-
Notifications
You must be signed in to change notification settings - Fork 2
Home
PowerAuth Command-Line Tool documentation has been moved to: https://developers.wultra.com/docs/develop/powerauth-cmd-tool/
Please use the new developer portal to access documentation.
This brief document serves as a documentation of the reference PowerAuth 2.0 Client - a simple utility connecting to the standard RESTful API. The utility simulates a mobile device on desktop - you can use it for simple integration testing.
You can download the latest powerauth-java-cmd.jar at the releases page:
Before you can run the utility from the command-line, you need to register Bouncy Castle JCE provider in your JRE.
Please follow our Bouncy Castle installation tutorial.
Note: You must create this file before you can use the utility. Obtain the information from the PowerAuth 2.0 Admin interface.
Client configuration file is required for the correct function of the command-line utility. It contains the same information that would be bundled inside a mobile app after download from the application marketplace. The file stores application key, application secret and master server public key in a following format:
{
"applicationName": "PowerAuth 2.0 Reference Client",
"applicationKey": "ivGlm/hl6rn9lSaD4qMgGw==",
"applicationSecret": "bI5pNbDdAXWUr/UQY5+Tpg==",
"masterPublicKey": "BO4+eqJPQTldjcV9G36dGiagsOHzgKgWz5uPuJKYwvIakbFmfWah1N4GXmBOS8aBEwQ+BcV04LL+OBBY0QS1bvg="
}You must obtain the values for this file from the PowerAuth 2.0 Admin interface:
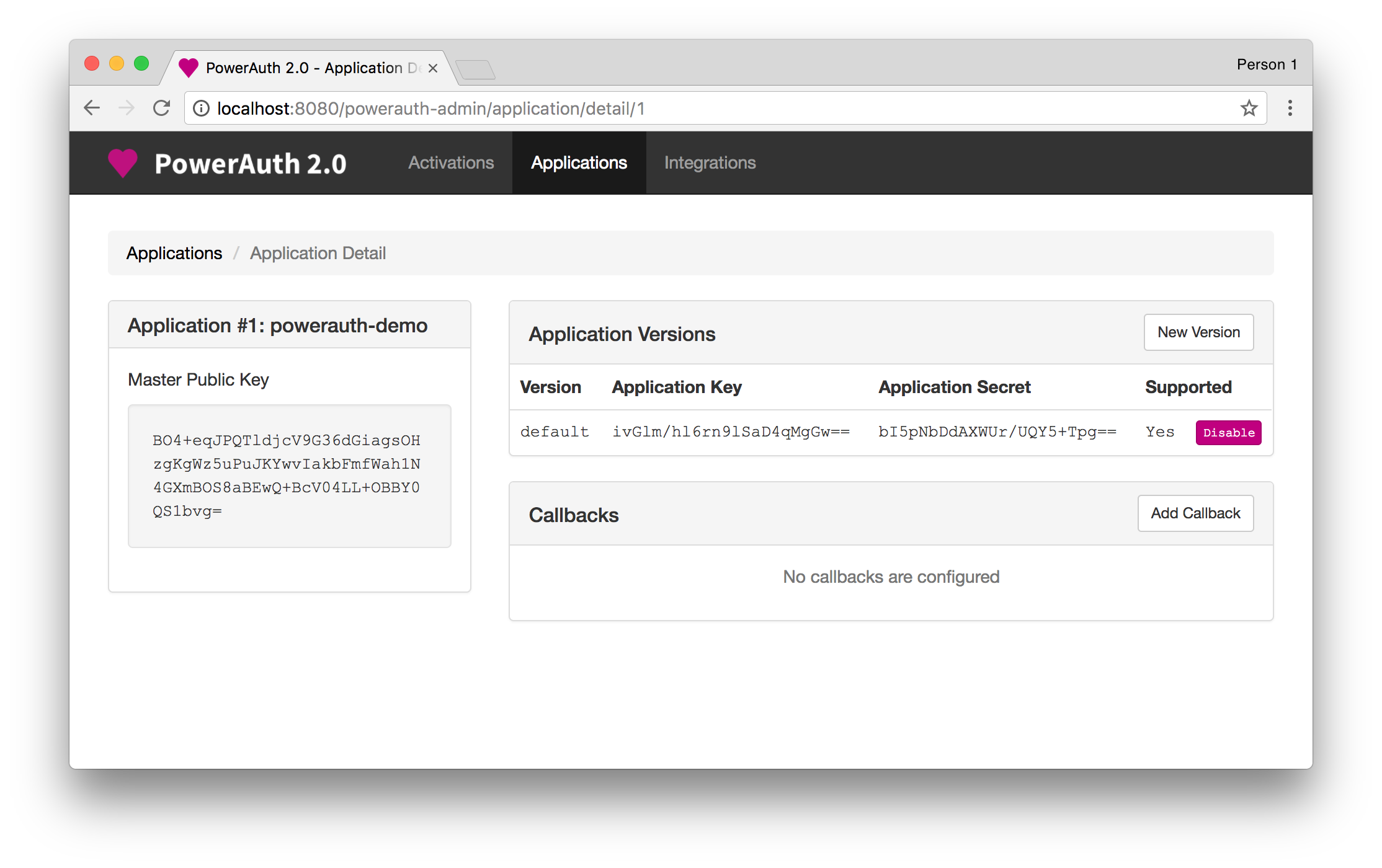
Note: You should not create this file yourself. The utility creates it for you.
This file is automatically created by the utility after you call the prepare method. It keeps the current PowerAuth 2.0 Client activation status information. In other words, client status file contains everything that a mobile application would store after it was paired with the user account.
{
"activationId" : "cebb3ae6-f774-4b74-8020-f7b4da64de8f",
"serverPublicKey" : "BKVanyqfLG2MxVwMt/LhmFliqPpHxVhtU3PEMG9FOIeJFkPAQjHpije029//S+bOprC4j6a8DMukxfoYkCFfLjU=",
"counter" : 10,
"encryptedDevicePrivateKey" : "HxRPkVVTM3QL+hecOY6cwQNvgNzvp2GbvvQ7cAOUXxzAk1dDaZVh1hd+2k18ZHn2",
"signatureBiometryKey" : "4Kb+7AO49ZHOpA4vtYzZGA==",
"signatureKnowledgeKeyEncrypted" : "i0LTZsWPlmRel0L7eg8U2w==",
"signatureKnowledgeKeySalt" : "J/LULF2V/fqE7Dw7AZhlmA==",
"signaturePossessionKey" : "jO89IxZs9bawvW3qlNQCzg==",
"transportMasterKey" : "kOh0lamazBJgDLSIcZ/ZJw=="
}Use this method to create a new activation using an activation code.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "prepare" \
--password "1234" \
--activation-code "F3CCT-FNOUS-GEVJF-O3HMV"Uses the prepare method to activate a PowerAuth 2.0 Reference client by calling the PowerAuth 2.0 Standard RESTful API endpoint /pa/activation/create hosted on root URL http://localhost:8080/powerauth-restful-server with an activation code F3CCT-FNOUS-GEVJF-O3HMV. Reads and stores the client status from the /tmp/pa_status.json file. Uses master public key and application identifiers stored in the /tmp/pamk.json file. Stores the knowledge related derived key using a given password 1234.
Note: If a --password option is not provided, this method requires interactive console input of the password, in order to encrypt the knowledge related signature key.
Use this method to obtain information about existing activation.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "status"Uses the status method to get the activation status for the activation ID stored in the status file /tmp/pa_status.json, by calling the PowerAuth 2.0 Standard RESTful API endpoint /pa/activation/status hosted on root URL http://localhost:8080/powerauth-restful-server. Uses the master public key and application identifiers stored in the /tmp/pamk.json file.
Use to remove the activation on the server.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "remove" \
--password "1234"Uses the remove method to remove activation with an activation ID stored in the status file /tmp/pa_status.json, by calling the PowerAuth 2.0 Standard RESTful API endpoint /pa/activation/remove hosted on root URL http://localhost:8080/powerauth-restful-server. Uses the master public key and application identifiers stored in the /tmp/pamk.json file. Unlocks the knowledge related signing key using 1234 as a password.
Note: If a --password option is not provided, this method requires interactive console input of the password, in order to unlock the knowledge related signature key.
Use this method to send signer GET or POST requests to given URL with provided data.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server/pa/signature/validate" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "sign" \
--http-method "POST" \
--endpoint "/pa/signature/validate" \
--signature-type "possession_knowledge" \
--data-file "/tmp/request.json" \
--password "1234"Uses the sign method to compute a signature for given data using an activation record associated with an activation ID stored in the status file /tmp/pa_status.json. Calls an authenticated endpoint http://localhost:8080/powerauth-restful-server/pa/signature/validate that is identified by an identifier /pa/signature/validate (by convention the same as the endpoint name after the main context). Uses the master public key and application identifiers stored in the /tmp/pamk.json file. Uses HTTP method POST, possession_knowledge signature type and takes the request data from a file /tmp/request.json. Unlocks the knowledge related signing key using 1234 as a password.
Note: If a --password option is not provided, this method requires interactive console input of the password, in order to unlock the knowledge related signature key.
In case you are validating signature on requests that require authenticated session, use --http-header option:
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server/pa/signature/validate" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "sign" \
--http-method "POST" \
--http-header Cookie="JSESSIONID=D0A047F9E8A9928386A5B34AB6343C30"
--endpoint "/pa/signature/validate" \
--signature-type "possession_knowledge" \
--data-file "/tmp/request.json" \
--password "1234"Use this method to test secure vault unlocking.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "unlock" \
--signature-type "possession_knowledge" \
--password "1234" \
--reason "NOT_SPECIFIED"Uses the unlock method to unlock the secure vault for an activation with activation ID stored in the status file /tmp/pa_status.json, by calling the PowerAuth 2.0 Standard RESTful API endpoint /pa/vault/unlock hosted on root URL http://localhost:8080/powerauth-restful-server. Uses the master public key and application identifiers stored in the /tmp/pamk.json file. Unlocks the knowledge related signing key using 1234 as a password. The reason why vault is being unlocked is NOT_SPECIFIED.
Note: If a --password option is not provided, this method requires interactive console input of the password, in order to unlock the knowledge related signature key.
Use this method to create an activation using the custom attributes.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server-spring/pa/activation/direct/create" \
--status-file "/tmp/pa_status.json" \
--config-file "/tmp/pamk.json" \
--method "create-custom" \
--identity-file "/tmp/identity.json" \
--custom-attributes-file "/tmp/custom-attributes.json" \
--password "1234"Uses the create-custom method to activate a PowerAuth 2.0 Reference client by calling a custom activation endpoint http://localhost:8080/powerauth-restful-server-spring/pa/activation/direct/create with identity attributes stored in /tmp/identity.json file and custom activation attributes stored in /tmp/custom-attributes.json file. Reads and stores the client status from the /tmp/pa_status.json file. Uses master public key and application identifiers stored in the /tmp/pamk.json file. Stores the knowledge related derived key using a given password 1234.
There is a required format of both identity.json and custom-attributes.json files. The custom-attributes.json file may be any JSON file representing an object (at least, the file must contain {} string). The identity.json file must be a simple JSON object with identity attributes stored as string key-value, for example:
{
"username": "johndoe01",
"password": "s3cR!7"
}Note: If a --password option is not provided, this method requires interactive console input of the password, in order to encrypt the knowledge related signature key.
Use this method to send encrypted data to the server.
java -jar powerauth-java-cmd.jar \
--url "http://localhost:8080/powerauth-restful-server-spring/exchange" \
--config-file "config.json" \
--method "encrypt" \
--data-file "request.json"Uses the encrypt method to encrypt data in request.json file using non-personalized end-to-end encryption.
The encrypted data is sent to specified endpoint URL. The endpoint which receives encrypted data needs to decrypt the data using PowerAuthNonPersonalizedEncryptor and return encrypted response back to the client. The cmd line tool receives the encrypted response from server, decrypts it and prints it into the command line.
PowerAuth 2.0 Reference Client is called as any Java application that is packaged as a JAR file and it uses following command-line arguments.
usage: java -jar powerauth-java-cmd.jar
-a,--activation-code <arg> In case a specified method is 'prepare', this field contains
the activation key (a concatenation of a short activation ID
and activation OTP).
-c,--config-file <arg> Specifies a path to the config file with Base64 encoded server
master public key, application ID and application secret.
-C,--custom-attributes-file <arg> In case a specified method is 'create-custom', this field
specifies the path to the file with custom attributes.
-d,--data-file <arg> In case a specified method is 'sign', this field specifies a
file with the input data to be signed and verified with the
server, as specified in PowerAuth signature process.
-e,--endpoint <arg> In case a specified method is 'sign', this field specifies a
URI identifier, as specified in PowerAuth signature process.
-h,--help Print this help manual.
-H,--http-header <key=value> Use provided HTTP header for communication
-I,--identity-file <arg> In case a specified method is 'create-custom', this field
specifies the path to the file with identity attributes.
-i,--invalidSsl Client may accept invalid SSL certificate in HTTPS
communication.
-l,--signature-type <arg> In case a specified method is 'sign', this field specifies a
signature type, as specified in PowerAuth signature process.
-m,--method <arg> What API method to call, available names are 'prepare',
'status', 'remove', 'sign', 'unlock' and 'create-custom'.
-p,--password <arg> Password used for a knowledge related key encryption. If not
specified, an interactive input is required.
-r,--reason <arg> Reason why vault is being unlocked.
-s,--status-file <arg> Path to the file with the activation status, serving as the
data persistence.
-t,--http-method <arg> In case a specified method is 'sign', this field specifies a
HTTP method, as specified in PowerAuth signature process.
-u,--url <arg> Base URL of the PowerAuth 2.0 Standard RESTful API.
Everything should be deployed correctly but utility cannot connect.
If you are using HTTPS, make sure you are using valid SSL certificate or that you use "-i" option.
All sources are licensed using Apache 2.0 license, you can use them with no restriction. If you are using PowerAuth 2.0, please let us know. We will be happy to share and promote your project.
If you need any assistance, do not hesitate to drop us a line at hello@wultra.com.