Home
This wiki summarizes macsec protocol usage with Multi-party protocol (MPP).
- EEE MACSec and NSA ESS: How to Protect Your WAN, LAN and Cloud (youtube)
- MACsec: a different solution to encrypt network traffic
After you understand why macsec is needed, deployed and used - you need to get keying right. Static macsec keys are by default easiest, but you might need some real security with periodically re-keyed macsec hosts. This is where our Multi-party Protocol (MPP) kicks in.
Standard way to dynamically key macsec hosts is MKA (based on IEEE 802.1X Extensible Authentication Protocol (EAP)). MKA is often offered by hardware ethernet switches and routers (by cisco, juniper and others). If you ever thought that IPSEC/IKEv1/IKEv2/EAP is complicated, try to figure MKA out.
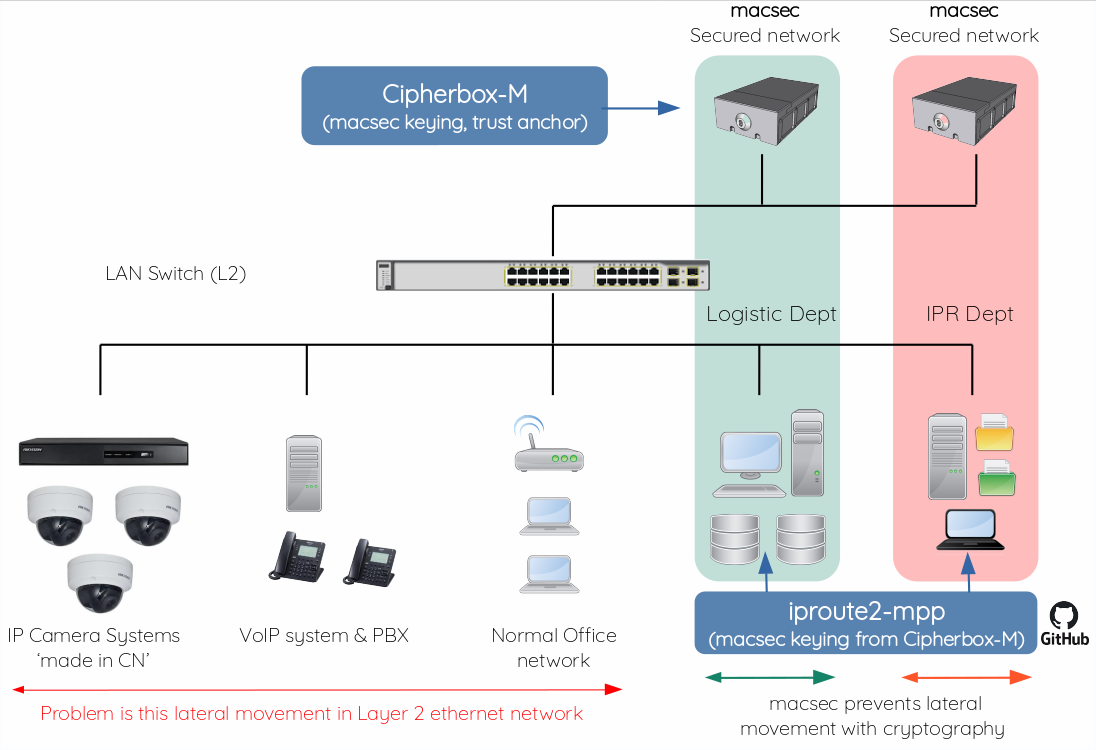
MPP is XXLSEC Ltd's proprietary multi-party protocol, which creates consensus between authorized entities in constellation. Our protocol delivers integrity, authentication, identification and confidentiality together with consensus of shared data set.
To put it simple, when you run protocol on hosts - they all become aware of 'payload data' from each others. Automatically.
When you think about macsec and available key exchange protocols, you end up in confusion. Mostly all currently deployed key agreement protocols are between two party and thereby create knowledge of keys (over insecure channel) between two parties.
Macsec demands consensus of keys, between everybody in macsec group. Each host has own key and other host key(s). This is where things turns complicated and where redhat left off with their excellent blog post. Nobody wants to talk about macsec keying and why's that?
If macsec hosts require consensus of keys, how does it looklike?
Take LAN network with 10 hosts, which you need to secure with MACSEC. Each host needs to have own 'TX' key and other hosts 'RX' keys. In 10 host network, you need to configure (by hand and following redhat excellent blog post) one key for 'TX' and nine other hosts key for 'RX' to each of 10 hosts on network.
It means that you need to setup 1 + 9 keys to each host. For 10 hosts it makes 90 keys to generate and to configure. By hand.
Try to calculate what it takes to secure 100 hosts LAN segment?
We call this cryptography logistics issue.
As we have our Multi-party Protocol (MPP), we decided to give it a try with macsec keying and it turned out to be pretty neat solution. This repository hosts MPP modified iproute2 as a reference design for macsec keying with our Multi-party Protocol.
We will illustrate full example here later on and define our MPP availability for commercial integration purposes as well. So check back later or contact us for immediate hands on demonstration how this all works now.
Securing hosts on LAN with macsec looks currently like this: