Exploiting Some Vulnerabilities of WP 4.2.2 for the Codepath cybersecurity class
Time spent: 5 hours spent in total
Objective: Find, analyze, recreate, and document five vulnerabilities affecting an old version of WordPress (4.2.2)
- (Required) WordPress 4.0-4.7.2 - Authenticated Stored Cross-Site Scripting (XSS) in YouTube URL Embeds/ CVE-2015-6535
- Summary: Youtube URL embed shortcode allows for a XSS attack. Inserting a script within a youtube url with escape sequences \x3c or \x3c instead of < and >.
- Vulnerability types: XSS
- Tested in version: 4.2.2
- Fixed in version: 4.2.13
- GIF Walkthrough:
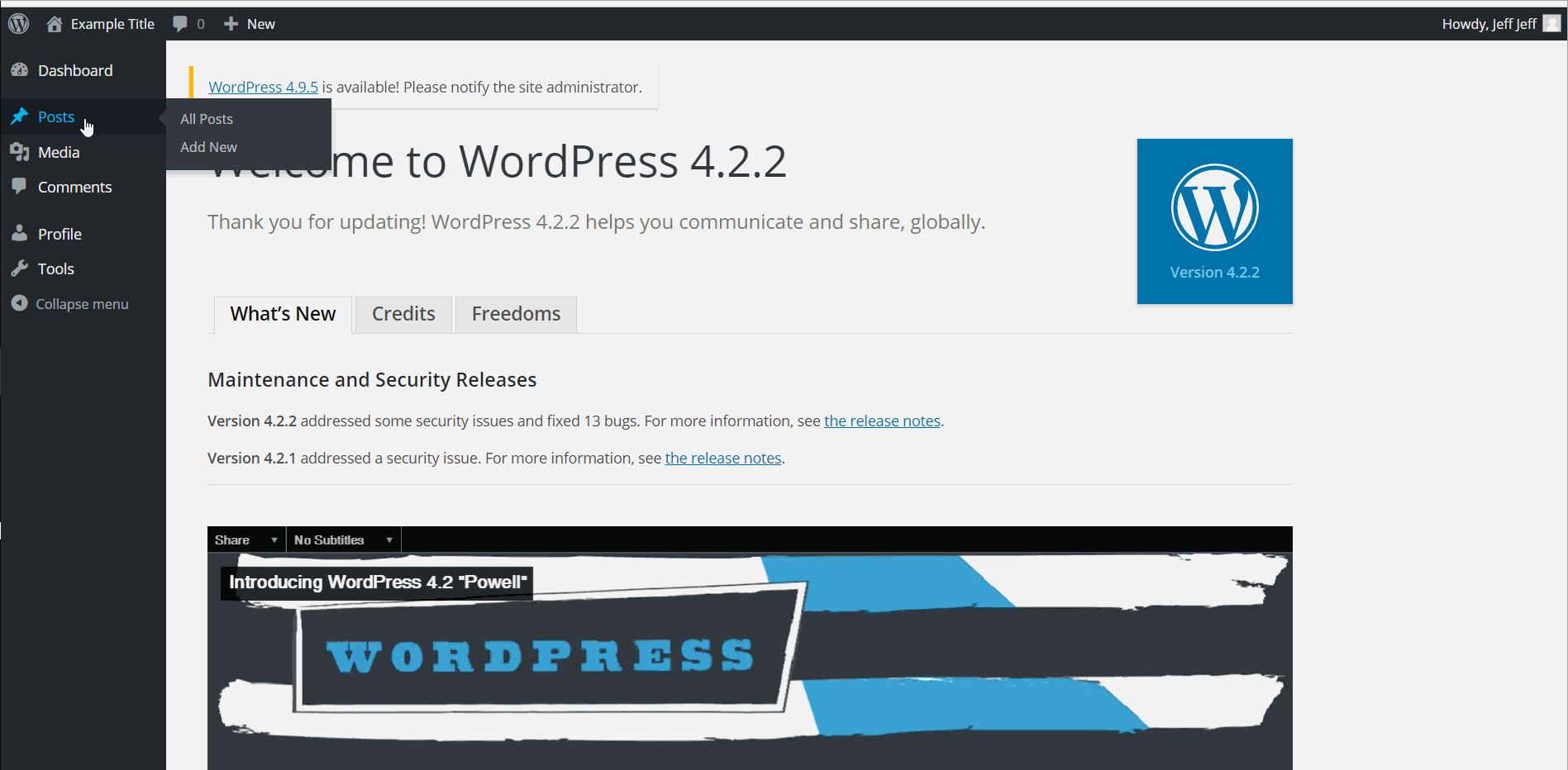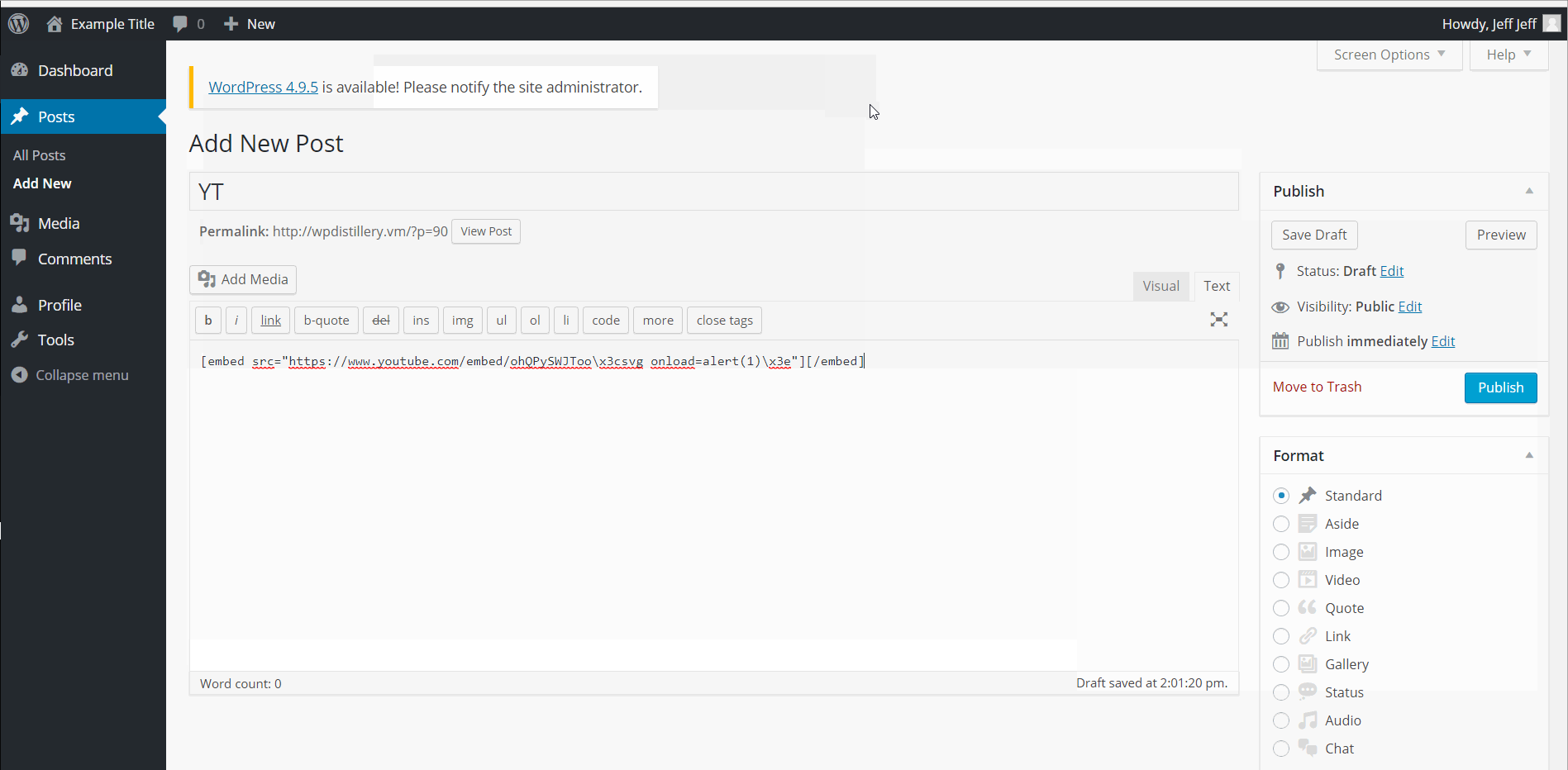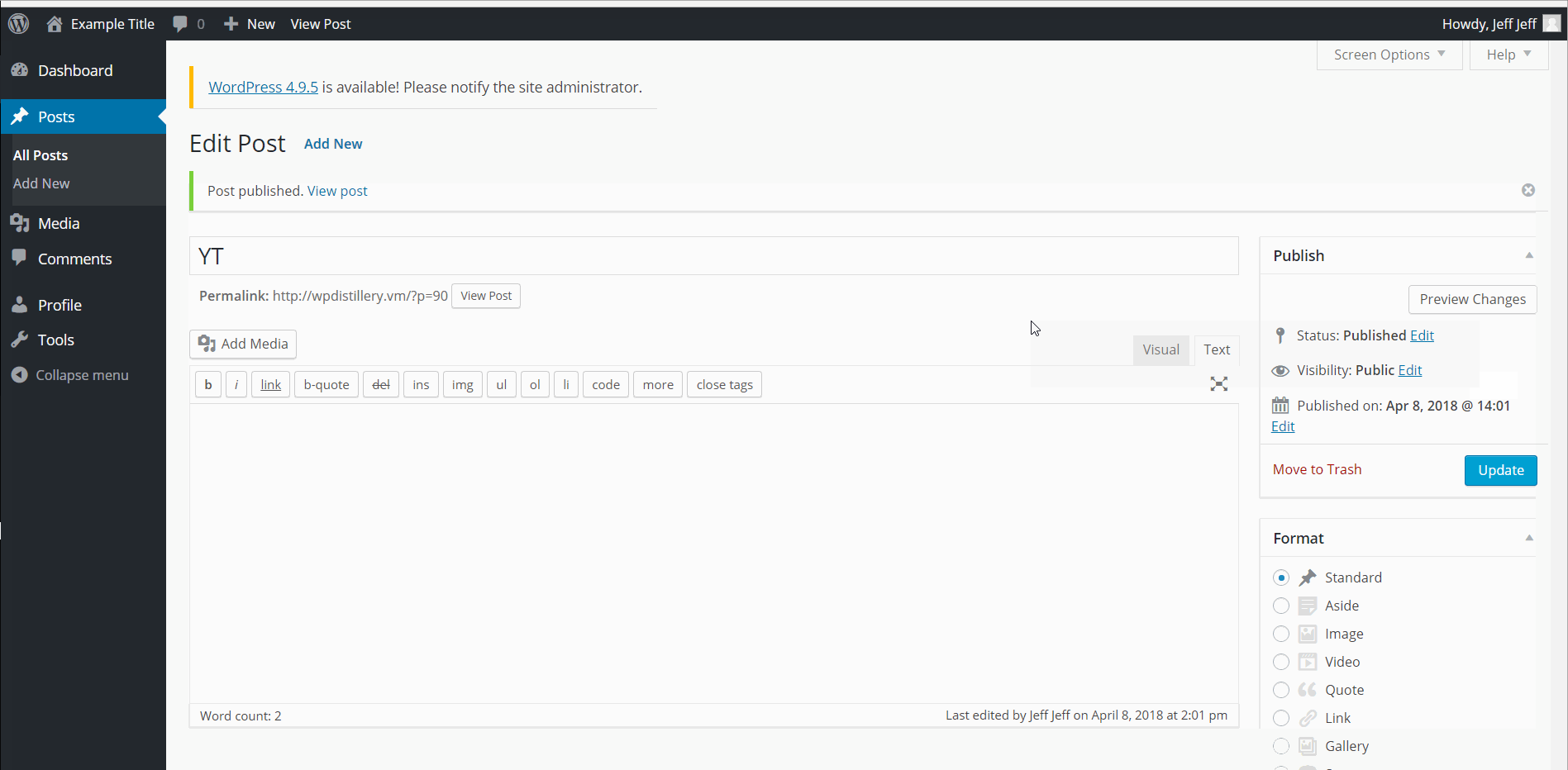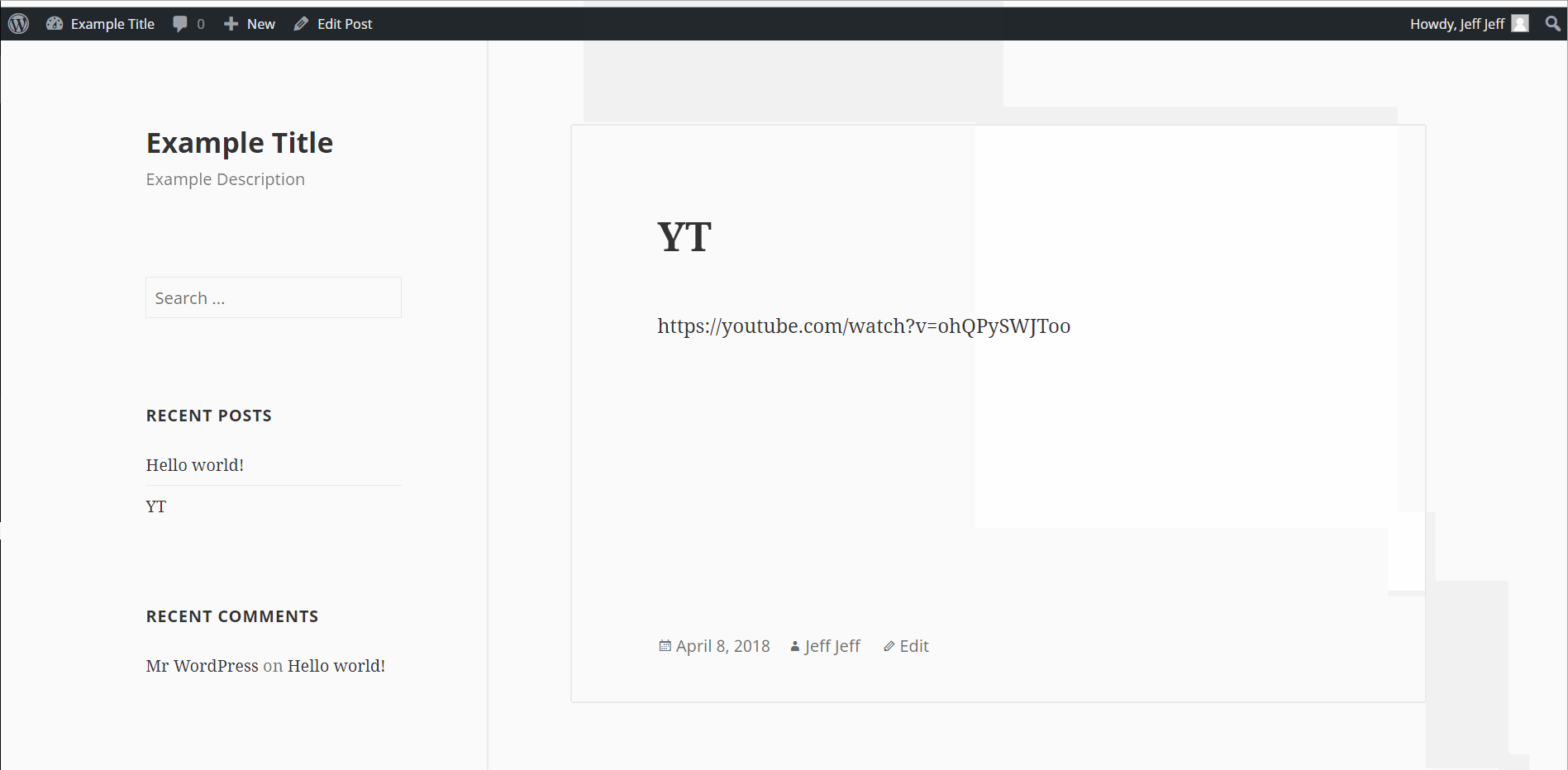
- Create a new post and embed any YouTube link in the text box. After the link, insert your XSS script with < replaced by \x3c and replaced by \x3e.
- Affected source code:
- (Required) WordPress 3.7-4.4 - Authenticated Stored Cross-Site Scripting (XSS)/ CVE-2016-1564
- Summary:
- Vulnerability types: XSS
- Tested in version: 4.2.2
- Fixed in version: 4.4.1
- GIF Walkthrough:

- Steps to recreate: Login as admin and create a new post. In the text of the post, add the alert script at the end of the link.
- Affected source code:
- (Required) WordPress <= 4.3 - Authenticated Shortcode Tags Cross-Site Scripting (XSS)/ CVE-2015-5714
- Summary: Insert a XSS attack within the HTML shortcode tag.
- Vulnerability types: XSS
- Tested in version: 4.2.2
- Fixed in version: 4.2.5
- GIF Walkthrough:

- Steps to recreate: Create a new post and add the XSS alert inside a tag.
- Affected source code:
- (Optional) UserEenumeration Using Wpscan
- Summary: The way the WordPress authentication is set up, different error messages are shown when a wrong passowrd is entered for an existing and non-existing user. From that, the user enumeration can be used to identify all users. Since most of them use easy-to-guess passwords, a brute force attack (Ex.: wordlist attack with rockyou.txt) can be used to hack into an account.
- Vulnerability types: User enumeration
- Tested in version: 4.2.2
- Fixed in version: Not fixed
- GIF Walkthrough:

- Steps to recreate: Run WPScan with the following command: "wpscan --url [WP URL] --enumerate u"
- Affected source code:
- (Optional) WordPress 3.6.0-4.7.2 - Authenticated Cross-Site Scripting (XSS) via Media File Metadata/ CVE-2017-6814
- Summary:
- Vulnerability types:
- Tested in version:
- Fixed in version:
- GIF Walkthrough:

- Steps to recreate:
- Affected source code:
GIFs created with LiceCap.
Copyright [2018] [Anastasiia Timashova]
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.