-
-
Notifications
You must be signed in to change notification settings - Fork 433
Traffic inspection
Now that we've discussed how to use Sniffnet to analyze your network at a high level, let's talk about how you can use it to inspect each of your connections more in depth.
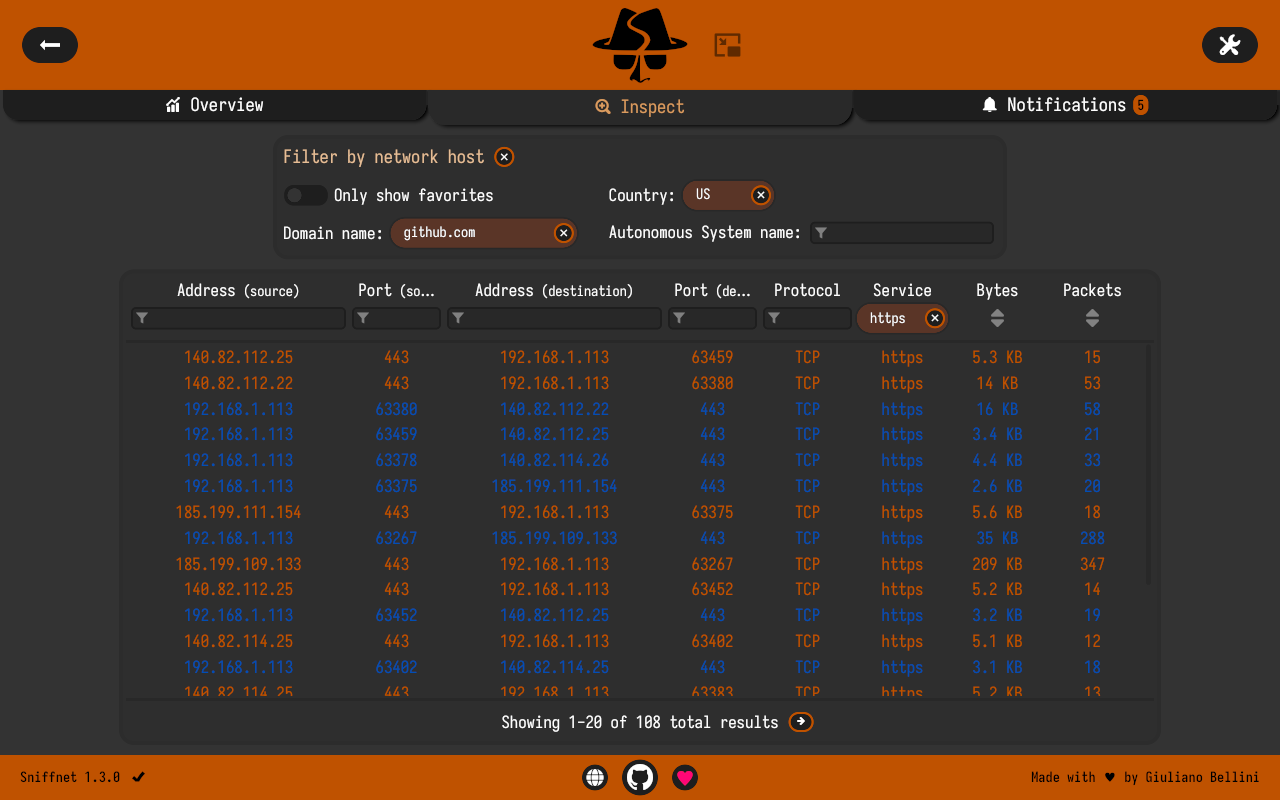
The Inspect page of the app allows you to gain more fine-grained insights about the network traffic you're monitoring.
Before diving into the functionalities of this page,
it's important to understand that the information reported here is relative to each network connection.
A network connection consists of a pair of hosts exchanging data, and it's characterized by the following attributes:
- source IP address: the IP address of the host sending data
- source port: the port number used by the source host
- destination IP address: the IP address of the host receiving data
- destination port: the port number used by the destination host
- protocol: the network protocol used for communication
These fields are better known as the 5-tuple of a connection, and they uniquely identify each network flow.
Keeping this in mind, we can now examine the features of the Inspect page.
The upper portion of the page includes a set of filters to limit the connections displayed in the table below, based on the attributes of the remote network host involved in the communication.

You should be familiar with the fields of this section, as they were previously discussed in the Network hosts Wiki page.
Tip
You can decide to populate these filters manually, but you can quickly do that also by clicking on the host you are interested in from the Overview page.
This way, the filters will be automatically filled with the details of the selected host.
The table right below shows a list of all the network connections observed during the monitoring session.

The table header not only includes the respective column names, but also provides:
- filtering capabilities for each column of interest
- sorting functionalities concerning the number of bytes and packets exchanged by each connection
Tip
All the available filters search for partial matches of the inserted values.
In case you want to only filter exact matches, you can prepend an equal character (=) to the search string.
By clicking on each of the table rows, you can obtain more details about the specific connection.
Additional information is displayed in a modal popup, and includes:
- timestamps of the first and last packet exchanged
- source and destination MAC addresses
- fully qualified domain name of the remote host
- ASN identifier of the remote host
- ICMP message types, in case of ICMP connections
