ACME challenge.I've tried using the extension with Run-From-Zip deployment but the process of requesting a certificate fails. The Let's Encrypt error report tells me that the request to
https://my-site.ext/.well-known/acme-challenge/{challenge}failed because of a HTTP 404 (Not Found).I would expect this process to fail since the wwwroot folder is frozen (well, actually I would expect the process to fail at writing the answer to the wwwroot folder but I might not completely understand the internals of the Run-From-Zip method).
My current workaround is to have the extension write the answers to a different folder (d:\home\data\letsencrypt\challenges) by setting the
letsencrypt:WebRootPathand have the application serving any requests to/.well-known/acme-challenge/{challenge}.A better solution would be if the extension did not rely on writing to the wwwroot folder for serving the answers but handled it internally by having a handler listening to the path
/.well-known/acme-challenge/{challenge}instead.The text was updated successfully, but these errors were encountered: