Create a workflow that uses GitHub Actions OIDC provider for authentication against Azure
GitHub Actions workflows often need to access a cloud provider like AWS, Azure, GCP, ... for example for resource creation or for software deployment. Therefore usually long living secrets are used and stored as secrets in GitHub. GitHub Actions OpenID Connect (OIDC) provider allows you to configure your workflow to request a short-lived access token directly from the cloud provider. By updating your workflows to use OIDC tokens, you can adopt good security practices like no cloud secrets, authentication and authorization management as well as rotating credentials.
- Who is this for: Developers and DevOps engineers
- What you'll learn: Best practice authentication for workflows against Azure
- What you'll build: A workflow that uses GitHub Actions OIDC provider for authentication against Azure
- Prerequisites: Azure tenant with a subscription
- How long: This course is 2 steps long and takes less than 15 minutes to complete.
- Above these instructions, click Use this template, right-click Create a new repository and click Open link in new tab.
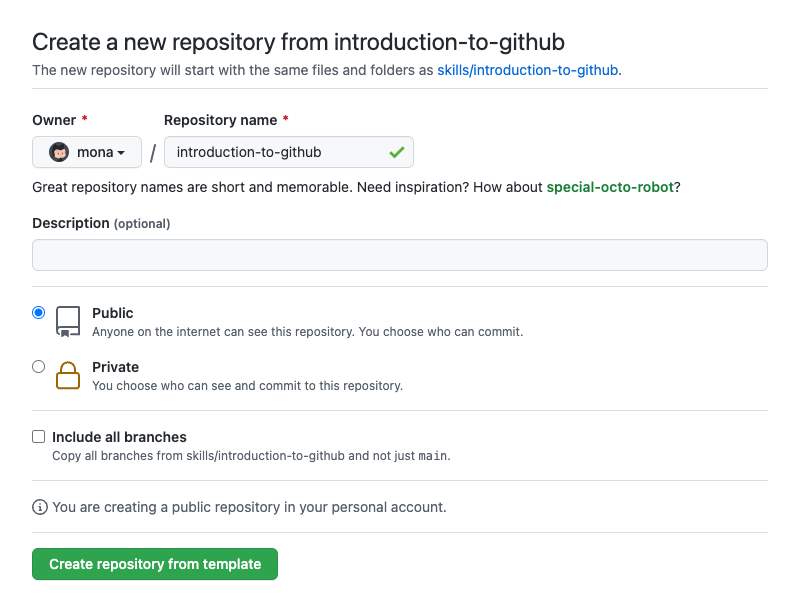
- In the new tab, follow the prompts to create a new repository.
- For owner, choose your personal account or an organization to host the repository.
- I recommend creating a public repository as private repositories will use Actions minutes.
- After your new repository is created, wait about 20 seconds, then refresh the page. Follow the step-by-step instructions in the new repository's README.
Welcome to "GitHub Actions workflow with OIDC based authentication against Azure"! 👋
In this step you'll configure OIDC in your Azure tenant.
What is Azure: Azure is the cloud platform of Microsoft.
What is a tenant: A Microsoft Entra ID tenant is a reserved Microsoft Entra ID service instance that an organization receives and owns once it signs up for a Microsoft cloud service such as Azure, Microsoft Intune, or Microsoft 365.
What is OIDC: OpenID Connect or OIDC is an identity protocol that utilizes the authorization and authentication mechanisms of OAuth 2.0.
What is a branch?: A branch is a parallel version of your repository. By default, your repository has one branch named main and it is considered to be the definitive branch. You can create additional branches off of main in your repository. You can use branches to have different versions of a project at one time.
- Open a new browser tab, and work on the steps in your second tab while you read the instructions in this tab
- Create an Azure Active Directory application and service principal by following the steps under the link
- Assign role
Contributorwith scope subscription (on subscription level) to the application (for a detailed step-by-step manual, see here)
- Assign role
- Add federated credentials by following the steps under the link
Entity type:Branch- GitHub branch name:
deploy-resource-group
- Create GitHub secrets by following the steps under the link
- If you are done, create a new branch with name
deploy-resource-group - Wait about 20 seconds then refresh this page for the next step
You did configure OIDC in Azure and created a branch! 🎉
Configuring OIDC in Azure allows you to authenticate in a GitHub Actions workflow without the need of storing an access token in GitHub!
What is a workflow: A workflow is a configurable automated process that will run one or more jobs. Workflows are defined by a YAML file checked in to your repository and will run when triggered by an event in your repository, or they can be triggered manually, or at a defined schedule.
The following steps will guide you through the process of creating a GitHub Actions workflow.
- On the Code tab, make sure you're on your new branch
deploy-resource-group - Click on tab
Settings - In section
Default branchswitch the default branch todeploy-resource-group(click on button <--> to switch default branch) - Click on tab
Actions - Click on button
new workflow - Choose
Simple workflowand clickConfigure - Rename file to
my-first-workflow.yml - Replace content of
.ymlfile with the following content
name: Run Azure Login with OpenID Connect and PowerShell
on: [push]
permissions:
id-token: write
contents: read
jobs:
Windows-latest:
runs-on: windows-latest
steps:
- name: OIDC Login to Azure Public Cloud with AzPowershell (enableAzPSSession true)
uses: azure/login@v1
with:
client-id: ${{ secrets.AZURE_CLIENT_ID }}
tenant-id: ${{ secrets.AZURE_TENANT_ID }}
subscription-id: ${{ secrets.AZURE_SUBSCRIPTION_ID }}
enable-AzPSSession: true
- name: 'Create resource group with PowerShell action'
uses: azure/powershell@v1
with:
inlineScript: |
New-AzResourceGroup -Name MyFirstResourceGroup -Location "South Central US"
azPSVersion: "latest"- Click
Commit changes...button - Wait until the GitHub Actions workflow finished and then refresh this page for the next step
Congratulations friend, you've completed this course!

Here's a recap of all the tasks you've accomplished in this course:
- You configured OIDC in Azure by adding the Federated Credentials to Azure
- You created your first GitHub Actions workflow that uses GitHub Actions OIDC provider for authentication against Azure
- The execution of this workflow create a resource group in your Azure tenant by using best practice authentication
- I'd love to hear what you thought of this course
- Check out using environments for deployment
- Check out reusable workflows
- Check out Assigning permissions to jobs
- To find projects to contribute to, check out GitHub Explore
Get help: About security hardening with OpenID Connect • Review the GitHub status page
© 2024 Marc Rufer • Code of Conduct • License