-
Notifications
You must be signed in to change notification settings - Fork 1
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
VerbsToken.tokenURI() is vulnerable to JSON injection attacks
#167
Comments
Descriptor contract is vulnerable to JSON injection attacksVerbsToken.tokenURI() is vulnerable to JSON injection attacks
|
raymondfam marked the issue as sufficient quality report |
|
raymondfam marked the issue as duplicate of #53 |
|
raymondfam marked the issue as not a duplicate |
|
raymondfam marked the issue as primary issue |
|
raymondfam marked the issue as high quality report |
|
rocketman-21 (sponsor) confirmed |
|
Looks like a |
|
MarioPoneder marked the issue as satisfactory |
|
MarioPoneder marked the issue as selected for report |
|
I think its invalid issue, because:
"doesn't process the JSON string properly" - its frontend problem.
|
|
Here is discussion regarding JSON metadata code-423n4/org#109 |
|
Thanks everyone for providing their input on this one.
|
But we talk about blockchain project, so user's could and must verify properties of pieces, to whom they give their votes. If user dont check all data of piece, its user mistake and isnt contract issue |
That's exactly the issue, the initial |
But user can see all data of piece before vote for this vote. And user can understand, that it is bad piece with bad code inside.. |
|
I understand both sides. On the one hand, users have to be careful and review their actions responsibly, but on the other hand it's any protocol's duty to protect users to a certain degree (example: slippage control). |
|
Underatand you, thank you for response. |
Lines of code
https://github.com/code-423n4/2023-12-revolutionprotocol/blob/d42cc62b873a1b2b44f57310f9d4bbfdd875e8d6/packages/revolution/src/CultureIndex.sol#L209
https://github.com/code-423n4/2023-12-revolutionprotocol/blob/d42cc62b873a1b2b44f57310f9d4bbfdd875e8d6/packages/revolution/src/VerbsToken.sol#L193
Vulnerability details
Impact
CultureIndex.createPiece()function doesn't sanitize malicious charcacters inmetadata.imageandmetadata.animationUrl, which would causeVerbsToken.tokenURI()suffering various JSON injection attack vectors.If the front end APP doesn't process the JSON string properly, such as using
eval()to parse token URI, then any malicious code can be executed in the front end. Obviously, funds in users' connected wallet, such as Metamask, might be stolen in this case.Even while the front end processes securely, such as using the standard builtin
JSON.parse()to read URI. Adversary can still exploit this vulnerability to replace art piece image/animation with arbitrary other ones after voting stage completed.That is the final metadata used by the NFT (VerbsToken) is not the art piece users vote. This attack could be benefit to attackers, such as creating NFTs containing same art piece data with existing high price NFTs. And this attack could also make the project sufferring legal risks, such as creating NFTs with violence or pornography images.
more reference: https://www.comparitech.com/net-admin/json-injection-guide/
Proof of Concept
As shown of
createPiece()function, there is no check ifmetadata.imageandmetadata.animationUrlcontain malicious charcacters, such as",:and,.Adverary can exploit this to make
VerbsToken.tokenURI()to return various malicious JSON objects to front end APP.For example, if attacker submit the following metadata
During voting stage, front end gets
imagefield byCultureIndex.pieces[pieceId].metadata.image, which isipfs://realMonaLisa. But, after voting complete, art piece is minted toVerbsTokenNFT. Now, front end would queryVerbsToken.tokenURI(tokenId)to get base64 encoded metadata, which would beIn the front end, we use
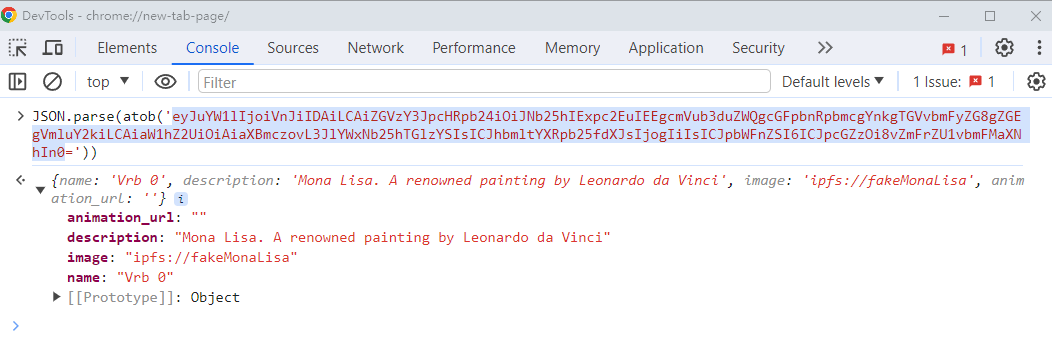
JSON.parse()to parse the above data, we getimageasipfs://fakeMonaLisa.Image link: https://gist.github.com/assets/68863517/d769d7ac-db02-4e3b-94d2-dfaf3752b763
Below is the full coded PoC:
And, test logs:
Tools Used
Manually review
Recommended Mitigation Steps
Sanitize input data according: https://github.com/OWASP/json-sanitizer
Assessed type
Invalid Validation
The text was updated successfully, but these errors were encountered: