The Gordian Seed Tool reference app allows for the storage of cryptographic seeds and their backup, transfer, and usage. It acts as a cosigner, seed generator, and seed vault.
This Case Study should not be taken as a review, as it covers one of Blockchain Commons' own apps. Rather, it's intended as a pure Case Study, demonstrating how Blockchain Commons feels that this app meets the goals of the Gordian architecture and thus how it can act as a reference for the design.
Gordian Seed Tool is an iOS app that can also be run on MacOS devices. It stores seeds and also allows the transfer of those seeds via a variety of specifications, the backup of seeds via SSKR and other methods, and the usage of seeds to sign PSBTs. Gordian Seed Tool's prime means of interacting with other devices is through airgapped QRs, though it can also transfer text via a variety of means.
- App Store: https://apps.apple.com/us/app/gordian-seed-tool/id1545088229
- Repo: https://github.com/BlockchainCommons/GordianSeedTool-iOS
- Manual: https://github.com/BlockchainCommons/GordianSeedTool-iOS/blob/master/Docs/MANUAL.md
Seed Tool does not create transactions nor send them to the network. It is a seed storage and offline signing app.
The Gordian Seed Tool stores seeds, optimally on an airgapped mobile device, and then allows their usage.
There are generally three ways to put seeds into Seed Tool:
- Create a seed with using Apple's cryptographic APIs for randomness.
- Create a seed on Seed Tool using dice, cards, or coin flips.
- Import a seed generated by another device or source of randomness.
There are a number of ways that seed can then be used:
- Export the seed to another location.
- Export a key to another location.
- Respond to a request for a variety of key formats, including private and public keys, hd-keys, and addresses.
- Respond to a request to sign a Bitcoin PSBT.
The Gordian architecture generally depends on airgaps for security, so the following airgapped usage most closely meets that design:
- Add a seed to Seed Tool via any means.
- Backup Your seed with SSKR. Separate the shares.
- Export a watch-only pubkey to a transaction coordinator via QR code.
- Alternatively, export a pubkey as one of the keys in a multisig account.
- Import PSBTs from the transaction coordinator using
ur:crypto-requestencoded as a QR. - Export Signed PSBTs to the transaction coordinator using
ur:crypto-responseencoded as a QR.
Note that this case study uses the term "transaction coordinator" to refer to the desktop or mobile software that watches over the account associated with a key on Seed Tool and creates and transmits transactions. These apps have more commonly been called "software wallets", but when used with a seed vault such as Seed Tool, the software app holds no private keys, and so the term "wallet" is not entirely correct. For that reason, and to avoid overload of the term, the more practical "transaction coordinator" is used. See Gordian Architecture Roles for more.
Gordian Seed Tool was designed as a reference for all four of the Gordian Principles.
Gordian Seed Tool maximizes Independence by allowing users to make all the choices about what they do with their seeds.
Pros:
- Seed Tool gives total control over all assets, with the seeds residing within Seed Tool.
- Seed Tool ensures that users have total choice over what transaction coordinator or other devices they use with Seed Tool.
Neutral:
- Total independence means total responsibility: users must independently backup their data, make good choices about transaction coordinators, and consider the use of resilient multisig designs.
The use of Gordian Seed Tool keeps all private data close.
Pros:
- As a closely held device, Seed Tool maximizes the privacy possibilities for private keys.
- When run on an unnetworked mobile device (iPhone or iPod Touch), the privacy of Seed Tool is near total; this decreases if Seed Tool is used on a networked mobile device (iPhone or iPod Touch with wifi or cellular connection) and may not meet privacy needs if it's run on a networked computer (desktop or laptop MacOS).
Neutral:
- Again, the user bears responsibility for what happens when information is transferred out of Seed Tool: they must decide which transaction coordinators (or architectural designs) will optimize privacy.
Minimizing Single Point of Compromise (SPOC) protects data from theft: with Seed Tool, Apple's internal security provides this protection.
Pros:
- Seed Tool stores all at-rest data in encrypted form using Apple's APIs.
- Access to Seed Tool is by default protected by 2FA: one factor is checked when you log into your Apple account on first usage and another when you verify your access each time you look at data, usually using a biometric code. (This can be turned off if Seed Tool is to be used in offline mode.)
- Seeds backed up to iCloud are encrypted, with the encryption key stored in your iCloud keychain, which is escrowed, so that not even Apple can read it.
- Seed Tool remains functional even if network access is completely turned off, creating the option of a cold-storage device.
- Seed Tool offers full support for cosigner keys, allowing its seeds to be used to create multisigs, which can offset any SPOC "Con"s.
Neutral:
- Trust in Seed Tool ultimately rests on trust in Apple. The question of whether this is a pro or con may vary for different users; Blockchain Commons feels that Apple invests money to protect the privacy of their products and the ecosystem, and that we are thus able to leverage their best practices.
Cons:
- Some backup and sharing mechanisms have the possibility to be SPOCs if used. An individual user must decide between ease-of-use (Convenience) and resilience based on the individual risks of their own setup. Notably:
- The network-printing option could make network access into a SPOC.
- Cut-and-paste sharing options could allow other apps to access the secure data on the Universal Clipboard.
- There has not yet been a security review of Seed Tool, though such a review is on the Blockchain Commons roadmap.
Minimizing Single Point of Failure (SPOF) protects data from loss: with Seed Tool, this is automated via iCloud and also available via other means.
Pros:
- Data is all backed up to iCloud, unless turned off by the user, and thus can be recovered by all devices logged into that account.
- Users are given the capability to back up data in a variety of other ways, including printing SSKR shares, but they must decide to do so.
- Data can all be exported as URs, which are self-describing and self-verifying, and thus unlikely to succumb to Bitrot in the future. Again, users must choose to do this export.
Neutral:
- Users can use seeds (and their keys) in any way that they want. If they use them to form multisigs, they will have additional protection from SPOF, but this is ultimately a decision that is up to the user.
Cons:
- iCloud backups can be lost if all physical devices (and/or logins to those devices) are lost and Apple account information is lost or if Apple deletes or locks down your account.
Seed Tool is the reference app for UR specifications, and so offers extensive interoperability.
Pros:
- Data can be imported via a variety of means, including URs.
- Data can be exported via a variety of means, including URs.
- The source code is open source and commits are verified.
- Seed Tool is licensed to protect against patent claims, and Blockchain Commons is also a member of COPA.
Seed Tool offers specific defenses against the following #Smartcustody adversaries.
Bitrot occurs when a software program or hardware device becomes outdated. There is some opportunity for Bitrot in Seed Tool, if the software is not updated and it no longer becomes possible to run it on newer devices. This is somewhat offset by the software being fully open source and moreso by Seed Tool offering the opportunity for users to back up their data in a variety of ways. By using URs as an option for these backups, Seed Tool also allows for self-describing data, which means that their purpose won't be forgotten in the future. Finally, Blockchain Commons also offers a command line version of the app, which is likely to outlast the Apple version.
With a touchscreen and a full graphical interface, Seed Tool offers a lot of convenience. This can itself be an adversary, because it means that users might not be using a fully airgapped device and are definitely using a device with a larger attack service than something that's exclusively a wallet. However, this level of convenience is meant to ward off users choosing something even more convenient (and less secure) such as keeping their seeds on a networked computer or at a centralized exchange.
Gordian Seed Tool is well-protected, even from institutional theft at Apple, provided that the data is actually protected as described in Apple APIs and tech sheets.
The backup to iCloud provides strong protection against key fragility, one of the largest dangers for personal cryptocurrency loss. The user can also proactively back up their seeds in a variety of different ways, with URs containing checksums that additionally protect against error or fragility.
If Seed Tool is entirely airgapped by using an unnetworked mobile device, this largely eliminates the possibility of network attack. If Seed Tool is run on a networked mobile device, the possibility of network attack still remains very low, due to the strong protections of the iPhone. Network attack could be a real possibility if Seed Tool is run on a networked computer, though the encryption of data still offers strong protection.
Seed Tool protects against physical theft with its 2FA, especially for any newer devices that uses biometrics as one of the factors (provided that they remain turned on). Again, the MacOS version of Seed Tool may be less secure, especially for older Macs without trusted hardware.
Seed Tool offers random seed generation. But, if users feel uncomfortable with that and the resultant possibility of Systemic Key Compromise if an error were to be found in the algorithm, they can instead generate seeds with dice, cards, or coin flips. Coins and dice can be checked against Ian Coleman's Mnemonic Code Converter, in off-line mode of course. They and cards can alternatively be checked against LetheKit or seedtool-cli.
Because Seed Tool is primarily a seed vault, it doesn't address the following adversaries, which are more likely to be found on the transaction-coordinator side of the equation: Censorship, Correlation, Transaction Error, User Error.
Seed Tool also doesn't currently resolve the following adversaries of note: Blackmail, Coercion, Death/Incapacitation, Social Engineering, Supply-Chain Attack.
Seed Tool maximizes the ways that a user can get data into the app:
- Data can be imported from files, images, photos, or the Universal Clipboard.
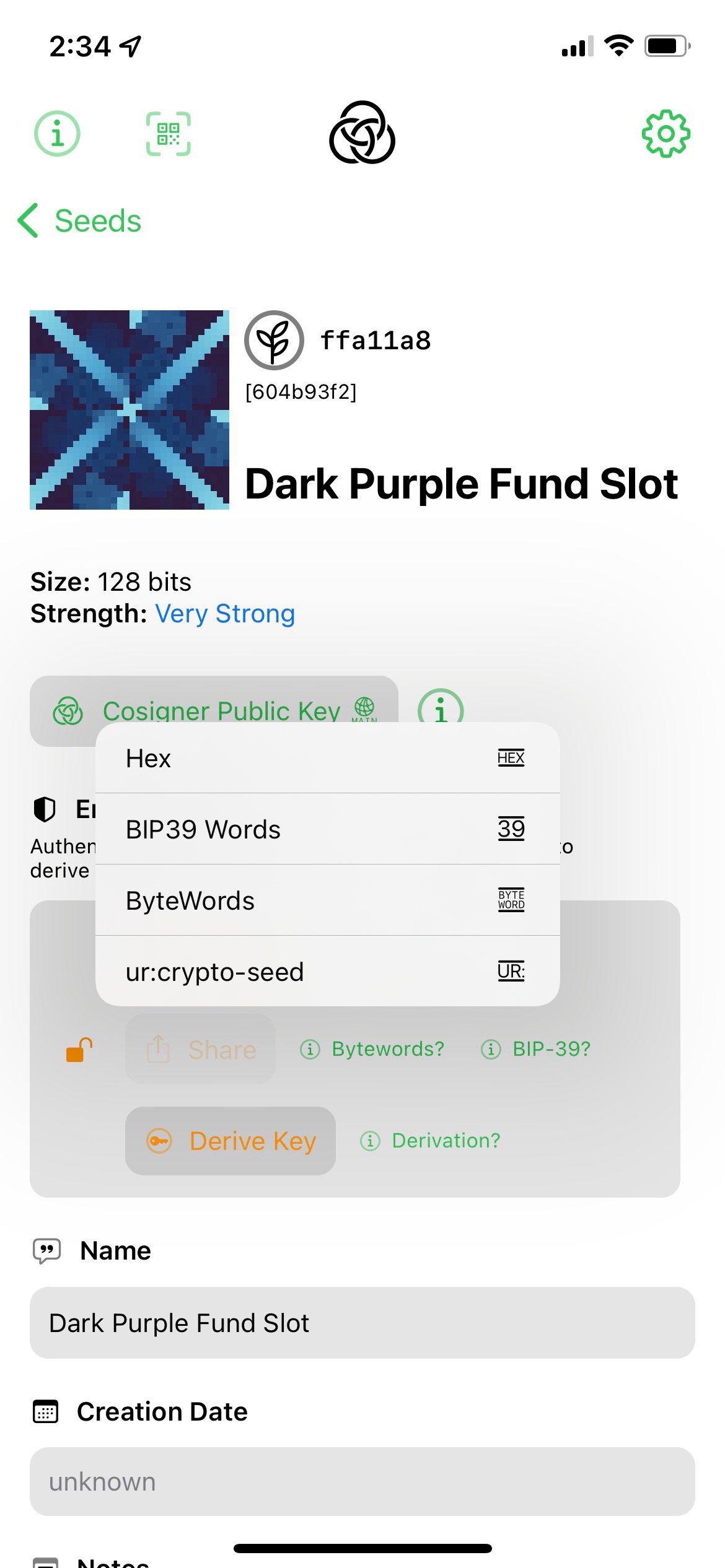
Seed Tool supports extensive input and output of URs, using either QRs, textual URs, or in some cases ByteWords.
- Seeds can be imported as
ur:crypto-seed. - Backups can be restored as
ur:crypto-sskr, provided that sufficient shares are available. - Seeds can be output as
ur:crypto-seed. - Seeds can be backed up as
ur:crypto-sskrshares. - Accounts can be exported as
ur:crypto-account. - Pubkeys can be exported as
ur:crypto-hdkey. - Private keys can be exported as
ur:crypto-hdkey. - Specific keys can be exported using
ur:crypto-responsein response to aur:crypto-requestfor a derivation. - PSBTs can be signed as a
ur:crypto-responsein response to aur:crypto-requestof an unsigned or partially signed PSBT.
Blockchain Commons considers URs the gold standard for interoperability because they are standardized, self-describing, and self-verifying.
Seed Tool also supports other popular data transfer methods for cryptocurrency, ensuring compatibility with legacy systems:
- Seeds can be imported as BIP-39 words or hex bytes.
- Seeds can be exported as BIP-39 words or hex bytes.
- Master keys can be exported as output descriptors.
- Addresses can be exported.
Gordian Seed Tool runs on any modern MacOS or iOS device. iOS is by far the preferred platform due to the security advantages of having a closely held device with a more limited attack surface.
The full source code for Gordian Seed Tool is available through Git Hub. It is programmed in Swift.
Gordian Seed Tool is a reference implementation meant to demonstrate the Gordian Principles and the Gordian Architecture. Though we believe the level of security and resilience built into Apple's hardware and software is strong, we also suspect that a dedicated hardware solution would be stronger, both because it would be built with security as a prime goal and because it would have a smaller attack surface.
Independence comes from user choice, privacy from user control, and resilience from seeds being automatically backed up (with additional options for sharing). Openness is demonstrated by creating the maximium interoperability reasonable, covering three different generations of interoperable specifications. We generally classify them as follows, in order of decreasing desirability:
ur:crypto-requestandur:crypto-response, which create the ability for high-level converations.ur:crypto-seed,ur-crypto-hdkey, and other URs, which create resilience through self-describing and self-verifying data.- BIP-39 and other older standards, which enable minimal interoperability, but which are widely recognized.
Although many second-generation hardware wallets such as Keystone and Passport are now using airgapped architectures with some interoperability, we believe they could still be improved by more focus on URs, especially the request/response cycle.
Seed Tool is intended largely as a reference and example of the feature set that future dedicated hardware wallets might want to consider; though no example is perfect, it offers concrete demonstrations of many of Blockchain Commons' best practices for architectural and interoperable design.
Gordian Seed Tool is an app produced by Blockchain Commons. Though it is freely compilable from source, it also available for sale through the Apple App Store. Caveat reader.