New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
TLS 1.3 Cipher Strength 90%? #636
Comments
|
Cipher strength is calculated as per this guide |
|
You have to remove |
|
Ah I got the mistake... The SSL Labs test isn't refreshing the ciphers / making the test again, so the 128 Bit cipher doesn't disappear. https://dev.ssllabs.com/ssltest/analyze.html?d=next-server.eu&s=46.251.251.145&hideResults=on&latest Is that behaviour normal? So: TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-256-GCM-SHA384 are the only 2 TLS 1.3 ciphers that can get 100%? |
|
Clearing the cache this results in the same, did you restart your nginx server after removing the cipher? |
|
Oh, one thing I’ve just remembered is that it seems to me OpenSSL splitted specifying TLS 1.3 ciphers from previous version, so that nginx cannot currently set TLS 1.3 ciphers. |
Sure :P
How do you mean that? https://www.openssl.org/blog/blog/2017/05/04/tlsv1.3/
But in my setting they are set :O |
Yes, exactly. nginx lacks the code to handle that AFAIK. |
|
Wow okay, that's totally new to me. Have you experienced the same, or heard of someone who has the same issue / read somewhere that the code is missing? |
|
I’ve read this in OpenSSL changelog: And a bit further down the notes: I don’t know of any project that has updated its code to use this new API. |
|
(And the PR that changed this openssl/openssl#5392) |
|
Ahh thanks for your research! On Openssl side: So adding / changing the new API for TLS1.3 here: would probably fix it (there are maybe more files to change I guess). |
|
Yeah, they are more changes required depending on how they want to support this. If you want to do a dirty try with only TLS 1.3 support, you could swap the new API in place of the TLS 1.2 one in nginx and see what it gives. |
|
You should not remove this cipher. draft-ietf-tls-tls13-28 RFC says:
IMHO SSLlabs should change the scoring. When there is a better cipher available and ordered before the mandatory AES128 ciphers for HTTP/2 with TLS 1.2 or TLS 1.3 it should be 100% not 90% for "Cipher Strength". Also supporting secp256r1 is mandatory for TLS 1.3 and reduces the score for "Key Exchange" by 10%. Even when there is secp384r1 available and preferred by the server. This also should give 100% and not 90% for "Key Exchange". |
|
Or decide to not be standard compliant. I don’t trust NIST ECC, so no secp256r1 on my servers. And I’m not sure whether the scoring should be changed: you are less secure than someone without 128-bits equivalent crypto. However, maybe a warning should be issued regarding standard compliance if you reach 100%, and when you are at 90% have some info printed alongside it saying that 100% cannot be reached within RFC compliance. |
|
The notion that a better available cipher is a solution seems to be not understanding attack vectors - the server will "prefer" the highest cipher the client can support. Attackers simply use clients that declare they do not have the highest ciphers, and the fun begins. From a broader perspective, the security in open source depends on projects such as this one to independently confirm other projects as secure. If the IETF publishes 8-bit ciphers into a standard, OpenSSL adds 8-bit ciphers to their default configuration and requires its use, does that mean SSL Labs should declare 100%, except for when 8-bit ciphers are used? No! It means the server gets 0% and F. This concept applies to 128-bit as well; if SSL Labs determines 128-bit gets 80%, then this is the case no matter what IETF or OpenSSL publish. |
|
Has someone tested that? |
I've tested the equivalent option in Apache 2.4.37 for TLSv1.2: With just the TLS_AES_256_GCM_SHA384 & TLS_CHACHA20_POLY1305_SHA256 TLS1.3 ciphers and without the secp256r1 I got 100% key exchange score. |
|
@shoujii I tried, it changes output of |
|
Someone have understood how to have this TLS 1.3 ciphers order with nginx and OpenSSL: ? |
|
@iz8mbw it's impossible right now. Nginx cannot use new OpenSSL API for TLS v1.3 yet. P.S. Why you need this order? Many processors support AES-NI, so proceed 256 as fast as 128. |
|
That does not appear to be the case, if I'm benchmarking correctly. openssl speed -evp aes-256-cbc is consistently ~30% slower than aes-128-cbc (or to put it the other way around, 128 is 40% faster than 256). AES-NI makes things five to six times faster - evp without it has a speedup, too - but the difference between 128 and 256 remains proportional. They may equally be 'fast enough', but it depends on your requirements. |
|
@GreenReaper my point: Site content affects speed MUCH more than AES choice. So I will just choose more secure AES256. For mobile devices there is also ChaCha20-Poly1305 that is also doesn't require AES-NI and still performs well enough in both cases: speed and security. |
I’m replying here to this now deleted message: the standard might have requirements that are not compatible with security, yes. For instance, until recently the mandatory cipher in previous versions of TLS was a 3DES one… Or even currently, you have to support NIST elliptic curves. So yes, if you want highest security, you cannot be standard-compliant. |
|
Hi all. |
|
That should not be required if you are willing to change cipher order preferences globally. Just set up a Ciphersuites entry in /etc/ssl/openssl.conf (I suggest also using the listed Options for the benefit of mobile devices). |
|
Ok. |
|
At a guess, the version of OpenSSL you compiled will be using the --prefix configure argument to specify where it stores its own configuration files.
Of course you could also change its compiled-in order. Personally I would tend towards using fewer patches if a config can achieve the same goal.
…________________________________
From: Fabio <notifications@github.com>
Sent: Tuesday, January 22, 2019 1:53:48 PM
To: ssllabs/ssllabs-scan
Cc: GreenReaper; Mention
Subject: Re: [ssllabs/ssllabs-scan] TLS 1.3 Cipher Strength 90%? (#636)
Ok.
But I did not understand how manage "openssl.cnf"...
On my Linux system I have two OpenSSL, one is the default of my Linux distro (1.0.1t) and the other is OpenSSL 1.1.1a built by myself and located in "/opt/ssl".
Nginx (also built by me from source code) is "linked" to the OpenSSL 1.1.1a.
Well, now, to properly set the TLSv1.3 Ciphers order using "openssl.cnf", what and how should I do that?
Thanks.
—
You are receiving this because you were mentioned.
Reply to this email directly, view it on GitHub<#636 (comment)>, or mute the thread<https://github.com/notifications/unsubscribe-auth/AAXYQ_RpXb0OsKDBuO9mw-QUkBhl0d-yks5vFxfsgaJpZM4VJY_W>.
|
|
No matter what I do, the server keeps forcing the mandatory TLS_AES_128_GCM_SHA256 cipher. To be honest, SSL Labs should just change their system to give us 100% with this cipher enabled. |
|
Just tried this, I edited both |
Depending on the distribution the files could be located somewhere else like in my case /usr/lib/ssl. Assuming the solution proposed by wibimaster works. |
|
You can use @ckaspers Did you patch at the start of the file and not the bottom ? Here is a default openssl.cnf, without comments, and with the patch you can see : Of course my certificate was 4096 bits and dhparam too, to get full 100%. I didn't reboot my server, only restarted nginx |
You triggered me here. I think you creating self-signed certificate using openssl, is that right? While others may use Let's encrypt as CA ;). Even then, you can create 4096 bits certificates via Let's Encrypt. I do it already. Change your |
Oh no, I'm using Letsencrypt too ;) |
|
Maybe you can check your openssl configuration after editing it : It should output : Be aware that this modification is system wide. If you want to edit this configuration only for nginx, you have to create another openssl configuration file and modify nginx service to use it (environement variable) |
|
I checked and my path is also /usr/lib/ssl/openssl.cnf which is a symlink to /etc/ssl/openssl.cnf. If it makes any difference at all I am running Ubuntu 20.04 LTS on a Raspberry Pi 4B 4GB. Here's my openssl.cnf file: https://pastebin.com/w5Bxpnsp. And this is my ssl.conf file in /etc/nginx: It just keeps forcing the "mandatory" 128 bit cipher for whatever reason... |
|
Respectfully, the last two days of comments seem unrelated to the bug report about Qualys' handing of TLS 1.3 scoring. We all want this solved. But it doesn't seem to me that this bug report is the place to figure out a workaround, that doesn't involve Qualys actually fixing the problem. |
|
It’s really funny, I opened this issue nearly 2 years ago and it still persists. I’m really sad that there is no solution without less or more dirty workarounds:/ |
@shoujii It is quite disappointing, isn't it. I have several times to implement @wibimaster's solution, perhaps you could upgrade your OpenSSL to the latest The only difference I can see between our configurations is the: [ CA_default ]
dir = /etc/ssl |
|
@wibimaster hmm, I swear I had that in there last time I tested though. I don't know what changed, but everything is working correctly and I have 100% now. |
Glad to see that it works for you :) About all this thread : If Qualys says "Having a 128 bit in ciphers list is not secure", I follow them. But you can update this configuration, you can have a specific openssl configuration file for nginx if you don't want to have this patch system-wide, and you don't have to build anything. For this specific thread, you can have 100% with TLSv1.3 quite easily. Maybe another thread with "TLSv1.3 with 128 bits in ciphers list should be considered secured" could be opened, but I'm not an expert. |
|
Managed to get it working by purging my OpenSSL
rm -rf /etc/ssl/*
pacman -S openssl..creating a # Ciphersuites Configuration
MinProtocol = TLSv1.2
CipherString = DEFAULT@SECLEVEL=2
Ciphersuites = TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256
Options = ServerPreference,PrioritizeChaCha..inserting the following lines into @@ -11,6 +11,17 @@
# defined.
HOME = .
+openssl_conf = default_conf
+
+[ default_conf ]
+ssl_conf = ssl_section
+
+[ ssl_section ]
+system_default = ssl_sys_section
+
+[ ssl_sys_section ]
+.include /etc/ssl/ciphersuites.cnf
+
# Extra OBJECT IDENTIFIER info:
#oid_file = $ENV::HOME/.oid
oid_section = new_oids..and finally restarting Nginx (a systemctl restart nginxIf it doesn't immediately work, try do a reboot. Nginx TLS configurations
Thanks @wibimaster and @ckaspers! 🎉 |
|
Sorry but this doesn't give all 100% can you reupload your screen-shot with date? |
Which one ? Mine or Axieum's ? |
|
Axieum's ALL:!AES128:!CAMELLIA128:!CAMELLIA:!ARIA128:!RSA:!SEED:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK:!DHE-RSA-AES256:!ECDHE-RSA-AES256-SHA384:!DHE-RSA-AES256-SHA256:!ECDHE-RSA-AES256-SHA:!DHE-RSA-AES256-SHA:@strength with updated etc/ssl/openssl.cnf |
|
@wibimaster comment from 18th May did the trick for me, on CentOS8 - just needed to alter 1 line in the openssl config Here is the part of my ansible playbook that takes care of this |
|
TLS_AES_128_GCM_SHA256 is a required cipher for TLS 1.3. RFC 8446 mandates it. In fact, there is a considerable argument to be made that AES 128 is actually more secure than something using AES 256. (Link) Openssl's default configuration is correct here. The correct fix, in the end, is for Qualys to correct their scoring. You guys are arguably weakening your security by removing TLS_AES_128_GCM_SHA256 -- just so that you can get 100%. |
|
You're right that TLS_AES_128_GCM_SHA256 is a mandated cipher for a TLS 1.3 implementation, but no one says my server has to provide it. Suppose an RFC for 1.3 requires a CIPHER with DES and 256 RSA, would you provide it? But I agree that an AES128 should not lower the rating to 90% because it is not actually insecure, but don't argue with an RFC that doesn't guarantee any security. |
|
Folks, just scan a Google website (the only one I could find that uses ECDSA certificates instead of RSA) and look at their results. It's a plain B. That's not even green anymore. So I, for one, am quite happy to get an A with some 90% scores. I don't see the difference between 128 and 256 bit encryption, which translates roughly to "practically unbreakable" and "practically unbreakable". |
|
I just wish to confirm that the solution from wibimaster works on openssl 1.1.1i and nginx 1.19.6. |
|
Note: starting from nginx 1.19.4 and later you can specify TLSv1.3 cipher suites right in the nginx config: I used this to achieve 100/100/100/100 (in conjunction with EC P-384 certificate signed by E1 Let's Encrypt intermediate): It screws some old clients, and p384 is much slower than p256 (on my VPS it's even twice slower than rsa2048), so it's better not to use this in production, unless you are extremely paranoid about the possibility of cracking AES-128 and/or EC P-256. |
|
Huge thanks @SagePtr - Good to know nginx can specify the ciphers directly; so we do not need to play with openssl.cnf. I liked your comments that helped to research further. The "old clients" are actually include Chrome 49 (for Win XP), Firefox 31 (for Win 7), Safari 8 (for Yosemite) and older versions and it makes no sense to use them in August 2021. So the issue of incompatibility is effectively for visitors using Android 6 or older; which in 2021 is less than 5% of the total Android population anyway and no longer receive security updates. So each one has to take a business decision for themselves, whether to provide backward compatibility with obsolete browsers and operating systems. As my servers CPU usage is very low and the pagespeed result is acceptable (with p384); there was no need to use p256. I find it is difficult to distinguish between extreme paranoids, score junkies and good cyber practices. Their venn diagrams overlap! |
|
@SagePtr thanks, with this config I get 100/100/100/100. |
Tested with openssl s_client and figured it out: when i specify -curve secp384r1 parameter in the client, the 0-RTT data is accepted, but when i don't specify any curve list, the 0-RTT data is rejected. If i specify X25519 among ssl_ecdh_curve list (on the server) - 0-RTT works anyway, but drops kex score to 90. Ideally, 0-RTT should not be used in a strong crypto setup, as it slightly reduces the security of the first packet for the sake of a faster handshake. |
|
@SagePtr thanks! |


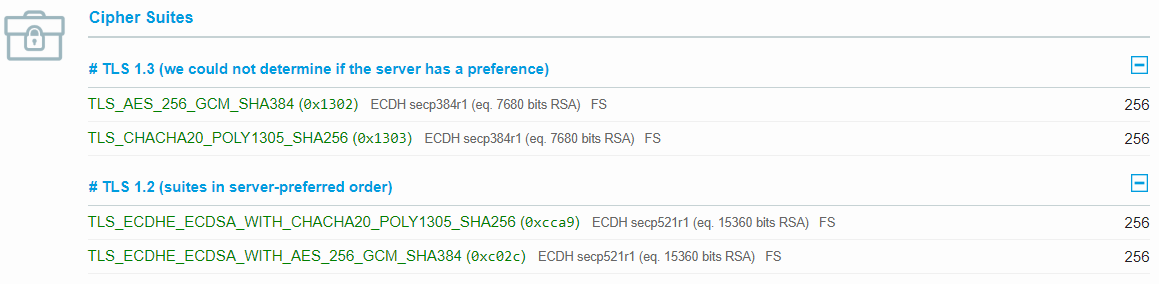
Hey there,
I tested my site -> nginx 1.15.1 using Openssl 1.1.1 pre release 8 on
with the following cipher list:
TLS13-CHACHA20-POLY1305-SHA256:TLS13-AES-256-GCM-SHA384:TLS13-AES-128-GCM-SHA256and I only got 90% Cipher Strength.
Am I doing something wrong?
There are only 5 TLS 1.3 Ciphers supported by openssl yet.
The text was updated successfully, but these errors were encountered: