Introduction • Attacks • Features • Installation • Requirements
This project started over 2021 as a personal tool to easily audit networks without writing long commands or setting all values one by one, in order to automate the whole processes. This is not a professional tool, this project was created to learn about wireless security and for testing purposes. This is a fully offensive framework to audit wifi networks with different types of attacks for WPA/WPA2, WPS and WEP, automated handshake cracking and much more.
If you find an error, please open an issue (you can write it in english or spanish, as you want). If you have any doubt contact me via Discord, my username is d3ext
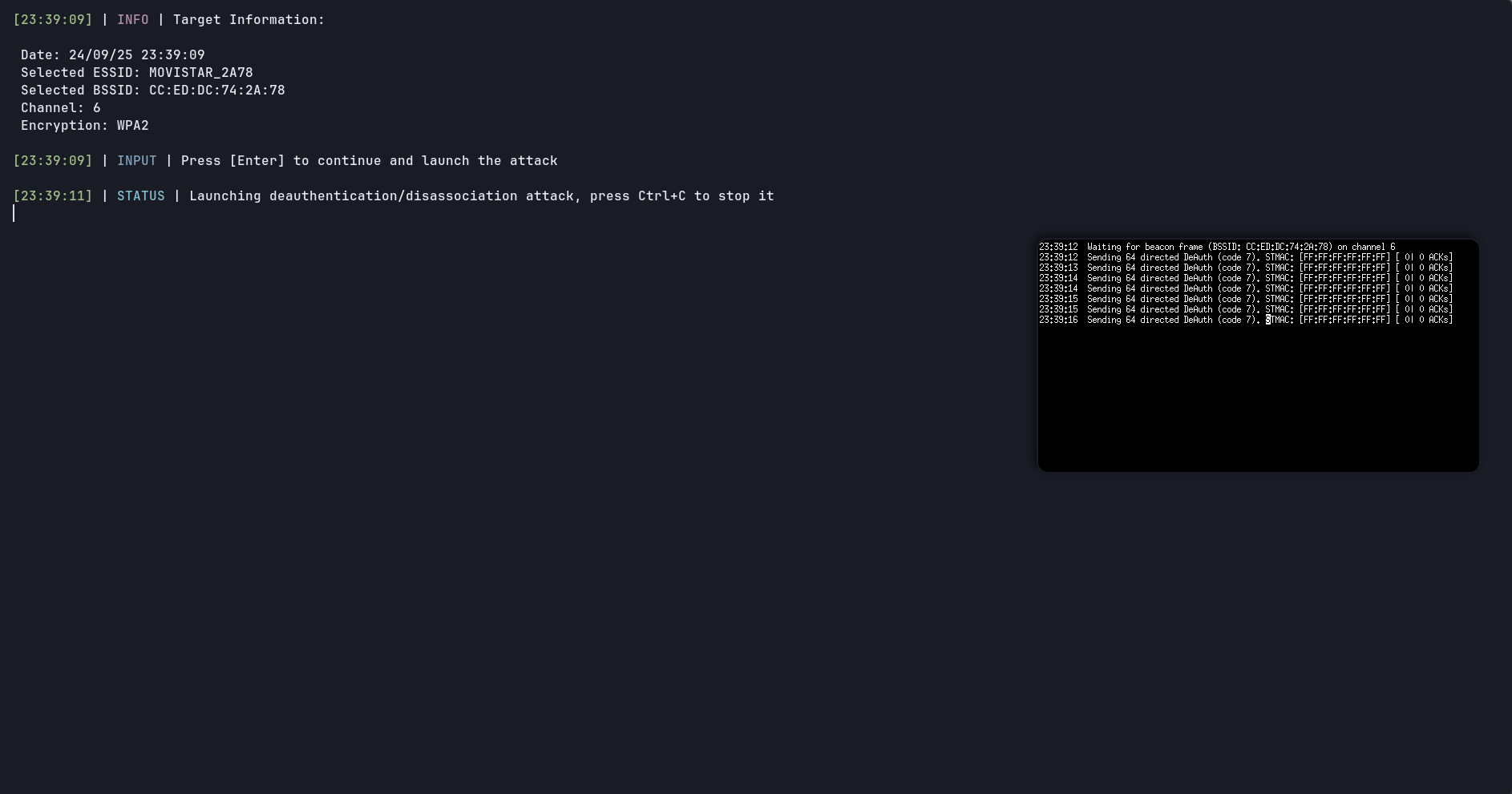
- Deauthentication attack
- WIDS Confusion attack
- Authentication attack
- Beacon Flood attack
- TKIP attack (Michael Shutdown Exploitation)
- Pixie Dust attack
- Null Pin attack
- PIN Bruteforce attack
- ARP Replay attack
- HIRTE attack
- Caffe Latte attack
- Fake Authentication attack
- WPA/WPA2 handshake capture attack (passively)
- PMKID attack
- Evil Twin attack
This attacks are explained here on the Wiki
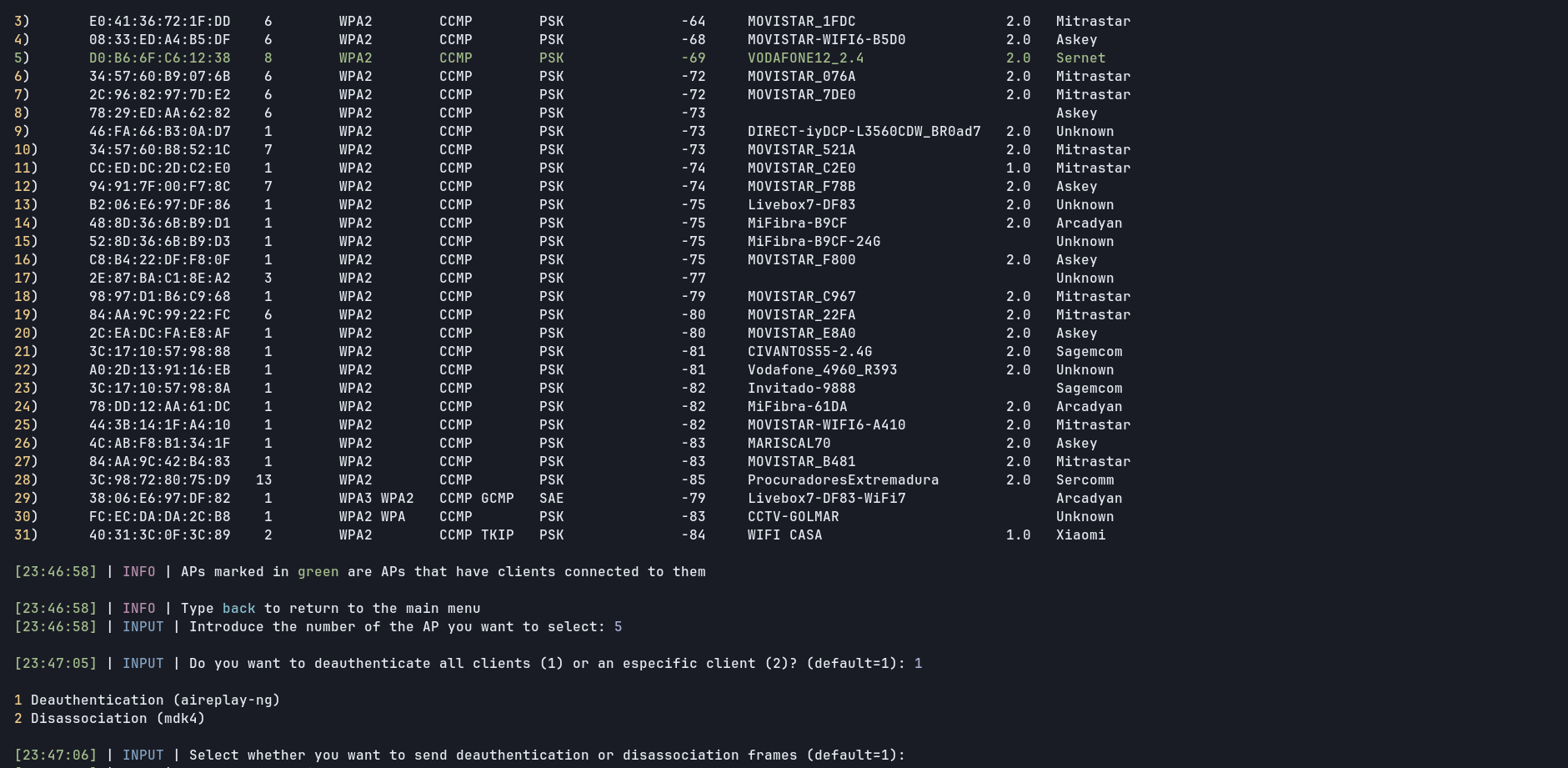
☑️ WPA/WPA2, WPS and WEP Attacks
☑️ Automatic handshake capture and cracking
☑️ Multiple templates for EvilTwin attack (different languages)
☑️ Enable/disable monitor mode and view interface info (frequencies, chipset, MAC...)
☑️ 2.4 GHz and 5 GHz supported
☑️ Informative attack logs (just done user side)
☑️ Custom wordlist selector when cracking handshakes
☑️ English and spanish supported
And much more
As root
git clone https://github.com/D3Ext/WEF
cd WEF
bash wefTake a look at the Wiki where I have more info about the installation
Simply execute this:
rm -rf /usr/share/wef \
/usr/bin/wefCommon usage of the framework
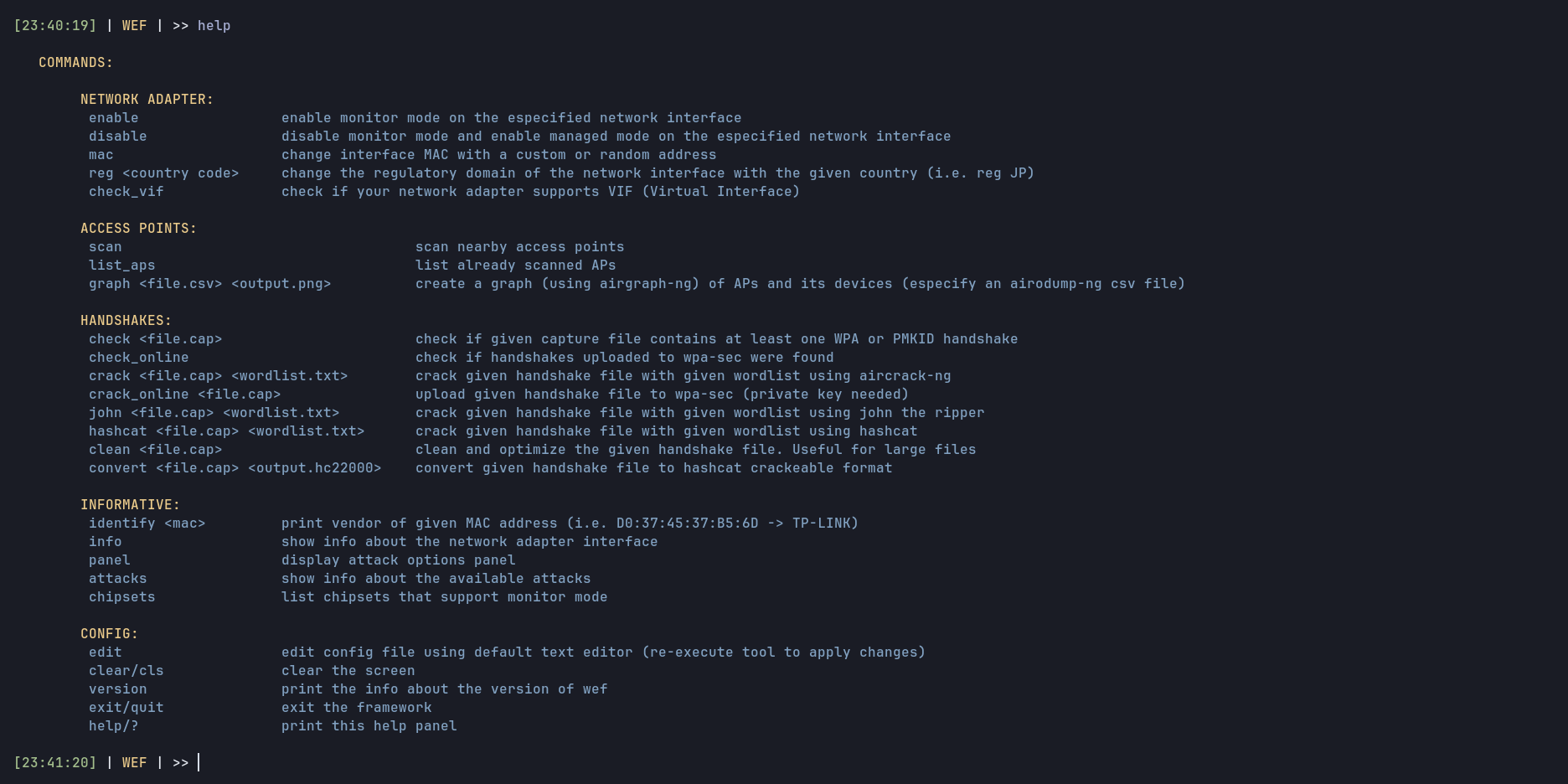
wef -i wlan0 # Your interface name might be differentHelp panel
__ _____ ___
\ \ / / __| __|
\ \/\/ /| _|| _|
\_/\_/ |___|_|
[WEF] WiFi Exploitation Framework 1.4
[*] Interfaces:
wlan0
ens33
Required parameters:
-i, --interface) The name of your network adapter interface in managed mode
Optional parameters:
-h, --help) Show this help panel
--version) Print the version and exit
See here for more information about how to use the tool and other related topics
Pwnagotchi mode- Add vendor logo to EvilTwin templates on the fly
- Test compatibility with others OS
KARMA attack- In-depth testing of implemented features
More general improvementMore languages added to Evil Twin templates
See CONTRIBUTING.md
See CHANGELOG.md
Thanks to ultrazar and ErKbModifier, they helped me a lot <3
https://github.com/aircrack-ng/aircrack-ng
https://github.com/aircrack-ng/mdk4
https://github.com/v1s1t0r1sh3r3/airgeddon
https://github.com/FluxionNetwork/fluxion
https://github.com/P0cL4bs/wifipumpkin3
https://github.com/s0lst1c3/eaphammer
https://github.com/derv82/wifite2
https://github.com/wifiphisher/wifiphisher
https://github.com/ZerBea/hcxtools
https://github.com/ZerBea/hcxdumptool
https://github.com/Tylous/SniffAir
https://github.com/evilsocket/pwnagotchi
https://github.com/koutto/pi-pwnbox-rogueap
https://github.com/koutto/pi-pwnbox-rogueap/wiki/01.-WiFi-Basics
Creator has no responsibility for any kind of:
- Illegal use of the project.
- Law infringement by third parties and users.
- Malicious act, capable of causing damage to third parties, promoted by the user through this software.
This project is under MIT license
Copyright © 2024, D3Ext