-
Notifications
You must be signed in to change notification settings - Fork 30
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
SCA Global Testing #97
Comments
Valgrind reportsExecuting SCA module with test policies. OUTDATED. FIXED IN: #97 (comment) wazuh-modulesd wazuh-db ossec-analysisd |
|
There was an error introduced merging 3.10 in the branch. The commit wazuh/wazuh@2b6f8f6 solves the error. This is the new Valgrind report of |
|
Scan build |
|
When launching a scan with an invalid YAML file, Valgrind reports the next summary: OUTDATED. FIXED IN #97 (comment) |
|
Fixed memory leak when parsing an invalid YAML file. Solved in this commit. |
|
OUTDATED. FIXED IN wazuh/wazuh@bc1222d There was a problem when trying to check the integrity from file sca_win_registry_test_suite.yml. SCA module: DB: The database orders by ID the results obtained, but the agent doesn't. This leads to an infinite loop of integrity checksum failures. For example, if the YAML policy has the IDs 1,0,2,3,4, and the results are |
|
Dr. Memory report: |
|
Adding a check which runs the command Generates an error of memory allocation: The timeout doesn't work for this command as it generates an output and the timeout checks whether a command does show output at a certain threshold. |
|
Update from 3.9 to 3.10 and run an SCA scan: Databases are correctly purged, they do not generate any error. With this update, the configuration is still the same, this means that it will show this kind of messages when it has been updated. |
|
Agent remote configuration OUTDATED. FIXED IN #97 (comment) With an agent having its default SCA configuration: With the next agent.conf set: We obtain the next result: And after finishing the evaluation of the first two files: Also, notice that we have set the policy cis_debian9_L2.yml file to disabled in the remote configuration, but |
The behaviour of SCA when a policy is disabledThe Wazuh manager removes the information of a disabled policy when a new scan is received. |
|
Checking the correct policies for Windows are installed at ruleset/sca Every Windows has only sca_win_audit.yml at ruleset/sca, without considering the Windows version. For example, A Windows Server 2012 does not have a cis_win2012r2_memberL1.yml file. |
|
Agent remote configuration The problem was that the array of policies to be scanned was adding every file included in the ossec.conf file. Checking if the policy has already been added fixes the issue. Testing
Log sample Configuration blocks: ossec.log output: |
Integrity testingDelete a check from the DB Server side:
Agent side at next scan: Server side after receiving the scan: Changing a check from a policy Server side: Agent side: Logs Agent side: Server side: New check in the server: |
|
Using Changing the After the 60 seconds from the Same results after running several subsequent scans. |
Windows testingDisabling a policy Setting a complete path to a policy different than the one by default Shows the next message, however the policy is correctly scanned. It adds the directory by default, |
|
Extended testing on disabling a policy on Windows while the agent is running
Until the agent is restarted the agent logs a Warning: When the agent is restarted and the first SCA scan is send the DB purges that policy: |
|
Memory Use of Windows Agent Powershell script to get the Memory on real time: Configuration: |
|
Script: Configuration: Frequency: 1 minute. Changes during execution: Half time IDs repeated and the other half valid policy (Check repeated ID and integrity) |
|
SCA actions with events and alerts generated
|
|
The SCA refactor has been merged, so I am closing this issue. |
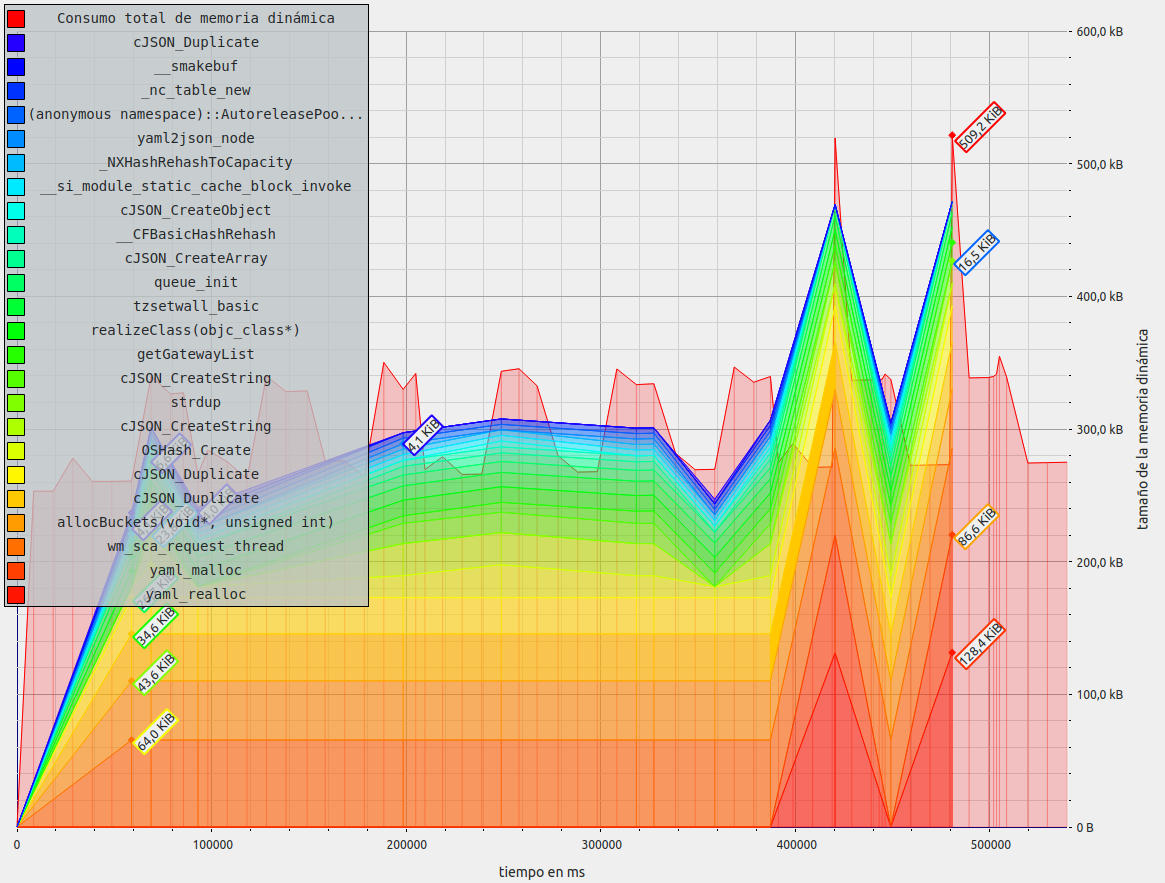

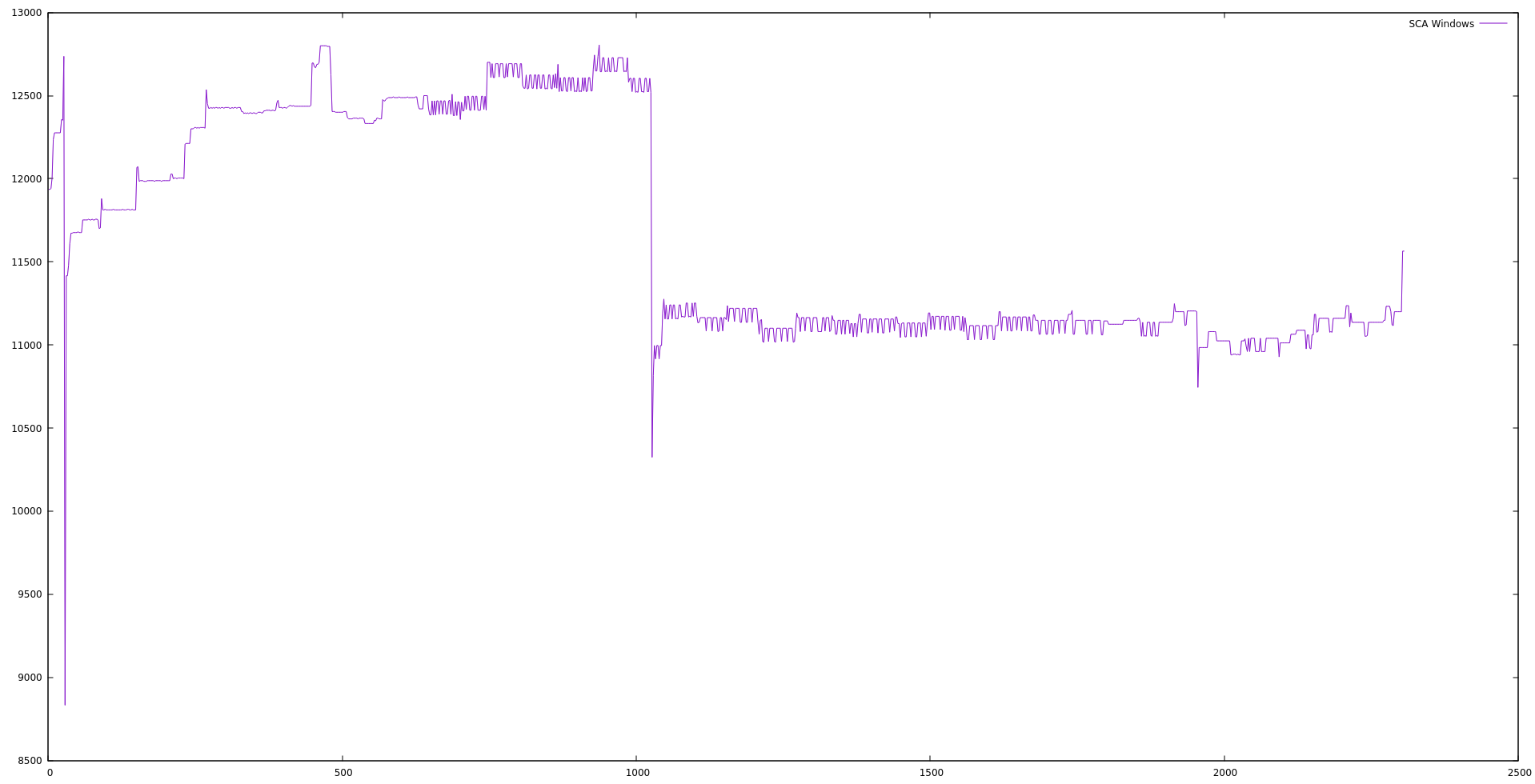

SCA Memory test
These tests assess that there are no memory leaks in the PR: wazuh/wazuh#3286
It also reflects the results of static code analyzers and tests of the memory and CPU use.
Functional tests
LINUX
.disabledorenable="no"at the configuration file.<policy>cis_debian9_L1.yml.disabled</policy>, for example. It should be enabled.<policy>cis_debian9_L1.yml.disabled</policy>.Check first scan results:
Check subsequent scans restults:
Check results when a policy is disabled:
Check the configuration on demand:
Integrity:
sca.request_db_intervalwhen the integrity check fails.Upgrade:
WINDOWS
.disabledorenable="no"at the configuration file.<policy>cis_debian9_L1.yml.disabled</policy>, for example. It should be enabled.<policy>cis_debian9_L1.yml.disabled</policy>.Check first scan results:
Check subsequent scans restults:
Check results when a policy is disabled:
Check the configuration on demand:
Integrity:
sca.request_db_intervalwhen the integrity check fails.Upgrade:
The text was updated successfully, but these errors were encountered: