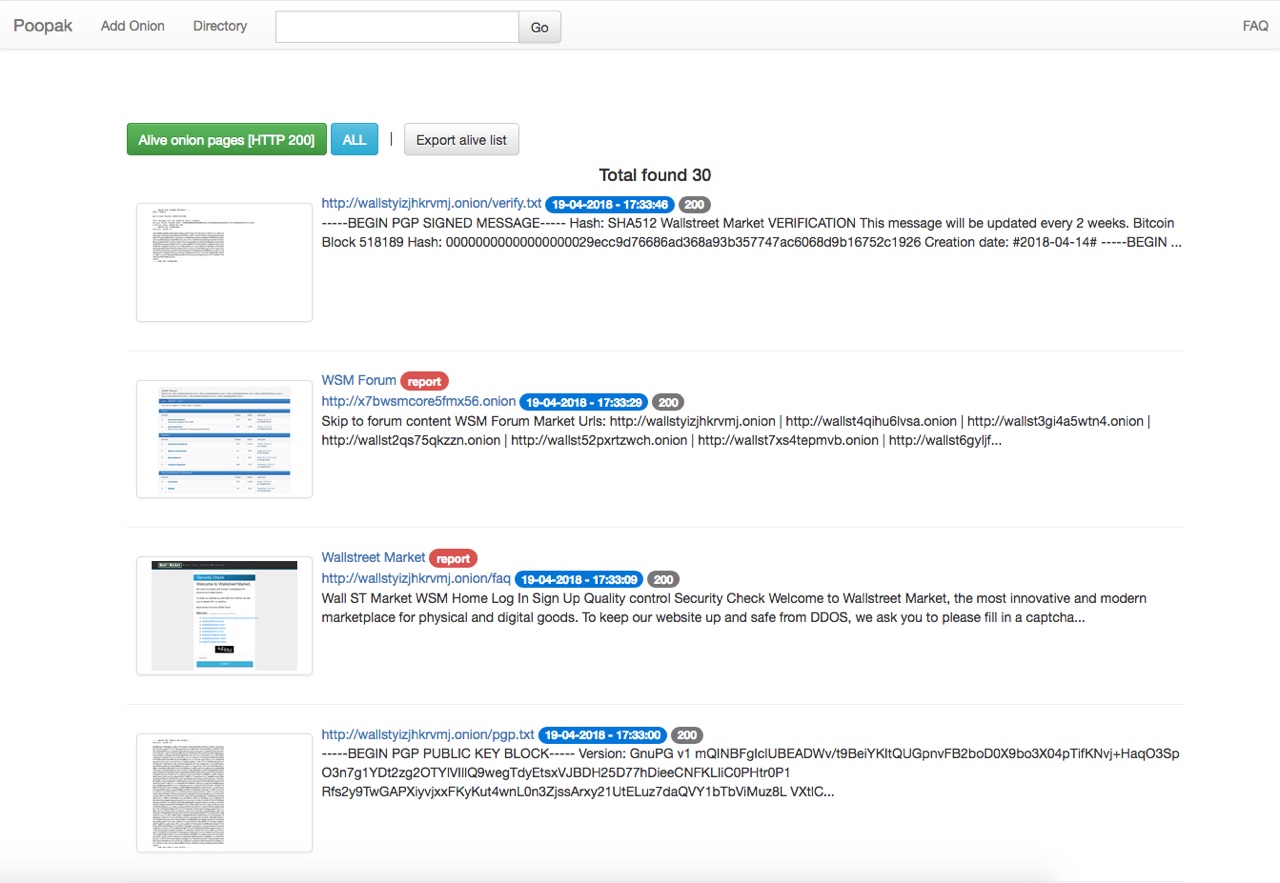
POOPAK | TOR Hidden Service Crawler
This is an experimental application for crawling, scanning and data gathering from TOR hidden services.
- Multi-level in-depth crawling using CURL
- Link extractor
- Extract Emails/BTC/ETH/XMR addresses
- Extract EXIF meta data
- Screenshot (using Splash)
- Subject detector (using Spacy)
- Port Scanner
- Extract report from a hidden service (CSV/PDF)
- Fulltext search through the directory
- Language detection
- Web application security scanning (using Arachni) - [Under Developing]
- Docker based and Web UI
This software is made available under the GPL v.3 license. It means if you run a modified program on a server and let other users communicate with it there, your server must also allow them to download the source code corresponding to the modified version running there.
- Docker (tested on Docker version 19.03.8)
- Docker Compose (tested on version 1.25.0)
- Python 3
- pipenv
Just run application with docker-compose:
docker-compose up -d
and next point your browser to localhost.
Accessing the administrative dashboard can be done at /dashboard. By default, the credentials are:
admin/123qweasdzxc
This allows you to upload seeds and view hidden instance crawl details