New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Security Fix for Cross-site Scripting (XSS) - huntr.dev #4543
Conversation
[FIX] Stored-XSS using `htmlentities()`
Add Middleware to clean user input from XSS
Middleware is at app/Http/Middleware/SanitizeInput.php and can be tunned for specific keys adding them to the $except array:
```
/**
* The names of the attributes that should not be trimmed.
*
* @var array
*/
protected $except = [
'password',
'password_confirmation',
'_token',
''
];
```
[FIX] Stored-XSS application-wide
|
Raj seems not to be a GitHub user. You need a GitHub account to be able to sign the CLA. If you have already a GitHub account, please add the email address used for this commit to your account. You have signed the CLA already but the status is still pending? Let us recheck it. |
|
@alromh87 - are you able to sign the CLA? Let me know if you have any questions! 🍰 |
|
Sure 😉 |
|
Hi @huntr-helper @JamieSlome @alromh87 Anyway, if you want to consider it, please remove the first changes done in the commit 3871537, because it has been superseeded by another fix here. |
|
I will update tomorrow, I found in many places protection was disabled due to using {!! $log['description'] !!} |
|
@asbiin Updated as per requested and updated with upstream, use of htmlentities was removed when presenting information, only middleware for sanitizing before storage is preserved. |
|
@alromh87 any update on that fix? Current changes still uses |
|
This PR has been on hold for a long time. |
|
This pull request has been automatically locked since there |
https://huntr.dev/users/alromh87 has fixed the Cross-site Scripting (XSS) vulnerability 🔨. alromh87 has been awarded $25 for fixing the vulnerability through the huntr bug bounty program 💵. Think you could fix a vulnerability like this?
Get involved at https://huntr.dev/
Q | A
Version Affected | ALL
Bug Fix | YES
Original Pull Request | 418sec#2
Vulnerability README | https://github.com/418sec/huntr/blob/master/bounties/other/monica/2/README.md
User Comments:
Metadata *
Bounty URL: https://www.huntr.dev/bounties/2-other-monica
⚙️ Description *
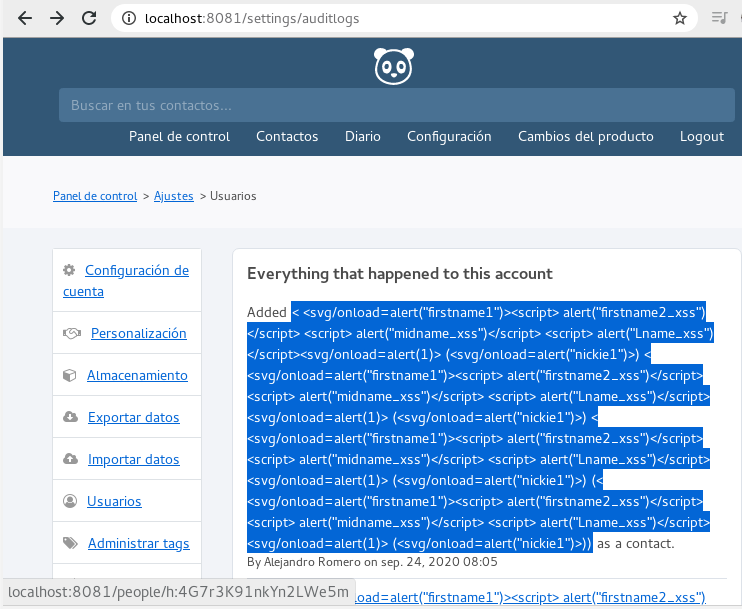
XSS queries being triggered from people info page by the audit log at the settings, fix sanitizes content before showing to user.
Technical Description *
Even tough Laravel has inbuilt protection for XSS it has been disabled when presenting log:
{!! $log['description'] !!}to enable embeding contact links, leading to XSS, htmlentities was used to sanitize data before showing to user, efectively avoiding new as well as already stored XSS.Edit
Looking further into the code I realized the XSS protection have been disabled in many views so I added a Middleware that will strip html tags using
strip_tags, and sincestrip_tagscan be tricked with malformed markup reamaning input is encoded using htmlentities.Middleware is at app/Http/Middleware/SanitizeInput.php and can be tunned for specific keys adding them to the
$exceptarray:Proof of Concept (PoC) *
< <svg/onload=alert("firstname1")><script> alert("firstname2_xss")</script> <script> alert("midname_xss")</script> <script> alert("Lname_xss")</script><svg/onload=alert(1)> (<svg/onload=alert("nickie1")>)Proof of Fix (PoF) *
After fix introduced data is displayed as text and no XSS is executed
Stored XSS will be also stripped out and encoded after contact is edited
User Acceptance Testing (UAT)
Functionallity is unafected, contact link works as usual